A Denial-of-Service (DoS) attack disrupts the normal functioning of a network, service, or website by overwhelming it with excessive traffic or requests, rendering it unavailable to legitimate users. Cybercriminals often exploit vulnerabilities to launch these attacks, causing significant downtime and financial loss. Discover effective strategies to protect Your systems and mitigate the impact of DoS attacks by reading the rest of this article.
Table of Comparison
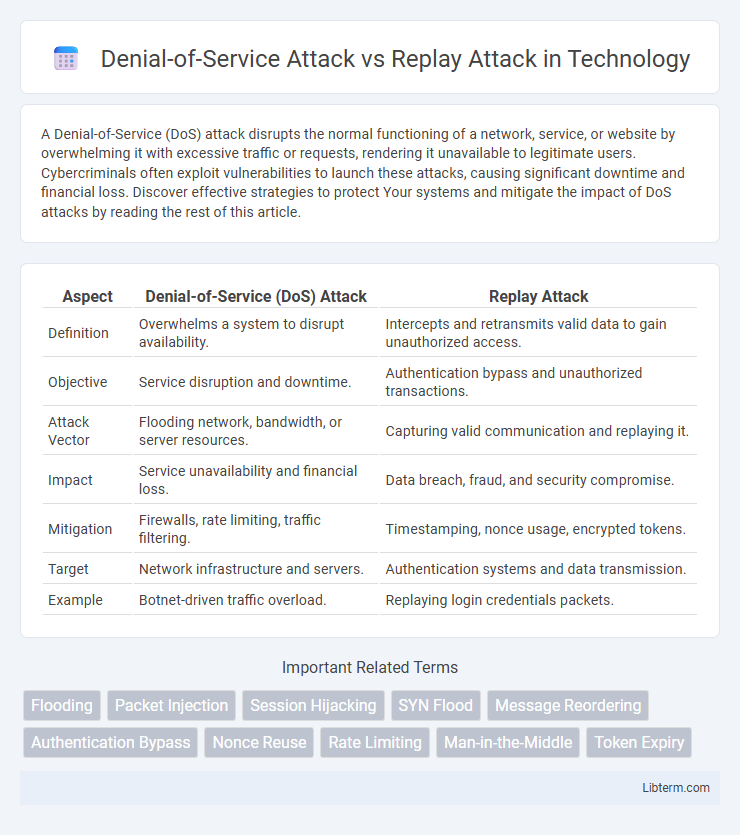
| Aspect | Denial-of-Service (DoS) Attack | Replay Attack |
|---|---|---|
| Definition | Overwhelms a system to disrupt availability. | Intercepts and retransmits valid data to gain unauthorized access. |
| Objective | Service disruption and downtime. | Authentication bypass and unauthorized transactions. |
| Attack Vector | Flooding network, bandwidth, or server resources. | Capturing valid communication and replaying it. |
| Impact | Service unavailability and financial loss. | Data breach, fraud, and security compromise. |
| Mitigation | Firewalls, rate limiting, traffic filtering. | Timestamping, nonce usage, encrypted tokens. |
| Target | Network infrastructure and servers. | Authentication systems and data transmission. |
| Example | Botnet-driven traffic overload. | Replaying login credentials packets. |
Introduction to Cyber Attacks
Denial-of-Service (DoS) attacks disrupt network services by overwhelming systems with excessive traffic, rendering resources unavailable to legitimate users. Replay attacks capture and retransmit valid data packets to gain unauthorized access or deceive systems into granting privileges. Both exploit vulnerabilities in network protocols but differ in their methods and objectives within cyber attack frameworks.
What is a Denial-of-Service (DoS) Attack?
A Denial-of-Service (DoS) attack is a cyberattack aimed at overwhelming a target system, network, or service with excessive traffic or resource requests, rendering it unavailable to legitimate users. This disruption is achieved by flooding the target with malicious requests that exhaust bandwidth, processing power, or memory, causing slowdowns or complete shutdowns. DoS attacks differ from replay attacks, which involve intercepting and retransmitting valid data to gain unauthorized access or deceive the system rather than causing service unavailability.
