Hijacking involves the unlawful seizure or control of a vehicle, aircraft, or ship, often to gain leverage or demand ransom. This serious crime poses significant risks to safety and security, requiring swift and effective intervention by authorities. Explore the full article to understand the methods, prevention strategies, and legal consequences surrounding hijacking.
Table of Comparison
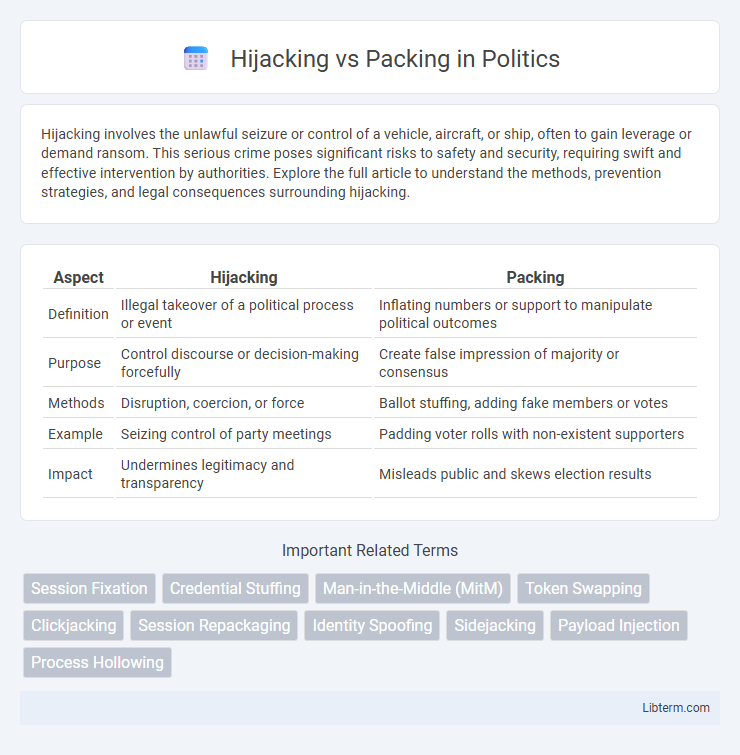
| Aspect | Hijacking | Packing |
|---|---|---|
| Definition | Illegal takeover of a political process or event | Inflating numbers or support to manipulate political outcomes |
| Purpose | Control discourse or decision-making forcefully | Create false impression of majority or consensus |
| Methods | Disruption, coercion, or force | Ballot stuffing, adding fake members or votes |
| Example | Seizing control of party meetings | Padding voter rolls with non-existent supporters |
| Impact | Undermines legitimacy and transparency | Misleads public and skews election results |
Understanding Hijacking: Definition and Key Concepts
Hijacking involves unauthorized control or manipulation of digital resources, typically by cybercriminals aiming to redirect traffic or steal sensitive data. Key concepts include session hijacking, where attackers exploit active sessions, and domain hijacking, which targets website ownership credentials. Understanding hijacking requires recognizing its methods, impact on security, and strategies for prevention.
What is Packing? An In-Depth Overview
Packing is a technique used by malware authors to compress or encrypt executable files, obscuring their true code to evade detection by antivirus software. This process modifies the binary structure, making reverse engineering and static analysis more difficult for security researchers. Common packers include UPX, Themida, and PECompact, each providing varying levels of obfuscation to hinder malware analysis and improve payload delivery stealth.
Differences Between Hijacking and Packing
Hijacking involves forcibly taking control of a vehicle or system, often with intent to redirect or exploit it, whereas packing refers to a method of compressing or encrypting malware to evade detection. The primary difference lies in the nature and purpose: hijacking targets control and manipulation, while packing is a technique used for concealment and obfuscation. Hijacking directly impacts operational control, while packing affects analysis and detection processes in cybersecurity.
Common Techniques Used in Hijacking
Hijacking techniques commonly involve URL hijacking, session hijacking, and domain hijacking, each exploiting vulnerabilities to redirect users or steal sensitive information. Attackers often use phishing schemes, cross-site scripting (XSS), or malware to gain unauthorized access or control over a user's session or data. These methods contrast with packing, which primarily focuses on compressing or encrypting malware to evade detection rather than direct user manipulation.
Popular Packing Methods Explained
Popular packing methods in malware distribution include URL packing, Base64 encoding, and polymorphic packing, designed to obfuscate code and evade detection. URL packing redirects users through multiple stages to hide the final payload, while Base64 encoding translates malicious scripts into encoded strings that are decoded during execution. Polymorphic packing continuously alters the malware's code signature, making it challenging for antivirus programs to detect hijacked or packed payloads.
Security Risks Associated with Hijacking
Hijacking involves unauthorized control over a software process, posing critical security risks such as data theft, privilege escalation, and system manipulation. This attack can lead to unauthorized access to sensitive information and compromise system integrity by injecting malicious code or redirecting execution paths. Unlike packing, which primarily focuses on code obfuscation and evasion of detection, hijacking directly threatens system security by exploiting vulnerabilities to assume control of a process or communication channel.
How Packing Affects Software Security
Packing compresses or encrypts executable files to obscure their original code, which complicates static analysis and detection by security tools. While packing can protect intellectual property and reduce file size, it often enables malware to evade antivirus detection, increasing the risk of undetected malicious activity. Security solutions must employ advanced unpacking and behavioral analysis techniques to mitigate threats associated with packed software.
Real-World Examples of Hijacking vs Packing
Hijacking involves maliciously redirecting legitimate web traffic to unauthorized destinations, such as the 2017 incident where the popular browser extension "Hola VPN" was hijacked to mine cryptocurrency on users' devices without consent. Packing refers to compressing or encrypting malware to evade detection, exemplified by the Conficker worm which used advanced packing techniques to hide its malicious payload from antivirus software. Both tactics exploit different security vulnerabilities but have been widely seen in cyberattacks targeting enterprises globally.
Detection and Prevention Strategies for Both
Hijacking attacks manipulate legitimate software or network traffic to execute malicious actions, while packing involves obfuscating malware code to evade detection by security tools. Detection strategies for hijacking include behavior analysis and anomaly detection, whereas packing detection relies on unpacking techniques and signature-based scanning. Prevention measures emphasize patch management and network segmentation for hijacking, and runtime monitoring alongside heuristic analysis to counter packing methods effectively.
Choosing the Right Defense Against Hijacking and Packing
Choosing the right defense against hijacking and packing requires a clear understanding of their distinct characteristics; hijacking involves unauthorized control over a process or data flow, while packing typically refers to obfuscation techniques used to conceal malicious code. Implementing behavior-based detection systems and heuristic analysis can effectively counter hijacking attempts by monitoring anomalies in execution patterns. For packing, robust unpacking tools combined with signature-based detection enhance the ability to identify and neutralize hidden threats without compromising system performance.
Hijacking Infographic
 libterm.com
libterm.com