Man-in-the-Middle attacks occur when a hacker secretly intercepts and alters communication between two parties without their knowledge, compromising data integrity and privacy. Protecting yourself from such attacks involves using strong encryption, secure networks, and vigilant monitoring of suspicious activities. Explore the rest of the article to learn how you can safeguard your information from these cyber threats effectively.
Table of Comparison
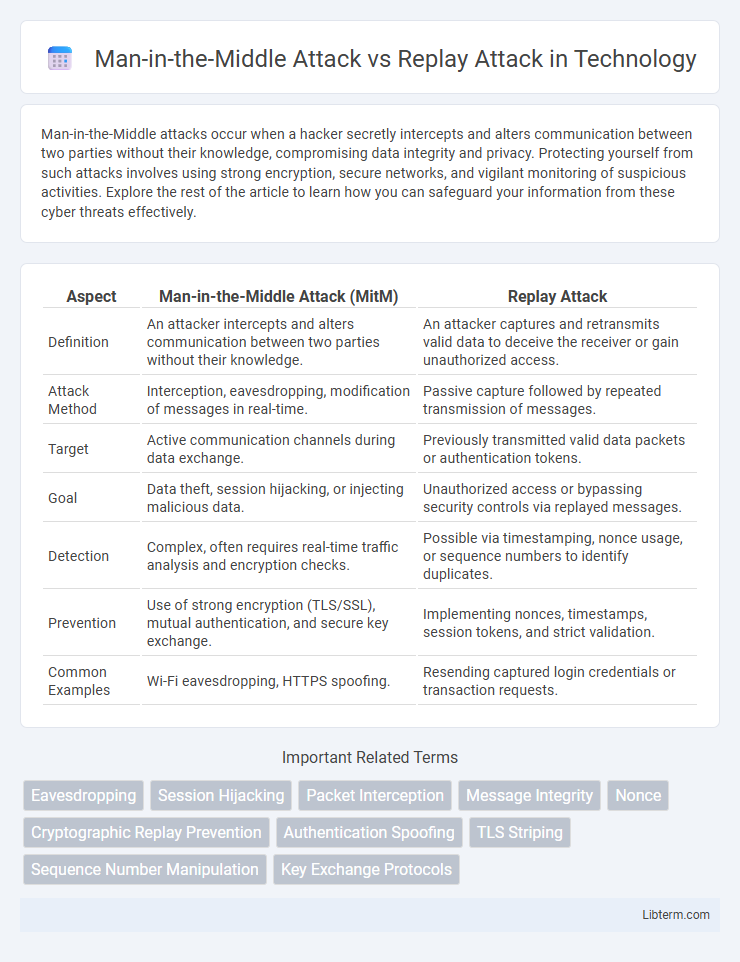
| Aspect | Man-in-the-Middle Attack (MitM) | Replay Attack |
|---|---|---|
| Definition | An attacker intercepts and alters communication between two parties without their knowledge. | An attacker captures and retransmits valid data to deceive the receiver or gain unauthorized access. |
| Attack Method | Interception, eavesdropping, modification of messages in real-time. | Passive capture followed by repeated transmission of messages. |
| Target | Active communication channels during data exchange. | Previously transmitted valid data packets or authentication tokens. |
| Goal | Data theft, session hijacking, or injecting malicious data. | Unauthorized access or bypassing security controls via replayed messages. |
| Detection | Complex, often requires real-time traffic analysis and encryption checks. | Possible via timestamping, nonce usage, or sequence numbers to identify duplicates. |
| Prevention | Use of strong encryption (TLS/SSL), mutual authentication, and secure key exchange. | Implementing nonces, timestamps, session tokens, and strict validation. |
| Common Examples | Wi-Fi eavesdropping, HTTPS spoofing. | Resending captured login credentials or transaction requests. |
Introduction to Cybersecurity Threats
Man-in-the-Middle (MitM) attacks exploit communication channels by intercepting and altering data between two parties without their knowledge, posing significant risks to confidentiality and data integrity. Replay attacks involve capturing and retransmitting valid data packets to deceive systems or gain unauthorized access, often targeting authentication mechanisms. Both threats underscore the importance of robust encryption, secure authentication protocols, and vigilant network monitoring in cybersecurity defense strategies.
What is a Man-in-the-Middle Attack?
A Man-in-the-Middle (MitM) attack occurs when an attacker secretly intercepts and possibly alters communication between two parties without their knowledge, compromising data integrity and confidentiality. This attack enables the intruder to eavesdrop, steal sensitive information such as login credentials, or inject malicious content. In contrast, a Replay Attack involves capturing and retransmitting valid data to gain unauthorized access, but does not require real-time interception or modification of the communication stream.
