TPM, or Total Productive Maintenance, is a strategic approach focused on maximizing equipment efficiency by involving all employees in proactive maintenance activities. This methodology enhances productivity, reduces downtime, and fosters a culture of continuous improvement within your organization. Explore the article further to understand how implementing TPM can transform your maintenance processes and boost operational success.
Table of Comparison
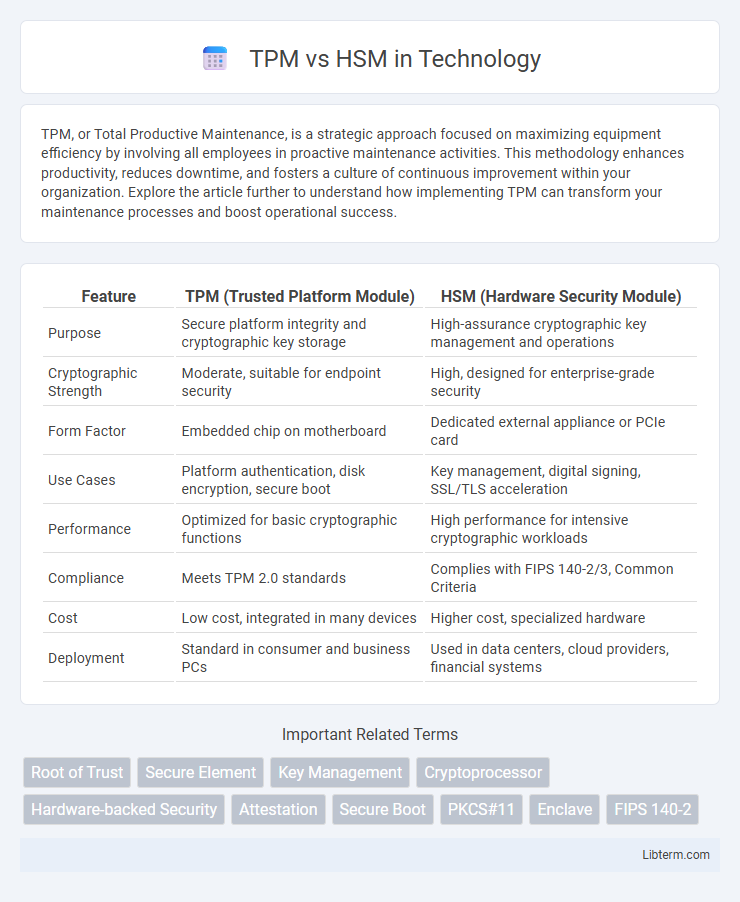
| Feature | TPM (Trusted Platform Module) | HSM (Hardware Security Module) |
|---|---|---|
| Purpose | Secure platform integrity and cryptographic key storage | High-assurance cryptographic key management and operations |
| Cryptographic Strength | Moderate, suitable for endpoint security | High, designed for enterprise-grade security |
| Form Factor | Embedded chip on motherboard | Dedicated external appliance or PCIe card |
| Use Cases | Platform authentication, disk encryption, secure boot | Key management, digital signing, SSL/TLS acceleration |
| Performance | Optimized for basic cryptographic functions | High performance for intensive cryptographic workloads |
| Compliance | Meets TPM 2.0 standards | Complies with FIPS 140-2/3, Common Criteria |
| Cost | Low cost, integrated in many devices | Higher cost, specialized hardware |
| Deployment | Standard in consumer and business PCs | Used in data centers, cloud providers, financial systems |
Introduction to TPM and HSM
Trusted Platform Module (TPM) is a specialized hardware chip integrated into computers to securely store cryptographic keys, ensuring platform integrity and enabling hardware-based security functions. Hardware Security Module (HSM) is a dedicated physical device designed to manage digital keys, perform cryptographic operations, and protect sensitive data in enterprise environments. Both TPM and HSM provide robust hardware-based security, but TPM is typically embedded in consumer devices, while HSMs are used in high-security applications like data centers and financial institutions.
Definition and Core Functions of TPM
Trusted Platform Module (TPM) is a specialized hardware chip designed to secure hardware through integrated cryptographic keys, primarily managing platform integrity, secure boot processes, and encryption key storage. Core functions of TPM include generating and storing cryptographic keys, performing platform integrity measurements, and facilitating secure authentication mechanisms. Unlike Hardware Security Modules (HSMs), which focus on broader cryptographic processing in enterprise environments, TPMs are embedded in personal computers and devices to ensure system integrity and trustworthiness.
