Encrypted data safeguards sensitive information by converting it into a coded format that is unreadable without the correct decryption key. This process ensures that your personal or business information remains secure from unauthorized access and cyber threats. Explore the rest of the article to learn how encryption enhances digital security and protects your valuable data.
Table of Comparison
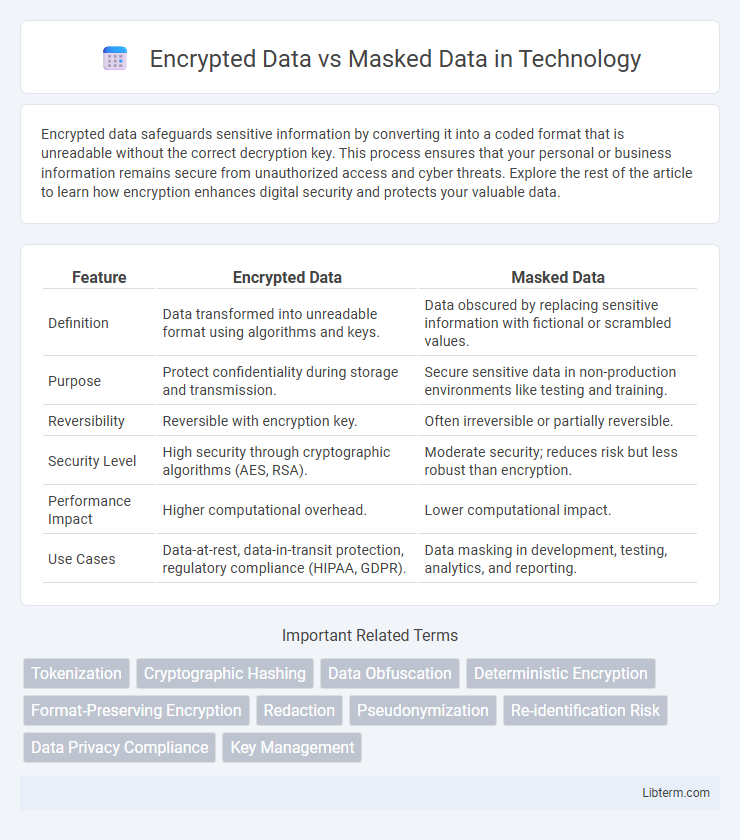
| Feature | Encrypted Data | Masked Data |
|---|---|---|
| Definition | Data transformed into unreadable format using algorithms and keys. | Data obscured by replacing sensitive information with fictional or scrambled values. |
| Purpose | Protect confidentiality during storage and transmission. | Secure sensitive data in non-production environments like testing and training. |
| Reversibility | Reversible with encryption key. | Often irreversible or partially reversible. |
| Security Level | High security through cryptographic algorithms (AES, RSA). | Moderate security; reduces risk but less robust than encryption. |
| Performance Impact | Higher computational overhead. | Lower computational impact. |
| Use Cases | Data-at-rest, data-in-transit protection, regulatory compliance (HIPAA, GDPR). | Data masking in development, testing, analytics, and reporting. |
Introduction to Data Protection Methods
Encrypted data transforms information into unreadable ciphertext using cryptographic algorithms, ensuring confidentiality and secure communication even if intercepted. Masked data replaces sensitive information with obfuscated characters or dummy data to prevent unauthorized access while maintaining data format for testing or analysis. Both methods are essential in data protection strategies, with encryption focusing on securing data in transit and storage, and masking enabling safe data use in non-secure environments.
Understanding Encrypted Data
Encrypted data transforms readable information into a coded format using algorithms and cryptographic keys, ensuring confidentiality and preventing unauthorized access. This process maintains data integrity and enables secure transmission over untrusted networks by making the content inaccessible without the correct decryption key. Common encryption methods include Advanced Encryption Standard (AES) and RSA, which provide varying levels of security based on key length and algorithm complexity.
Exploring Masked Data
Masked data involves transforming sensitive information by obscuring or replacing specific elements to protect privacy while maintaining data utility for analysis and testing. Unlike encrypted data, which requires decryption keys to access original content, masked data is intentionally altered to prevent exposure of confidential information without complex reversal processes. This approach ensures compliance with data protection regulations and enables safe use in non-secure environments such as development and analytics.
Key Differences Between Encryption and Masking
Encryption transforms data into a coded format using cryptographic algorithms and keys, ensuring that only authorized users with the correct decryption key can access the original information. Masking, on the other hand, substitutes or obfuscates data elements to create a masked version that retains format and usability but hides sensitive details, typically without requiring decryption keys. Key differences include encryption's reversible nature through secure key management versus masking's non-reversible alteration primarily used for testing and data privacy.
Use Cases for Encrypted Data
Encrypted data ensures confidentiality during storage and transmission by converting information into unreadable ciphertext accessible only with decryption keys, making it ideal for securing sensitive customer records, financial transactions, and personal healthcare information. Its use cases include protecting data in cloud storage, safeguarding communication channels in messaging apps, and complying with regulations like GDPR and HIPAA by preventing unauthorized access. Encryption supports secure data sharing across networks, enabling trusted collaboration and maintaining privacy in remote work environments.
Applications of Data Masking
Data masking is extensively applied in software testing, enabling developers to work with realistic datasets without exposing sensitive information. It is crucial in data sharing scenarios, ensuring compliance with privacy regulations such as GDPR and HIPAA by protecting personally identifiable information (PII). Masked data also supports analytics and business intelligence operations, allowing companies to derive insights while maintaining data confidentiality.
Security Implications: Encryption vs Masking
Encrypted data transforms information into a secure, unreadable format using cryptographic algorithms, ensuring confidentiality and preventing unauthorized access even if intercepted. Masked data replaces sensitive information with fictional but realistic values, protecting data visibility while maintaining usability for testing and analysis without exposing original details. Encryption provides stronger security by enabling secure data restoration only with decryption keys, whereas masking primarily safeguards privacy without allowing reversal to the original data.
Compliance and Regulatory Considerations
Encrypted data ensures compliance with regulations such as GDPR and HIPAA by protecting sensitive information through cryptographic algorithms, making data inaccessible without proper decryption keys. Masked data supports regulatory requirements by obfuscating personal identifiers in non-production environments, reducing risks of exposure while maintaining data utility for testing and analysis. Choosing between encryption and masking depends on compliance needs, data sensitivity, and the specific requirements of standards like PCI DSS and CCPA.
Performance Impact of Encryption and Masking
Encryption often introduces higher computational overhead than masking due to complex algorithms like AES or RSA that require significant processing power and time, impacting system performance, especially in real-time applications. Masking, involving simpler techniques such as substitution or shuffling of data elements, typically results in lower latency and minimal impact on throughput, making it more suitable for scenarios requiring fast data access and display. Performance impact varies based on data size, algorithm complexity, and system architecture, with encryption generally demanding more resources for secure key management and decryption processes.
Choosing the Right Data Protection Strategy
Choosing the right data protection strategy requires understanding that encrypted data transforms sensitive information into unreadable ciphertext using cryptographic algorithms, ensuring confidentiality during storage and transmission. Masked data, on the other hand, obscures original data elements by replacing or redacting values, often used in non-production environments to maintain usability without exposing sensitive information. Organizations must evaluate factors such as data sensitivity, compliance requirements, access needs, and performance impact to decide between encryption for robust security and masking for safe data usability.
Encrypted Data Infographic
 libterm.com
libterm.com