Secure key storage is essential for protecting sensitive information and ensuring the integrity of cryptographic systems. Utilizing hardware security modules (HSMs) or encrypted software vaults significantly reduces the risk of unauthorized access and data breaches. Discover effective strategies to safeguard your keys and enhance your overall security by reading the full article.
Table of Comparison
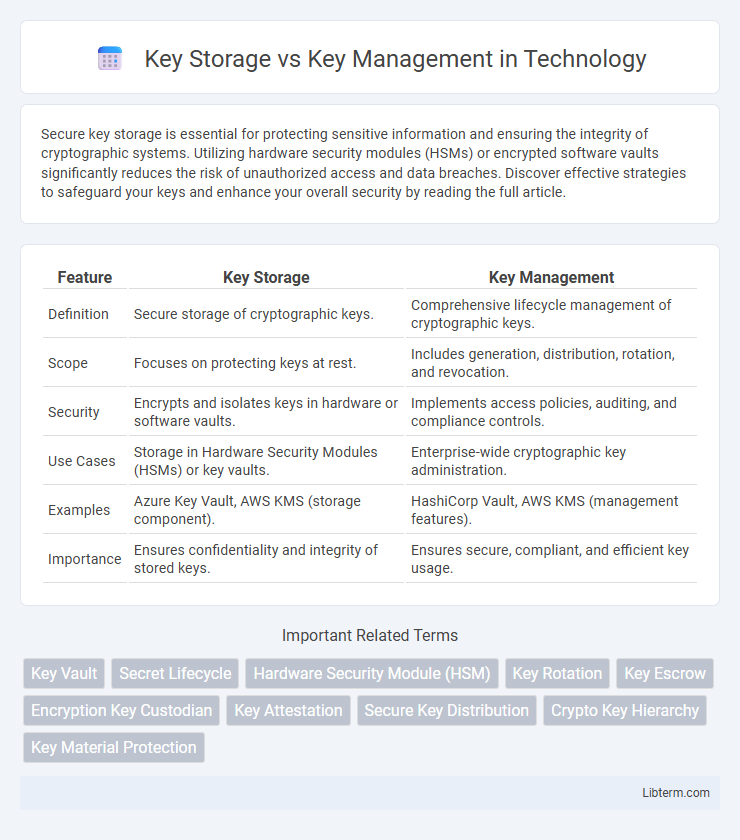
| Feature | Key Storage | Key Management |
|---|---|---|
| Definition | Secure storage of cryptographic keys. | Comprehensive lifecycle management of cryptographic keys. |
| Scope | Focuses on protecting keys at rest. | Includes generation, distribution, rotation, and revocation. |
| Security | Encrypts and isolates keys in hardware or software vaults. | Implements access policies, auditing, and compliance controls. |
| Use Cases | Storage in Hardware Security Modules (HSMs) or key vaults. | Enterprise-wide cryptographic key administration. |
| Examples | Azure Key Vault, AWS KMS (storage component). | HashiCorp Vault, AWS KMS (management features). |
| Importance | Ensures confidentiality and integrity of stored keys. | Ensures secure, compliant, and efficient key usage. |
Introduction to Key Storage and Key Management
Key storage refers to the secure saving of cryptographic keys in physical or digital environments, ensuring keys are protected from unauthorized access and loss. Key management encompasses the entire lifecycle of cryptographic keys, including generation, distribution, storage, rotation, and destruction, aiming to maintain data confidentiality and integrity. Effective key management solutions integrate robust key storage mechanisms with policies and procedures to safeguard sensitive information in cybersecurity frameworks.
Defining Key Storage: What It Is and How It Works
Key storage refers to the secure retention of cryptographic keys within hardware devices or software systems designed to protect against unauthorized access and tampering. It involves the use of specialized hardware security modules (HSMs), secure enclaves, or encrypted databases to ensure keys remain confidential and integral throughout their lifecycle. Effective key storage safeguards key material from theft, loss, or exposure, enabling reliable cryptographic operations and data protection.
Understanding Key Management: Scope and Functions
Key management encompasses the processes and technologies involved in the generation, distribution, storage, rotation, and destruction of cryptographic keys to ensure data security and integrity. It provides a comprehensive framework for controlling access to keys, enforcing policies, and maintaining audit trails to prevent unauthorized use or compromise. Unlike simple key storage, key management systems integrate lifecycle management and operational controls essential for maintaining strong encryption practices across organizations.
Key Storage vs Key Management: Core Differences
Key storage involves securely storing cryptographic keys in hardware or software to prevent unauthorized access, often using hardware security modules (HSMs) or encrypted vaults. Key management encompasses the entire lifecycle of cryptographic keys, including generation, distribution, rotation, revocation, and auditing, ensuring effective governance and compliance. The core difference lies in key storage focusing solely on safeguarding keys, while key management integrates storage with operational controls and policies for robust security.
Security Implications of Key Storage
Key Storage involves physically or digitally storing cryptographic keys, often in hardware security modules (HSMs) or secure vaults to prevent unauthorized access and ensure data integrity. The main security implications include risks of key exposure from inadequate protection, susceptibility to insider threats, and vulnerabilities to physical theft or cyber-attacks. Effective key storage solutions must implement strong encryption, access controls, and regular audits to maintain confidentiality and prevent key compromise.
The Role of Key Management in Data Protection
Key management involves the generation, distribution, storage, use, and destruction of cryptographic keys, playing a critical role in maintaining data confidentiality and integrity. Effective key management ensures that encryption keys are securely handled throughout their lifecycle, preventing unauthorized access to sensitive information. Unlike simple key storage, which only refers to holding keys, comprehensive key management provides policies and controls that enforce security standards essential for robust data protection frameworks.
Common Use Cases for Key Storage Solutions
Key storage solutions are commonly used for securely storing cryptographic keys in scenarios such as data encryption, digital signatures, and secure access control, where the primary focus is on safeguarding key confidentiality and availability. Key management extends beyond storage by providing lifecycle management features, including key generation, rotation, distribution, and revocation, essential for compliance and enterprise security frameworks. Industries like finance, healthcare, and cloud computing heavily rely on key storage solutions to protect sensitive information and ensure regulatory adherence.
Advanced Features of Key Management Systems
Key Management Systems (KMS) provide advanced features such as automated key rotation, granular access controls, and comprehensive auditing capabilities that enhance security beyond simple key storage solutions. These systems support integration with hardware security modules (HSMs) and cloud environments to enforce encryption policies and secure key lifecycle management. Real-time monitoring and compliance reporting within KMS enable organizations to meet regulatory requirements while minimizing risks associated with key compromise.
Choosing Between Key Storage and Key Management
Choosing between key storage and key management depends on the complexity of cryptographic needs and security requirements. Key storage involves securely saving cryptographic keys in hardware or software solutions, ideal for simple encryption tasks with minimal key lifecycle operations. Key management encompasses the generation, distribution, rotation, and destruction of keys, providing comprehensive control necessary for enterprise-level security and regulatory compliance.
Best Practices for Secure Key Handling
Best practices for secure key handling emphasize distinguishing between key storage and key management, where key storage involves securely saving cryptographic keys using hardware security modules (HSMs) or encrypted vaults to prevent unauthorized access. Key management encompasses the entire lifecycle of keys, including generation, distribution, rotation, and destruction, with strict policies ensuring compliance and minimizing risk exposure. Implementing role-based access controls, regular audits, and automated key rotation schedules enhances security and maintains integrity throughout key handling processes.
Key Storage Infographic
 libterm.com
libterm.com