Man-in-the-Browser attacks exploit vulnerabilities in web browsers by injecting malicious code to intercept and manipulate your online transactions without detection. These sophisticated threats often target banking and e-commerce sites, compromising sensitive information and facilitating unauthorized activities. Discover how to protect your digital security by reading the full article.
Table of Comparison
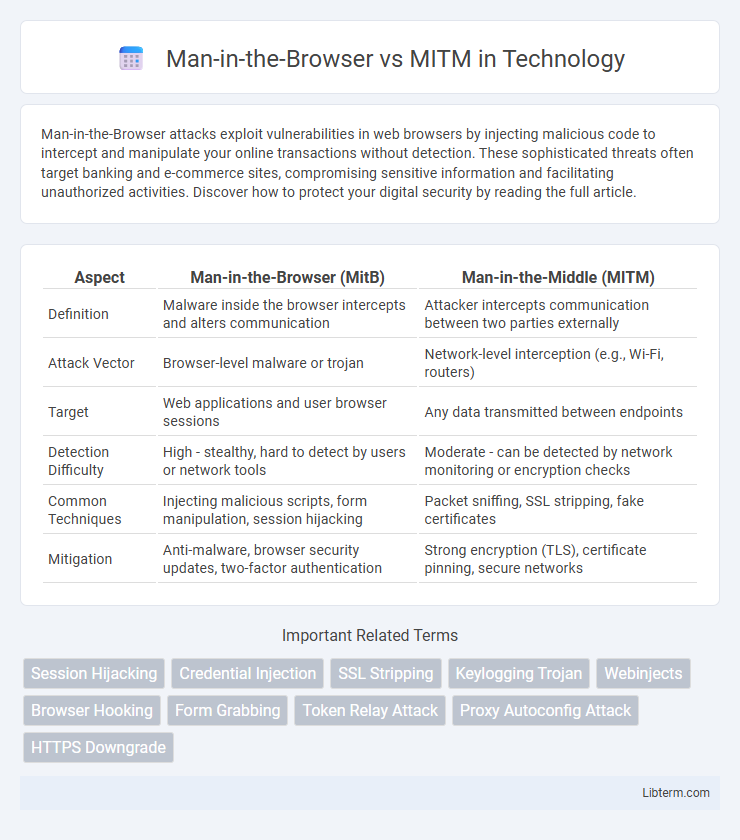
| Aspect | Man-in-the-Browser (MitB) | Man-in-the-Middle (MITM) |
|---|---|---|
| Definition | Malware inside the browser intercepts and alters communication | Attacker intercepts communication between two parties externally |
| Attack Vector | Browser-level malware or trojan | Network-level interception (e.g., Wi-Fi, routers) |
| Target | Web applications and user browser sessions | Any data transmitted between endpoints |
| Detection Difficulty | High - stealthy, hard to detect by users or network tools | Moderate - can be detected by network monitoring or encryption checks |
| Common Techniques | Injecting malicious scripts, form manipulation, session hijacking | Packet sniffing, SSL stripping, fake certificates |
| Mitigation | Anti-malware, browser security updates, two-factor authentication | Strong encryption (TLS), certificate pinning, secure networks |
Introduction to Online Threats: MITB and MITM
Man-in-the-Browser (MITB) and Man-in-the-Middle (MITM) attacks are sophisticated cyber threats targeting online communications to intercept and manipulate data. MITB involves malware infecting a user's browser to alter transactions in real-time, often bypassing conventional security measures, while MITM attacks intrude on the communication channel between two parties to eavesdrop or inject malicious content. Both types of attacks pose significant risks to online banking, e-commerce, and personal data security, emphasizing the need for robust cybersecurity defenses and user vigilance.
What is a Man-in-the-Browser (MITB) Attack?
A Man-in-the-Browser (MITB) attack involves malware that infects a user's web browser, enabling attackers to intercept and manipulate web transactions in real time without user awareness. Unlike traditional Man-in-the-Middle (MITM) attacks that intercept data between two endpoints on a network, MITB operates within the browser itself, targeting the communication between the user and the web application. MITB attacks are particularly dangerous in online banking and e-commerce, where they can alter transaction details or steal sensitive credentials.
What is a Man-in-the-Middle (MITM) Attack?
A Man-in-the-Middle (MITM) attack occurs when a cybercriminal intercepts communication between two parties to secretly eavesdrop or alter the exchanged information. Unlike Man-in-the-Browser (MitB) attacks that manipulate transactions within a compromised browser, MITM attacks typically exploit network vulnerabilities such as unsecured Wi-Fi or DNS spoofing. Understanding MITM attacks is crucial for implementing security measures like end-to-end encryption and secure authentication protocols.
