Shadow IT refers to the use of information technology systems, devices, software, applications, and services without explicit organizational approval. It can enhance innovation and agility but poses significant security risks, data breaches, and compliance issues. Discover how managing Shadow IT effectively can protect Your business and ensure seamless IT governance in the rest of this article.
Table of Comparison
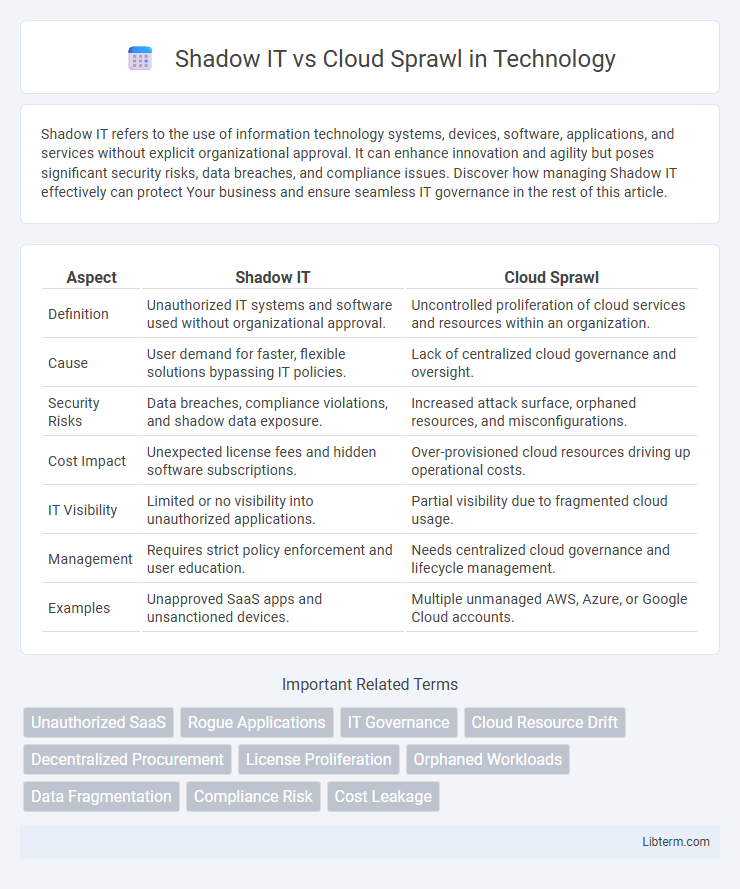
| Aspect | Shadow IT | Cloud Sprawl |
|---|---|---|
| Definition | Unauthorized IT systems and software used without organizational approval. | Uncontrolled proliferation of cloud services and resources within an organization. |
| Cause | User demand for faster, flexible solutions bypassing IT policies. | Lack of centralized cloud governance and oversight. |
| Security Risks | Data breaches, compliance violations, and shadow data exposure. | Increased attack surface, orphaned resources, and misconfigurations. |
| Cost Impact | Unexpected license fees and hidden software subscriptions. | Over-provisioned cloud resources driving up operational costs. |
| IT Visibility | Limited or no visibility into unauthorized applications. | Partial visibility due to fragmented cloud usage. |
| Management | Requires strict policy enforcement and user education. | Needs centralized cloud governance and lifecycle management. |
| Examples | Unapproved SaaS apps and unsanctioned devices. | Multiple unmanaged AWS, Azure, or Google Cloud accounts. |
Understanding Shadow IT: Definition and Risks
Shadow IT refers to the use of information technology systems, devices, software, applications, and services without explicit organizational approval, often driven by employees seeking quick solutions. This unauthorized usage creates significant security risks, such as data breaches, compliance violations, and loss of control over enterprise data. Understanding Shadow IT is crucial for organizations to implement effective governance policies and robust monitoring systems to mitigate risks and maintain cloud security.
What is Cloud Sprawl? Causes and Consequences
Cloud sprawl refers to the uncontrolled growth and proliferation of cloud services and resources within an organization, often resulting from decentralized IT management and excessive use of shadow IT. Causes include lack of visibility, weak governance policies, and the ease of deploying cloud solutions without proper oversight. Consequences involve increased operational costs, security vulnerabilities, compliance risks, and inefficient resource utilization that can hinder overall IT performance.