Definition and Core Functions of HSM
Hardware Security Modules (HSMs) are dedicated physical devices designed to generate, protect, and manage cryptographic keys with high security and compliance standards. Unlike Trusted Platform Modules (TPMs), which provide hardware-based security for individual devices primarily focusing on platform integrity and secure boot processes, HSMs offer robust cryptographic processing capabilities, including secure key storage, encryption, decryption, and digital signing within a tamper-resistant environment. Core functions of HSMs include secure key lifecycle management, hardware-accelerated cryptographic operations, and enforcing strict access controls to ensure the highest level of data protection for enterprise and cloud infrastructures.
Key Differences Between TPM and HSM
Trusted Platform Module (TPM) is a dedicated microcontroller designed to secure hardware through integrated cryptographic keys, primarily used in personal computers and embedded systems, whereas Hardware Security Module (HSM) is a physical device that provides advanced cryptographic key management and high-performance encryption, commonly deployed in enterprise environments and data centers for scalable security. TPMs offer device-specific identity and integrity measurement with limited processing power, while HSMs support extensive cryptographic operations, multi-user access, and compliance with stringent security standards like FIPS 140-2. The key differences lie in their scope of use, cryptographic capability, and level of security management, with TPMs focusing on device-level protection and HSMs enabling comprehensive key lifecycle management and high-throughput cryptographic processing.
Use Cases for TPM in Modern Security
Trusted Platform Modules (TPM) are widely utilized for hardware-based cryptographic operations, such as secure key storage, device authentication, and platform integrity verification, making them essential in securing personal computers, laptops, and IoT devices. TPMs enable trusted boot processes by ensuring firmware and software integrity, which protects against rootkits and bootkits in enterprise environments. Their integration with operating systems like Windows and Linux supports features like disk encryption (e.g., BitLocker) and secure credential storage, enhancing endpoint security and compliance with regulatory standards.
Use Cases for HSM in Enterprise Environments
Hardware Security Modules (HSMs) are essential in enterprise environments for managing cryptographic keys, securing digital identities, and ensuring compliance with stringent data protection regulations like GDPR and HIPAA. Unlike TPMs, which are primarily embedded in devices for platform integrity, HSMs provide scalable, high-performance encryption services for applications such as SSL/TLS acceleration, database encryption, and blockchain key management. Enterprises rely on HSMs to safeguard sensitive operations in cloud infrastructures, payment processing systems, and certificate authorities, offering robust protection against key theft and tampering.
Security Features Compared: TPM vs HSM
Trusted Platform Module (TPM) offers hardware-based cryptographic functions such as secure key generation, storage, and platform integrity measurement, primarily designed for endpoint device security. Hardware Security Module (HSM) provides advanced cryptographic processing, secure key management, and high-assurance protection against tampering, typically used in data centers and cloud environments for enterprise-grade security. HSMs generally deliver higher performance and scalability with stringent FIPS 140-2 or 140-3 certifications, whereas TPMs focus on device-level security compliance like ISO/IEC 11889 standards.
Performance and Scalability Considerations
TPMs (Trusted Platform Modules) offer hardware-based security with limited processing power, making them suitable for endpoint protection but less effective for high-throughput cryptographic operations. HSMs (Hardware Security Modules) are designed for intensive cryptographic workloads, delivering superior performance and scalability in enterprise environments requiring rapid key generation, encryption, and decryption. Large-scale deployments favor HSMs due to their ability to handle multiple simultaneous operations without compromising security or speed.
Cost Implications of TPM and HSM Solutions
TPM (Trusted Platform Module) solutions typically incur lower costs due to their integration into existing hardware and standardized functionality, making them suitable for mass deployment in consumer devices. HSM (Hardware Security Module) solutions involve higher upfront investment driven by specialized cryptographic hardware, enhanced performance, and robust security certifications essential for enterprise and cloud environments. Cost implications also include long-term maintenance and scalability expenses, with HSMs demanding greater operational budgets for secure management and compliance adherence.
Choosing Between TPM and HSM: Factors to Consider
Choosing between TPM (Trusted Platform Module) and HSM (Hardware Security Module) depends on the specific security requirements and use cases, as TPMs are ideal for individual device security and secure boot processes, while HSMs offer high-performance cryptographic processing for enterprise applications. Key factors include the level of cryptographic strength needed, scalability, budget constraints, compliance with industry standards, and the type of cryptographic operations such as key management or encryption/decryption workloads. Assessing deployment environment, performance needs, and integration capabilities ensures the right choice between TPM's embedded security and HSM's dedicated hardware protection.
TPM Infographic
 libterm.com
libterm.com