Key Differences Between MITB and MITM
Man-in-the-Browser (MITB) attacks specifically target vulnerabilities within a user's browser by injecting malicious code through infected browser extensions or malware, enabling real-time manipulation of web transactions without detection. Man-in-the-Middle (MITM) attacks intercept and potentially alter communications between two parties over a network, often exploiting insecure Wi-Fi or compromised routers to eavesdrop or inject data. Key differences include the attack vector--MITB operates inside the client's browser environment while MITM manipulates data transmission between endpoints--and the scope, with MITB focusing on browser sessions and MITM affecting network communication channels.
Attack Vectors: How MITB and MITM Infiltrate Systems
Man-in-the-Browser (MITB) attacks exploit malware-infected browsers to intercept and manipulate data within a user's web session, often using trojans or malicious extensions to alter transactions unnoticed. Man-in-the-Middle (MITM) attacks infiltrate systems by intercepting communication between two parties through techniques like ARP spoofing, DNS poisoning, or rogue Wi-Fi hotspots to capture or modify data in transit. Both attack vectors leverage vulnerabilities in network protocols or endpoint security to evade detection and compromise sensitive information.
Common Targets and Real-World Examples
Man-in-the-Browser (MitB) attacks primarily target online banking platforms and e-commerce websites by infecting users' browsers with malware to intercept and manipulate transactions in real-time. Man-in-the-Middle (MITM) attacks often focus on unencrypted Wi-Fi networks and enterprise VPNs, capturing or altering data between two communicating parties without their knowledge. Notable MitB incidents include the Zeus Trojan campaign, while famous MITM cases involve the 2013 Target breach exploiting network vulnerabilities.
Detection Methods for MITB vs MITM
Detection methods for Man-in-the-Browser (MITB) attacks primarily involve behavioral analysis using endpoint security solutions that monitor unusual browser activity or unauthorized transaction modifications, often leveraging machine learning algorithms to identify anomalies. In contrast, Man-in-the-Middle (MITM) attack detection relies on network-based techniques such as inspecting SSL/TLS certificate validity, monitoring for ARP spoofing, or detecting SSL stripping attempts through network intrusion detection systems (NIDS). Endpoint-focused tools excel in MITB detection by analyzing code injection and API hooking within browsers, while MITM detection depends on network traffic analysis and cryptographic validation to identify interception and data manipulation at the communication layer.
Prevention Strategies: Protecting Against Both Attacks
Effective prevention strategies against Man-in-the-Browser (MitB) and Man-in-the-Middle (MITM) attacks emphasize multi-factor authentication (MFA), end-to-end encryption, and regular software updates to patch vulnerabilities exploited by attackers. Implementing robust endpoint security with anti-malware solutions and behavioral analysis can detect and block browser-based Trojans characteristic of MitB attacks, while secure SSL/TLS protocols and certificate pinning reduce MITM risks by validating server authenticity. User education on phishing awareness and cautious handling of public Wi-Fi networks further strengthens defenses against these sophisticated cyber threats.
Impact on Financial Transactions and E-Commerce
Man-in-the-Browser (MitB) attacks manipulate web sessions within the browser to intercept and alter financial transactions in real-time, often bypassing traditional security measures and leading to unauthorized fund transfers or data theft. Man-in-the-Middle (MITM) attacks intercept communication between users and e-commerce platforms, enabling attackers to capture login credentials, payment information, and sensitive transaction data, impacting transaction integrity and confidentiality. Both attack vectors pose significant risks to financial transactions by compromising authentication and transaction data, increasing fraud losses and undermining trust in online banking and e-commerce systems.
Future Trends and Evolving Threat Landscapes
Emerging trends in Man-in-the-Browser (MitB) and Man-in-the-Middle (MITM) attacks reveal a shift towards more sophisticated, AI-driven malware capable of evading traditional detection techniques by exploiting browser vulnerabilities and encrypted communications. The proliferation of Internet of Things (IoT) devices and cloud-based applications expands attack surfaces, increasing the risk of interception and manipulation of sensitive data in real-time. Future defense strategies emphasize advanced threat intelligence, behavioral analytics, and zero-trust architectures to counteract evolving tactics in these cyberattack vectors.
Man-in-the-Browser Infographic
 libterm.com
libterm.com