Eavesdropping involves secretly listening to private conversations without consent, often violating privacy laws and ethical standards. Understanding the risks and legal implications of eavesdropping can help you protect your personal communications and ensure respectful interactions. Explore the following article to learn more about how to safeguard your privacy from eavesdropping threats.
Table of Comparison
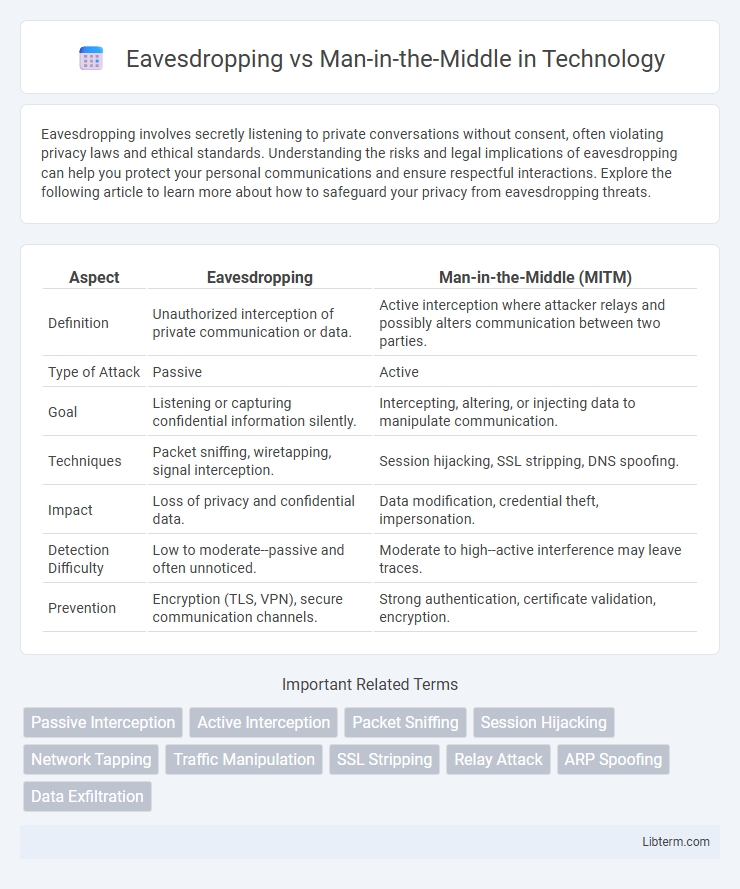
| Aspect | Eavesdropping | Man-in-the-Middle (MITM) |
|---|---|---|
| Definition | Unauthorized interception of private communication or data. | Active interception where attacker relays and possibly alters communication between two parties. |
| Type of Attack | Passive | Active |
| Goal | Listening or capturing confidential information silently. | Intercepting, altering, or injecting data to manipulate communication. |
| Techniques | Packet sniffing, wiretapping, signal interception. | Session hijacking, SSL stripping, DNS spoofing. |
| Impact | Loss of privacy and confidential data. | Data modification, credential theft, impersonation. |
| Detection Difficulty | Low to moderate--passive and often unnoticed. | Moderate to high--active interference may leave traces. |
| Prevention | Encryption (TLS, VPN), secure communication channels. | Strong authentication, certificate validation, encryption. |
Introduction to Eavesdropping and Man-in-the-Middle Attacks
Eavesdropping involves unauthorized interception of private communications or data transmission, often carried out passively to gather sensitive information without alerting the target. Man-in-the-Middle (MitM) attacks actively intercept and alter communication between two parties, enabling attackers to manipulate or steal data by impersonating one or both ends. Both techniques pose significant cybersecurity threats by compromising confidentiality and data integrity in digital communications.
Defining Eavesdropping in Cybersecurity
Eavesdropping in cybersecurity refers to the unauthorized interception and monitoring of private communications or data transmissions between parties. It involves attackers covertly capturing information such as emails, chat messages, or network traffic without altering the content. Unlike a man-in-the-middle attack, which actively manipulates the communication between two systems, eavesdropping is a passive form of cyberattack focused on data confidentiality violation.
