True random refers to unpredictability generated by natural physical processes rather than algorithms. This randomness is crucial for secure cryptographic systems and accurate scientific simulations, ensuring outcomes cannot be anticipated or replicated. Discover how true random sources impact your data security and technology in the full article.
Table of Comparison
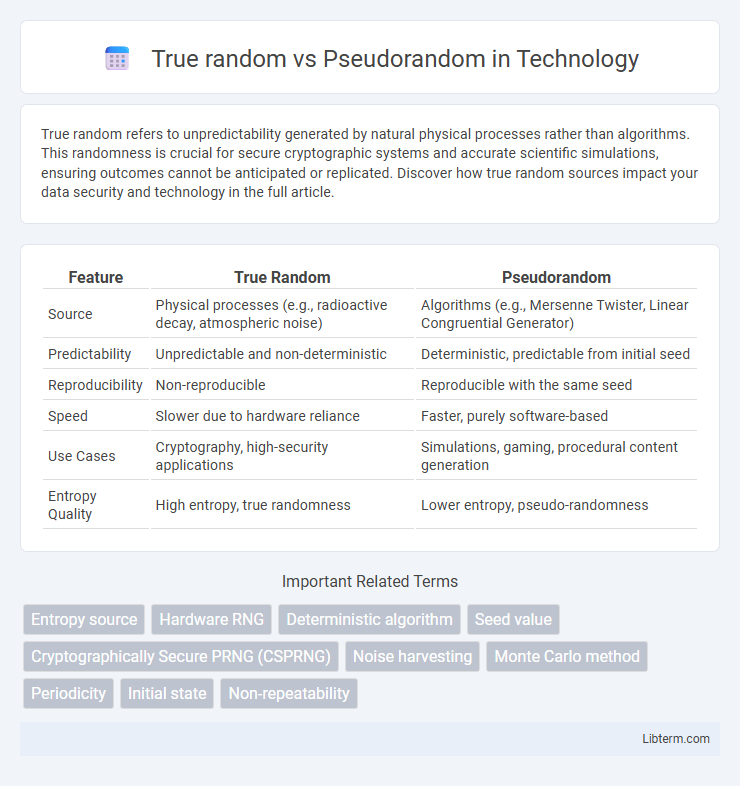
| Feature | True Random | Pseudorandom |
|---|---|---|
| Source | Physical processes (e.g., radioactive decay, atmospheric noise) | Algorithms (e.g., Mersenne Twister, Linear Congruential Generator) |
| Predictability | Unpredictable and non-deterministic | Deterministic, predictable from initial seed |
| Reproducibility | Non-reproducible | Reproducible with the same seed |
| Speed | Slower due to hardware reliance | Faster, purely software-based |
| Use Cases | Cryptography, high-security applications | Simulations, gaming, procedural content generation |
| Entropy Quality | High entropy, true randomness | Lower entropy, pseudo-randomness |
Introduction to Randomness
True randomness originates from inherently unpredictable physical phenomena such as radioactive decay or atmospheric noise, providing sequences that are fundamentally unpredictable and non-reproducible. Pseudorandomness, generated by algorithms known as pseudorandom number generators (PRNGs), produces sequences that mimic randomness but are entirely determined by initial seed values, allowing for reproducibility and faster generation. Understanding the distinction between true random and pseudorandom sources is critical in fields like cryptography, simulations, and statistical sampling where the quality and unpredictability of randomness directly impact security and accuracy outcomes.
Defining True Random and Pseudorandom
True random numbers are generated from inherently unpredictable physical processes such as radioactive decay or atmospheric noise, ensuring complete randomness without any underlying deterministic pattern. Pseudorandom numbers, however, are produced by deterministic algorithms that use an initial seed value to simulate randomness, which means they can be replicated if the seed is known. True randomness is crucial for applications requiring high security and unpredictability, while pseudorandom sequences are sufficient for simulations and general computational purposes.
