A self-signed certificate is a digital certificate that is signed by the same entity whose identity it certifies, rather than a trusted certificate authority. These certificates are commonly used for testing, internal networks, or personal projects where external validation is not required. Discover how self-signed certificates work and whether they are suitable for your security needs by reading the rest of this article.
Table of Comparison
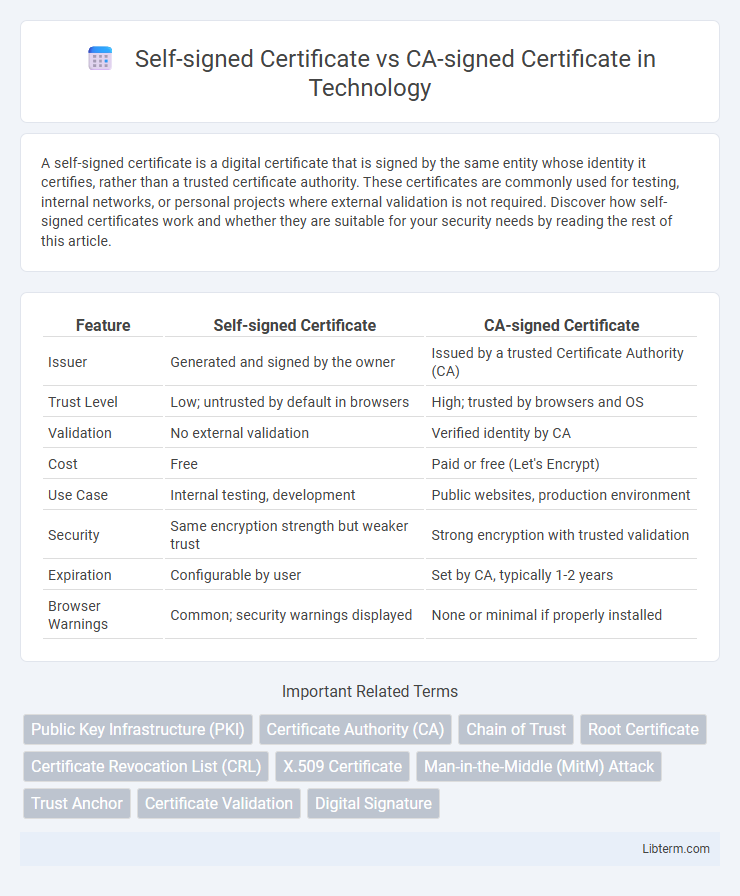
| Feature | Self-signed Certificate | CA-signed Certificate |
|---|---|---|
| Issuer | Generated and signed by the owner | Issued by a trusted Certificate Authority (CA) |
| Trust Level | Low; untrusted by default in browsers | High; trusted by browsers and OS |
| Validation | No external validation | Verified identity by CA |
| Cost | Free | Paid or free (Let's Encrypt) |
| Use Case | Internal testing, development | Public websites, production environment |
| Security | Same encryption strength but weaker trust | Strong encryption with trusted validation |
| Expiration | Configurable by user | Set by CA, typically 1-2 years |
| Browser Warnings | Common; security warnings displayed | None or minimal if properly installed |
Introduction to Digital Certificates
Digital certificates serve as digital passports that authenticate the identity of entities in online communications, ensuring secure data exchange through encryption. Self-signed certificates are created and signed by the entity itself, offering quick deployment but lacking third-party validation, which can lead to trust issues. CA-signed certificates, issued by trusted Certificate Authorities like DigiCert or Let's Encrypt, provide verified authenticity and widespread browser trust, essential for securing websites and online transactions.
What is a Self-signed Certificate?
A self-signed certificate is a digital certificate signed by the same entity that it certifies, rather than a trusted Certificate Authority (CA). It provides encryption and identity verification within controlled environments but lacks the widespread trust required for public-facing websites. Organizations often use self-signed certificates for internal testing, development, and intranet applications where cost and control are priorities.
What is a CA-signed Certificate?
A CA-signed certificate is a digital certificate issued by a trusted Certificate Authority (CA) that verifies the legitimacy of a website or organization. It establishes a secure connection by authenticating the server's identity through a trusted third party, preventing man-in-the-middle attacks. Unlike self-signed certificates, CA-signed certificates are widely recognized by browsers and operating systems, ensuring user trust and enabling seamless SSL/TLS encryption.
Key Differences: Self-signed vs CA-signed Certificates
Self-signed certificates are created and signed by the entity that owns the certificate, lacking validation from a trusted Certificate Authority (CA), which limits their acceptance and trust in browsers and applications. CA-signed certificates are issued by a recognized Certificate Authority, providing verified authenticity through a trusted chain of trust, which enhances security and user confidence. The key difference lies in trust verification, where CA-signed certificates undergo rigorous identity validation, whereas self-signed certificates do not, making them suitable mainly for internal or development purposes.
Security Implications and Trustworthiness
Self-signed certificates lack third-party validation, which makes them vulnerable to man-in-the-middle attacks and generally untrusted by browsers and operating systems, limiting their use to internal or development environments. In contrast, CA-signed certificates are issued by trusted Certificate Authorities that verify the entity's identity, providing stronger assurance of authenticity and secure communication. The inherent trust model of CA-signed certificates ensures broader acceptance, enhanced security, and compliance with industry standards, making them essential for public-facing websites and sensitive data transfers.
Use Cases for Self-signed Certificates
Self-signed certificates are ideal for internal testing environments, development stages, and securing local servers where trust chains from public Certificate Authorities (CAs) are unnecessary. They provide cost-effective encryption and facilitate quick deployment without involving third-party validation, making them suitable for non-production applications. Enterprises often utilize self-signed certificates within private networks or for internal applications that do not require public trust.
Use Cases for CA-signed Certificates
CA-signed certificates are essential for public websites, e-commerce platforms, and any online service requiring trusted identity verification and secure data encryption recognized by browsers. They provide authentication, data integrity, and protection against man-in-the-middle attacks, ensuring user trust and compliance with industry standards like PCI-DSS and HIPAA. Enterprises use CA-signed certificates to secure email communications, VPN access, and internal applications where verified identity and adherence to regulatory requirements are critical.
Pros and Cons of Self-signed Certificates
Self-signed certificates offer cost-effective encryption without relying on external Certificate Authorities (CAs), making them ideal for internal testing and development environments. However, they lack automatic trust in browsers and operating systems, leading to security warnings and potential man-in-the-middle attack vulnerabilities. Their management requires manual distribution and acceptance by users, which can complicate scalability and user experience in public-facing applications.
Pros and Cons of CA-signed Certificates
CA-signed certificates offer strong trust and compatibility across browsers and devices, ensuring encrypted communication is widely recognized as secure by users and applications. They reduce the risk of man-in-the-middle attacks by using a trusted Certificate Authority's validation, which enhances security and compliance for businesses handling sensitive data. However, CA-signed certificates involve costs and require periodic renewal and management, adding operational overhead compared to self-signed certificates.
Choosing the Right Certificate for Your Needs
Self-signed certificates provide basic encryption and are suitable for internal testing or development environments where trust is limited to known users. CA-signed certificates are issued by trusted Certificate Authorities, ensuring broader browser recognition and enhanced security, making them ideal for public-facing websites and applications. Evaluating your security requirements and audience trust needs is crucial when choosing between self-signed and CA-signed certificates.
Self-signed Certificate Infographic
 libterm.com
libterm.com