Interception plays a crucial role in various fields such as telecommunications, cybersecurity, and sports, where it involves capturing or interrupting signals, messages, or moves before they reach their intended target. Understanding interception techniques and their implications can help enhance security measures, improve game strategies, or safeguard sensitive information. Explore the full article to discover how interception impacts your world and what you can do to stay ahead.
Table of Comparison
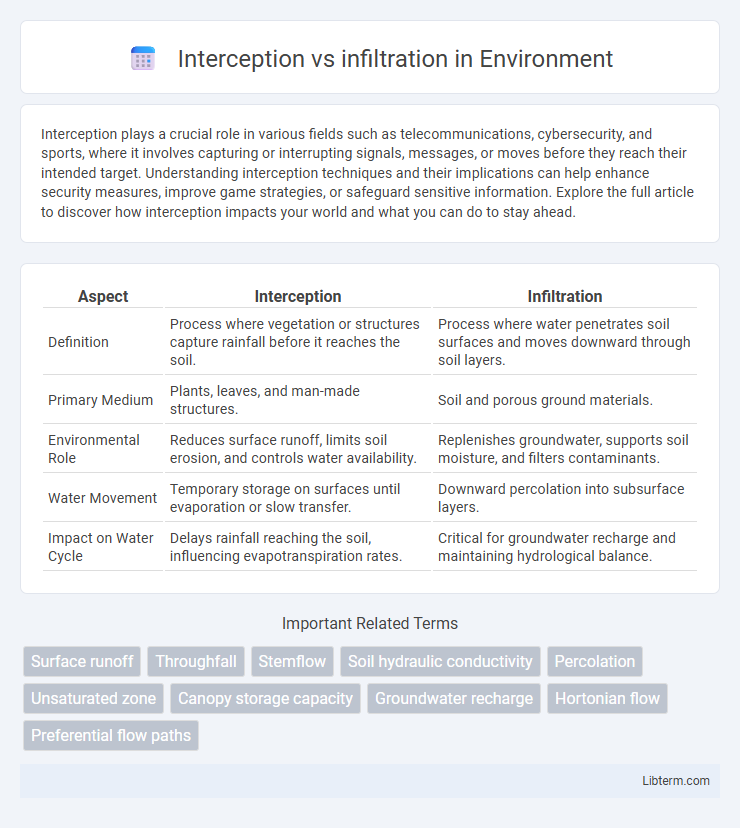
| Aspect | Interception | Infiltration |
|---|---|---|
| Definition | Process where vegetation or structures capture rainfall before it reaches the soil. | Process where water penetrates soil surfaces and moves downward through soil layers. |
| Primary Medium | Plants, leaves, and man-made structures. | Soil and porous ground materials. |
| Environmental Role | Reduces surface runoff, limits soil erosion, and controls water availability. | Replenishes groundwater, supports soil moisture, and filters contaminants. |
| Water Movement | Temporary storage on surfaces until evaporation or slow transfer. | Downward percolation into subsurface layers. |
| Impact on Water Cycle | Delays rainfall reaching the soil, influencing evapotranspiration rates. | Critical for groundwater recharge and maintaining hydrological balance. |
Understanding Interception and Infiltration: Key Differences
Interception involves the capture of precipitation by plant surfaces before it reaches the ground, typically influenced by vegetation type and canopy structure, which reduces surface runoff and soil erosion. Infiltration refers to the process where water penetrates the soil surface and moves into the subsurface layers, governed by soil texture, moisture content, and compaction levels, directly impacting groundwater recharge and availability. Understanding the differences between interception and infiltration is crucial for effective water management, ecosystem sustainability, and designing strategies to mitigate flooding and improve soil health.
Definitions: What Is Interception?
Interception refers to the process of detecting, capturing, or halting data, communications, or signals before they reach their intended destination, often used in cybersecurity, law enforcement, or military applications. It involves actions such as monitoring network traffic, wiretapping phone calls, or seizing messages to prevent unauthorized or harmful exchanges. Interception plays a crucial role in preventing security breaches, unauthorized access, and intelligence gathering by adversaries.