Key Differences: Shadow IT vs Cloud Sprawl
Shadow IT refers to the unauthorized use of IT systems and software within an organization, typically bypassing official IT approval or oversight, whereas cloud sprawl describes the uncontrolled proliferation of cloud services and resources within an enterprise, often leading to inefficiencies and increased costs. Shadow IT highlights security and compliance risks due to unmonitored applications, while cloud sprawl emphasizes management challenges and resource wastage caused by lack of centralized governance. Both issues can undermine organizational IT strategy but differ fundamentally in their origins and operational impact.
Common Drivers Behind Shadow IT and Cloud Sprawl
Common drivers behind Shadow IT and cloud sprawl include a need for increased agility and faster access to technology resources outside traditional IT approval processes. Departments often seek cloud services and software solutions independently to meet immediate business demands, driven by perceived IT bottlenecks or limitations. Budget constraints and decentralized decision-making further exacerbate the proliferation of unauthorized cloud usage and untracked digital assets.
Impact on Security: Shadow IT vs Cloud Sprawl
Shadow IT increases security risks by enabling employees to use unauthorized applications and services, often bypassing established security controls and policies, leading to data breaches and compliance violations. Cloud sprawl complicates security management by creating an unorganized proliferation of cloud resources, making it difficult to monitor, secure, and maintain consistent access controls across multiple platforms. Both phenomena undermine centralized security strategies and elevate the potential for misconfigurations, exposing organizations to increased vulnerability and attack surfaces.
Financial Implications for Businesses
Shadow IT contributes to uncontrolled spending by allowing departments to independently procure software and cloud services without IT approval, leading to redundant subscriptions and untracked expenses. Cloud sprawl exacerbates financial inefficiencies through underutilized and idle cloud resources, driving up operational costs without delivering proportional value. Both phenomena heighten the risk of budget overruns and complicate financial forecasting due to fragmented visibility into total technology expenditures.
Detecting and Managing Unauthorized Systems
Detecting unauthorized systems involves continuous monitoring of network traffic and user activities to identify Shadow IT instances and cloud sprawl risks before they escalate. Implementing automated discovery tools and integrating cloud security posture management (CSPM) helps organizations maintain visibility over unsanctioned applications and resources. Effective management requires enforcing strict governance policies and leveraging identity and access management (IAM) solutions to control usage and mitigate security vulnerabilities associated with unauthorized cloud deployments.
Best Practices to Prevent Shadow IT and Cloud Sprawl
Implement strict access controls and continuous monitoring to prevent Shadow IT by ensuring employees use authorized cloud services aligned with company policies. Employ cloud management platforms to maintain visibility over cloud resources, enabling the detection and reduction of Cloud Sprawl through automated policy enforcement and cost optimization. Regularly conduct audits and provide employee training on security risks and governance best practices to reinforce compliance and minimize unsanctioned cloud usage.
Role of IT Governance in Mitigation
IT governance plays a crucial role in mitigating Shadow IT and Cloud Sprawl by establishing clear policies and controls for cloud service usage and data management within organizations. Effective governance frameworks enable continuous monitoring, risk assessment, and compliance enforcement to prevent unauthorized cloud applications and reduce redundant, unmanaged cloud resources. By integrating automated tools and cross-departmental collaboration, IT governance ensures optimized cloud expenditure and enhances security posture across the enterprise.
Future Trends: Managing IT Complexity in the Cloud Era
Emerging trends in managing IT complexity highlight the increasing need to balance Shadow IT and cloud sprawl as enterprises adopt multi-cloud strategies and edge computing. Advanced AI-driven monitoring and governance tools are being deployed to detect unauthorized cloud usage and optimize resource allocation across diverse cloud environments. Emphasizing integrated security frameworks and automated policy enforcement will be crucial for organizations to maintain control, reduce risks, and enhance agility in the evolving cloud landscape.
Shadow IT Infographic
 libterm.com
libterm.com