Key Methods Used in DoS Attacks
Denial-of-Service (DoS) attacks primarily use methods such as volume-based attacks, protocol attacks, and application layer attacks to overwhelm network resources and disrupt service availability. Common techniques include UDP floods, SYN floods, and HTTP GET/POST floods, which target bandwidth consumption, protocol state tables, or application processes respectively. Replay attacks, in contrast, involve capturing and retransmitting valid data packets to deceive authentication or transaction systems without directly exhausting resources.
Understanding Replay Attacks
Replay attacks involve intercepting and retransmitting valid data transmissions to gain unauthorized access or perform fraudulent actions, exploiting the lack of freshness verification in communication protocols. Unlike denial-of-service attacks, which aim to disrupt service availability, replay attacks target the integrity and authenticity of data by reusing previously captured valid messages. Effective defenses include timestamping, nonce usage, and cryptographic challenge-response mechanisms to ensure message freshness and prevent unauthorized retransmission.
Techniques Involved in Replay Attacks
Replay attacks exploit the technique of intercepting and retransmitting valid data packets to deceive a system into unauthorized operations. This involves capturing authentication tokens or data packets during legitimate transmissions and resending them to gain access or replicate transactions. Techniques such as timestamping, nonce usage, and sequence numbering are often implemented to counteract replay attack attempts by ensuring freshness and uniqueness of each communication.
Major Differences Between DoS and Replay Attacks
Denial-of-Service (DoS) attacks primarily aim to overwhelm a target system's resources or network bandwidth, rendering services unavailable to legitimate users, whereas Replay attacks focus on intercepting and retransmitting valid data packets to gain unauthorized access or repeat transactions. DoS attacks disrupt service availability by flooding the network, while Replay attacks exploit system authentication or communication protocols by duplicating legitimate communication. The core difference lies in the attack goals: DoS targets service disruption, while Replay targets data integrity and authentication processes.
Impact of DoS Attacks on Network Security
Denial-of-Service (DoS) attacks severely disrupt network availability by overwhelming resources, causing service outages and degrading legitimate user access. Unlike Replay Attacks, which focus on intercepting and retransmitting valid data to gain unauthorized access, DoS attacks directly target the infrastructure, leading to increased latency, packet loss, and potential system crashes. The impact on network security includes reduced operational efficiency, financial losses, and compromised trust in network reliability.
Effects of Replay Attacks on Data Integrity
Replay attacks compromise data integrity by retransmitting valid data transmissions, leading to unauthorized duplication or alteration of sensitive information. Unlike denial-of-service attacks that disrupt service availability, replay attacks manipulate the authenticity of data, causing trust issues and potential financial losses. The persistence of legitimate data packets in unauthorized contexts severely undermines the integrity and reliability of communication protocols.
Preventative Measures Against DoS and Replay Attacks
Preventative measures against Denial-of-Service (DoS) attacks include implementing robust firewalls, rate limiting, and traffic filtering to detect and block malicious traffic, coupled with the deployment of intrusion detection and prevention systems (IDPS) to monitor suspicious activities. For Replay attacks, employing cryptographic techniques such as using unique nonces, timestamps, and session tokens in authentication protocols ensures that intercepted data cannot be reused maliciously. Network administrators should also enforce strict access controls and conduct regular security audits to mitigate vulnerabilities that could be exploited by both DoS and replay attacks.
Conclusion: Securing Systems from DoS and Replay Threats
Securing systems from Denial-of-Service (DoS) and replay attacks requires a multi-layered approach involving robust network monitoring, rate limiting, and the use of anti-replay protocols such as timestamps and nonces. Implementing intrusion detection systems (IDS) alongside encryption methods like TLS can effectively mitigate the impact of DoS floods and prevent the reuse of intercepted data packets. Regular security audits and patch management further enhance resilience against these threats by identifying vulnerabilities before exploitation.
Denial-of-Service Attack Infographic
 libterm.com
libterm.com