Definitions: What Is Infiltration?
Infiltration refers to the covert penetration of a secure area or system by unauthorized individuals or entities to gather intelligence or conduct operations without detection. It involves bypassing physical or digital defenses, often blending with legitimate users or personnel to avoid raising suspicion. Unlike interception, which captures or monitors data or communications externally, infiltration entails direct internal access and manipulation within the targeted environment.
Mechanisms of Interception in Security Contexts
Interception in security contexts involves detecting, capturing, and analyzing unauthorized data or communication flows through mechanisms such as network sniffers, man-in-the-middle attacks, and signal jamming. These interception techniques leverage protocol vulnerabilities, real-time monitoring tools, and cryptographic weaknesses to access sensitive information before it reaches its intended recipient. Effective interception defenses include encryption, intrusion detection systems, and secure communication protocols that mitigate data exposure risks in cyber and physical security environments.
Infiltration Techniques and Approaches
Infiltration techniques utilize covert methods such as social engineering, phishing, and malware deployment to gain unauthorized access to networks or systems, often bypassing traditional security measures. Approaches include exploiting vulnerabilities in software, leveraging insider threats, and establishing persistent backdoors for continuous control. Effective infiltration requires detailed reconnaissance, stealthy execution, and adaptive tactics to evade detection by security protocols.
Real-World Examples of Interception
Interception involves the act of capturing or seizing communications or information as it travels between parties, with real-world examples including the NSA's PRISM program which intercepted internet data from major tech companies, and the interception of encrypted messages by intelligence agencies during the Cuban Missile Crisis. Military operations often rely on interception to disrupt enemy communications, as seen in World War II's Operation Ultra, where Allied forces decrypted and intercepted German Enigma codes. Corporate espionage also uses interception techniques to monitor competitors' confidential communications and gain strategic advantages.
Real-World Examples of Infiltration
Infiltration involves covertly entering an organization or system to gather intelligence or sabotage operations, as seen in the CIA's deep-cover agents infiltrating hostile regimes during the Cold War. Unlike interception, which passively captures communications, infiltration requires establishing trust and integration, exemplified by the FBI's use of informants within criminal gangs to dismantle drug networks. These real-world examples highlight infiltration's strategic value in gaining inside access beyond mere surveillance.
Comparing Effectiveness: Interception vs Infiltration
Interception primarily targets threats by detecting and blocking them before they penetrate security perimeters, offering immediate threat neutralization and reducing system exposure. Infiltration focuses on identifying threats that successfully bypass initial defenses, enabling detailed monitoring and analysis of malicious activities within the network for long-term mitigation. Comparing effectiveness, interception excels in preventative security by stopping threats early, while infiltration provides critical insights into advanced persistent threats that evade frontline defenses.
Impact on Cybersecurity: Risks and Mitigations
Interception involves unauthorized access to data during transmission, posing risks such as data breaches and information leakage that compromise confidentiality and integrity. Infiltration refers to adversaries penetrating network defenses to establish persistent access, escalating the risk of advanced persistent threats (APTs) and internal sabotage. Effective cybersecurity mitigations include strong encryption protocols, multi-factor authentication, continuous network monitoring, and endpoint detection and response (EDR) systems to detect and prevent both interception and infiltration attacks.
Choosing Between Interception and Infiltration Strategies
Choosing between interception and infiltration strategies depends on the specific operational goals and security context. Interception focuses on detecting and blocking threats before they reach critical assets, making it ideal for perimeter defense and real-time threat mitigation. Infiltration, on the other hand, involves penetrating an adversary's network to gather intelligence or disrupt operations internally, which requires stealth, advanced access techniques, and deep knowledge of target systems.
Interception Infographic
 libterm.com
libterm.com