Understanding Man-in-the-Middle Attacks
Man-in-the-middle (MITM) attacks involve an attacker secretly intercepting and potentially altering communication between two parties without their knowledge, unlike eavesdropping which solely involves passive listening. MITM attacks can compromise sensitive information by injecting malicious content or redirecting communication to fraudulent sites, posing significant risks to data integrity and confidentiality. Understanding the techniques used in MITM attacks, such as session hijacking and SSL stripping, is crucial for implementing robust cybersecurity measures like encryption and multi-factor authentication.
Key Differences Between Eavesdropping and MITM
Eavesdropping involves secretly listening to or intercepting communication without altering the message, primarily targeting data confidentiality, whereas Man-in-the-Middle (MITM) attacks actively intercept, modify, and relay communications to impersonate parties, compromising integrity and trust. Eavesdropping typically exploits passive vulnerabilities in networks, while MITM attacks require active manipulation and sophisticated techniques like session hijacking or SSL stripping. The fundamental difference lies in the attacker's interaction level: eavesdropping is passive and hidden, whereas MITM is active and intrusive, affecting both data authenticity and confidentiality.
Common Techniques Used in Eavesdropping
Common techniques used in eavesdropping include packet sniffing, where attackers capture data packets traveling over a network, and wiretapping, involving unauthorized interception of telephone or internet communications. Attackers may also leverage network protocol analyzers to monitor traffic, and employ software keyloggers for capturing keystrokes on targeted devices. Techniques like electromagnetic eavesdropping exploit signal emissions from hardware to gain access to sensitive information without physical contact.
Typical Methods of Man-in-the-Middle Attacks
Man-in-the-Middle (MITM) attacks commonly involve methods such as session hijacking, where attackers take over an active communication session between two parties, and SSL stripping, which downgrades HTTPS connections to unencrypted HTTP to intercept data. Attackers also use Wi-Fi eavesdropping on unsecured networks to insert themselves between users and the internet, capturing sensitive information transparently. These techniques exploit vulnerabilities in network protocols and encryption practices, enabling interception and alteration of data without detection.
Impact and Consequences of Eavesdropping
Eavesdropping compromises confidentiality by allowing unauthorized parties to intercept sensitive communications, leading to potential data breaches and identity theft. The impact includes loss of privacy, financial damages from stolen information, and erosion of trust in communication systems. Persistent eavesdropping can result in long-term security vulnerabilities, making it critical to implement robust encryption and secure network protocols.
Risks and Ramifications of Man-in-the-Middle Attacks
Man-in-the-Middle (MitM) attacks pose significant security risks by intercepting and altering communications between two parties without their knowledge, often leading to data breaches, identity theft, and financial loss. Unlike passive eavesdropping, MitM attacks actively manipulate transmitted information, enabling attackers to inject malware, steal sensitive credentials, and compromise system integrity. The ramifications include long-term damage to trust, regulatory penalties, and severe operational disruptions for both individuals and organizations.
Prevention and Protection Strategies
Eavesdropping prevention relies heavily on strong encryption protocols such as TLS and AES to secure communication channels and prevent unauthorized data interception. Man-in-the-Middle (MitM) attack protection involves the use of mutual authentication methods, including digital certificates and Public Key Infrastructure (PKI), to verify the identities of communicating parties and block attackers from inserting themselves into the communication stream. Implementing network security measures like VPNs, intrusion detection systems (IDS), and enforcing strict access controls further enhances defense against both eavesdropping and MitM threats.
Conclusion: Strengthening Cyber Defense Against Data Interception
Eavesdropping and Man-in-the-Middle attacks both exploit data interception but differ in complexity and impact, with Man-in-the-Middle posing a more sophisticated threat by actively altering communication. Strengthening cyber defense requires deploying robust encryption protocols such as TLS and using multi-factor authentication to safeguard data integrity and confidentiality. Continuous network monitoring combined with advanced intrusion detection systems enhances the identification and mitigation of interception attempts, reducing the risk of data breaches.
Eavesdropping Infographic
 libterm.com
libterm.com