Sources of True Random Numbers
True random numbers are generated from physical processes such as atmospheric noise, radioactive decay, or quantum phenomena, providing high entropy and unpredictability. These sources rely on inherently unpredictable natural events, ensuring genuine randomness crucial for cryptographic applications and secure key generation. Unlike algorithm-based pseudorandom number generators, true random number generators (TRNGs) harness external entropy sources to avoid determinism and periodicity in the output sequence.
How Pseudorandom Numbers Are Generated
Pseudorandom numbers are generated using deterministic algorithms called pseudorandom number generators (PRNGs), which start with a fixed initial value known as a seed. These algorithms produce sequences of numbers that appear random but are entirely predictable if the seed and the algorithm are known. Common PRNG methods include linear congruential generators and Mersenne Twister, both designed to simulate randomness efficiently for applications in simulations, cryptography, and gaming.
Applications of True Randomness
True randomness is crucial in cryptographic systems to ensure secure key generation, preventing predictability exploited by attackers. High-stakes applications like lottery drawings, secure communications, and hardware security modules rely on true random number generators (TRNGs) to maintain integrity and confidentiality. Utilizing physical processes such as quantum phenomena or electronic noise, true randomness provides an essential foundation for robust security protocols and unbiased probabilistic computations.
Uses of Pseudorandom Generators
Pseudorandom generators produce sequences that appear random but are generated deterministically using algorithms, making them essential in simulations, cryptographic protocols, and randomized algorithms where reproducibility and speed are critical. Unlike true random sources, pseudorandom numbers allow precise control over initial seeds, enabling debugging and consistent results in scientific experiments and gaming applications. Their efficiency and ease of implementation make them indispensable in large-scale numerical methods and probabilistic modeling.
Security Implications: True vs Pseudorandom
True random number generators (TRNGs) derive entropy from physical processes, offering unpredictability critical for cryptographic security, as they resist prediction and ensure robust key generation. Pseudorandom number generators (PRNGs), while faster and more practical for many applications, rely on deterministic algorithms that can be vulnerable if their initial seed or algorithm becomes known, potentially compromising encryption schemes. Security protocols often integrate TRNGs to seed PRNGs, enhancing randomness quality and mitigating risks associated with predictable pseudorandom sequences in secure communications.
Performance and Efficiency Comparison
True random number generators (TRNGs) derive randomness from physical processes, offering high entropy but often at slower speeds and higher resource consumption compared to pseudorandom number generators (PRNGs), which use deterministic algorithms to produce sequences quickly and efficiently. PRNGs excel in applications requiring rapid number generation with predictable performance and low computational overhead, making them ideal for simulations and cryptographic protocols where controlled randomness suffices. TRNGs, while less efficient, are preferred in security-critical contexts needing unpredictable outputs resistant to reverse engineering or prediction attacks.
Limitations and Challenges
True random number generation relies on physical processes, such as quantum phenomena or atmospheric noise, which can be slow, hardware-dependent, and difficult to scale. Pseudorandom number generators (PRNGs) use deterministic algorithms that can produce high-speed sequences but suffer from predictability and periodicity, limiting their effectiveness in cryptographic and scientific applications. Ensuring entropy quality and avoiding bias remain significant challenges in both methods, affecting the reliability and security of random numbers.
Choosing the Right Randomness for Your Needs
True random numbers are generated from physical processes such as atmospheric noise or radioactive decay, ensuring unpredictability and high entropy ideal for cryptographic security and gambling applications. Pseudorandom numbers, produced by algorithmic processes like linear congruential generators or Mersenne Twister, offer faster generation and reproducibility, making them suitable for simulations, gaming, and procedural content creation. Selecting the right randomness depends on prioritizing unpredictability versus speed and repeatability, with true randomness favored for security-critical tasks and pseudorandomness preferred for performance-driven scenarios.
True random Infographic
 libterm.com
libterm.com