Firewall protection is essential for safeguarding your network from unauthorized access, cyber threats, and data breaches by monitoring and controlling incoming and outgoing traffic based on predefined security rules. Implementing a robust firewall enhances your system's defense against malware, hackers, and other cyber attacks that could compromise sensitive information. Explore the rest of the article to learn how firewall protection can strengthen your cybersecurity strategy effectively.
Table of Comparison
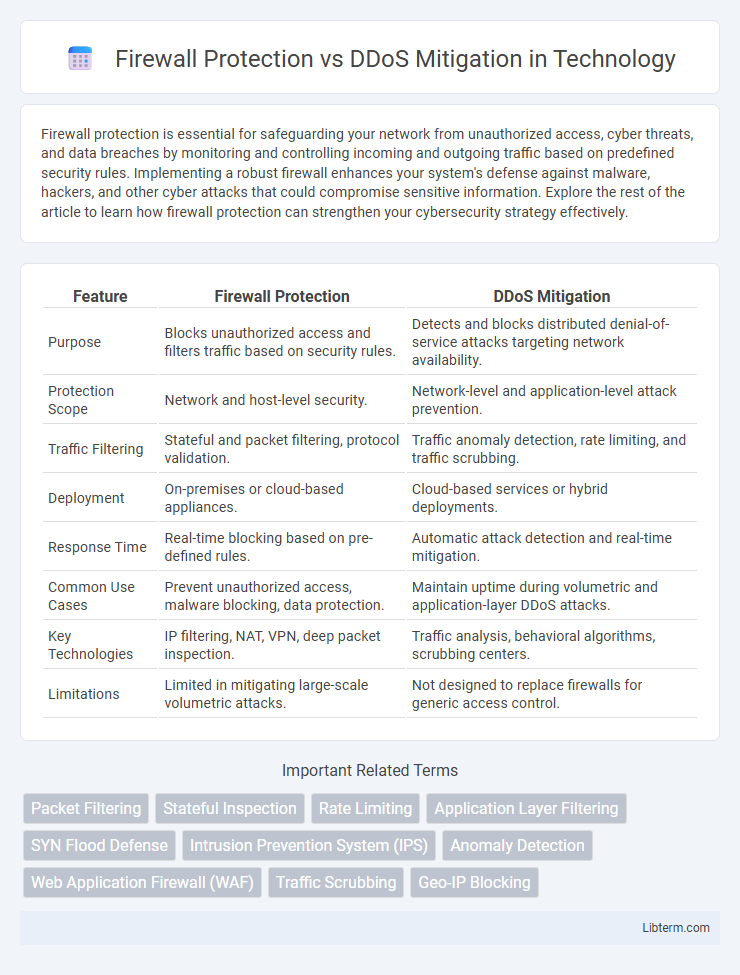
| Feature | Firewall Protection | DDoS Mitigation |
|---|---|---|
| Purpose | Blocks unauthorized access and filters traffic based on security rules. | Detects and blocks distributed denial-of-service attacks targeting network availability. |
| Protection Scope | Network and host-level security. | Network-level and application-level attack prevention. |
| Traffic Filtering | Stateful and packet filtering, protocol validation. | Traffic anomaly detection, rate limiting, and traffic scrubbing. |
| Deployment | On-premises or cloud-based appliances. | Cloud-based services or hybrid deployments. |
| Response Time | Real-time blocking based on pre-defined rules. | Automatic attack detection and real-time mitigation. |
| Common Use Cases | Prevent unauthorized access, malware blocking, data protection. | Maintain uptime during volumetric and application-layer DDoS attacks. |
| Key Technologies | IP filtering, NAT, VPN, deep packet inspection. | Traffic analysis, behavioral algorithms, scrubbing centers. |
| Limitations | Limited in mitigating large-scale volumetric attacks. | Not designed to replace firewalls for generic access control. |
Introduction to Firewall Protection and DDoS Mitigation
Firewall protection establishes a secure barrier between internal networks and external threats by monitoring and controlling incoming and outgoing network traffic based on predetermined security rules. DDoS mitigation specifically targets and neutralizes Distributed Denial of Service attacks, which aim to overwhelm network resources and disrupt service availability. Both technologies are essential components of a comprehensive cybersecurity strategy, addressing different aspects of network defense and ensuring system integrity and uptime.
Understanding the Basics: What Is Firewall Protection?
Firewall protection is a cybersecurity measure that monitors and controls incoming and outgoing network traffic based on predetermined security rules. It acts as a barrier between trusted internal networks and untrusted external networks, filtering potentially harmful data to prevent unauthorized access and cyber threats. Unlike DDoS mitigation, which specifically targets and defends against distributed denial-of-service attacks, firewall protection provides a broader scope of network security by managing general traffic and blocking malicious exploits.