Understanding Replay Attacks
Replay attacks involve intercepting and retransmitting valid data transmissions to deceive a recipient into unauthorized actions, exploiting the lack of freshness or time stamps in communication protocols. This type of attack contrasts with Man-in-the-Middle (MitM) attacks, where the attacker actively intercepts, alters, and relays messages between two parties in real-time to eavesdrop or manipulate information. Understanding replay attacks requires recognizing the importance of cryptographic nonce values, timestamps, and sequence numbers in preventing attackers from successfully reusing captured data packets.
Man-in-the-Middle vs Replay Attack: Key Differences
Man-in-the-Middle (MitM) attacks involve an attacker secretly intercepting and altering communication between two parties, whereas Replay Attacks consist of capturing and retransmitting valid data to deceive the recipient. The primary difference lies in MitM attacks enabling active manipulation of the data stream in real-time, while Replay Attacks rely on passive duplication without modification. MitM attacks exploit vulnerabilities in communication protocols to insert, modify, or delete messages, whereas Replay Attacks typically bypass authentication by resending captured valid messages.
Attack Vectors and Methods
Man-in-the-Middle (MitM) attacks exploit interception of communication channels by attackers who insert themselves between two parties to eavesdrop or alter messages in real-time, often using techniques like packet sniffing, session hijacking, or DNS spoofing. Replay attacks involve capturing valid data transmissions and retransmitting them to deceive the recipient, typically executed through the reuse of authentication tokens, intercepted network frames, or previously recorded messages without modification. Both attack vectors target network vulnerabilities but differ in methodology, with MitM attacks focusing on manipulation of ongoing communication and replay attacks emphasizing the replication of past legitimate interactions.
Common Targets and Vulnerabilities
Man-in-the-Middle (MITM) attacks and Replay attacks commonly target communication channels such as unsecured Wi-Fi networks, online banking sessions, and email exchanges where encryption is weak or improperly implemented. Vulnerabilities exploited include poor authentication mechanisms, lack of session encryption, and failure to use time-stamped tokens or nonces that prevent message reuse. Both attacks thrive on intercepting or capturing data transmissions, but MITM manipulates data in transit while Replay attacks resend valid data to gain unauthorized access or disrupt systems.
Real-World Examples and Case Studies
Man-in-the-Middle (MitM) attacks have been prominently demonstrated in the 2011 DigiNotar breach, where attackers intercepted communications to issue fraudulent SSL certificates, undermining web security globally. Replay attacks were notably exploited in the 2018 Tesla Model 3 key fob vulnerability, allowing attackers to capture and retransmit signals to unlock and start vehicles without authorization. Both attack types highlight the critical need for robust encryption protocols and multi-factor authentication in protecting sensitive digital communications and infrastructures.
Detection Techniques for Each Attack
Man-in-the-Middle (MitM) attack detection techniques prioritize monitoring unusual network patterns, employing encryption protocols like TLS to prevent unauthorized interception, and utilizing anomaly-based intrusion detection systems that flag abnormal communication sequences. Replay attack detection centers around time-stamping packets, employing nonce values in authentication processes, and using sequence number validation to identify duplicated or delayed transmissions. Both attack types benefit from real-time traffic analysis and multi-factor authentication systems to enhance detection accuracy.
Prevention and Mitigation Strategies
Man-in-the-Middle (MITM) attacks and Replay attacks both compromise communication security but require distinct prevention methods; MITM attacks are mitigated through strong encryption protocols like TLS, mutual authentication mechanisms, and the use of secure key exchanges such as Diffie-Hellman. Replay attacks are prevented by implementing nonce values, timestamps, and session tokens to ensure message freshness and uniqueness, along with enforcing strict synchronization between communicating parties. Employing multi-factor authentication and continuous network monitoring further enhances defense against these threats by detecting anomalies and unauthorized access attempts.
Conclusion: Securing Against Cyber Attacks
Securing against Man-in-the-Middle (MITM) and Replay Attacks requires robust encryption protocols such as TLS and the implementation of strong authentication mechanisms including multi-factor authentication (MFA). Network security tools like intrusion detection systems (IDS) combined with session tokens and timestamp validation mitigate the risk of replay attacks by ensuring data integrity and freshness. Effective cybersecurity strategies must continuously update cryptographic standards and monitor network traffic to prevent interception and unauthorized retransmission of sensitive information.
Man-in-the-Middle Attack Infographic
 libterm.com
libterm.com