What Is DDoS Mitigation? Core Concepts Explained
DDoS mitigation involves strategies and technologies designed to detect, absorb, and deflect distributed denial-of-service attacks that flood a network with excessive traffic to disrupt service availability. Unlike traditional firewall protection that filters traffic based on predetermined rules and signatures, DDoS mitigation uses advanced traffic analysis, rate limiting, and behavioral algorithms to differentiate legitimate users from malicious bots. Key components include traffic scrubbing centers, real-time monitoring, and scalable cloud-based defenses that ensure continuous network uptime during large-scale traffic surges.
Key Differences: Firewall vs DDoS Mitigation
Firewall protection primarily filters incoming and outgoing traffic based on predefined security rules to prevent unauthorized access and attacks. DDoS mitigation specifically targets and neutralizes distributed denial-of-service attacks by detecting abnormal traffic patterns and absorbing or blocking malicious data floods. Firewalls offer broad network defense against various cyber threats, while DDoS mitigation provides specialized defense focused on maintaining service availability during volumetric attacks.
How Firewalls Protect Networks from Threats
Firewalls protect networks from threats by monitoring and controlling incoming and outgoing traffic based on predefined security rules, effectively blocking unauthorized access and malicious data packets. They inspect traffic at various layers, filtering out viruses, malware, and exploit attempts before they penetrate the network perimeter. Unlike DDoS mitigation systems that specifically target traffic floods, firewalls provide a broader range of protections, including intrusion prevention and application-level filtering.
Limitations of Traditional Firewall Solutions
Traditional firewall protection primarily focuses on filtering unauthorized access based on IP addresses, ports, and protocols, lacking the capacity to handle the volumetric traffic surges caused by Distributed Denial of Service (DDoS) attacks. Firewalls often struggle with stateful inspection overload during large-scale DDoS incidents, leading to potential service outages or degraded performance. Unlike specialized DDoS mitigation services, traditional firewalls cannot differentiate between legitimate traffic and attack traffic at high speeds, making them insufficient for comprehensive defense against sophisticated, high-volume DDoS threats.
DDoS Attacks: How They Bypass Firewalls
DDoS attacks bypass firewalls by overwhelming network resources with massive traffic volumes, exploiting the limitations of firewall rules focused on legitimate traffic filtering rather than large-scale traffic floods. Firewalls primarily inspect packet headers and basic protocols, allowing sophisticated DDoS attacks such as application layer and volumetric floods to slip through undetected. Effective DDoS mitigation employs specialized traffic analysis, rate limiting, and behavior-based anomaly detection to identify and block malicious traffic before it impacts network performance.
Advanced DDoS Mitigation Techniques and Tools
Advanced DDoS mitigation techniques prioritize real-time traffic analysis, behavior-based anomaly detection, and automated filtering to identify and neutralize malicious traffic before it impacts network performance. Tools such as cloud-based scrubbing centers, AI-powered threat intelligence platforms, and rate limiting protocols significantly enhance the ability to absorb and mitigate volumetric and application-layer attacks, providing robust protection beyond traditional firewall capabilities. Integrating these specialized DDoS defenses with firewall protection ensures comprehensive security by combining perimeter control with dynamic attack mitigation strategies.
Choosing the Right Solution: Firewall, DDoS Mitigation, or Both?
Firewall protection provides robust security by filtering unauthorized access and blocking malicious traffic based on predefined rules, ideal for preventing intrusion attempts and malware attacks. DDoS mitigation specifically targets large-scale, volumetric attacks designed to overwhelm network resources, using traffic analysis and scrubbing techniques to maintain service availability. Choosing the right solution depends on threat profile and network requirements; deploying both firewall and DDoS mitigation ensures comprehensive defense, combining access control with resilience against distributed denial-of-service attacks.
Best Practices for Comprehensive Network Security
Firewall protection establishes a baseline defense by filtering unauthorized access and blocking malicious traffic at the network perimeter, while DDoS mitigation specifically targets and absorbs large-scale traffic floods to maintain service availability. Best practices for comprehensive network security involve integrating stateful firewalls with advanced DDoS mitigation tools that leverage traffic analysis, rate limiting, and anomaly detection to preemptively identify and neutralize cyber threats. Employing continuous monitoring, regular rule updates, and multi-layered security architecture ensures robust protection against both infiltration attempts and volumetric attacks.
Firewall Protection Infographic
 libterm.com
libterm.com