Fuzz testing is an automated software testing technique that involves inputting random, unexpected, or malformed data to discover coding errors and security vulnerabilities. By simulating potential attacks or faults, it helps ensure the robustness and reliability of your software applications. Explore the article to learn how fuzz testing can enhance your development process and safeguard your systems.
Table of Comparison
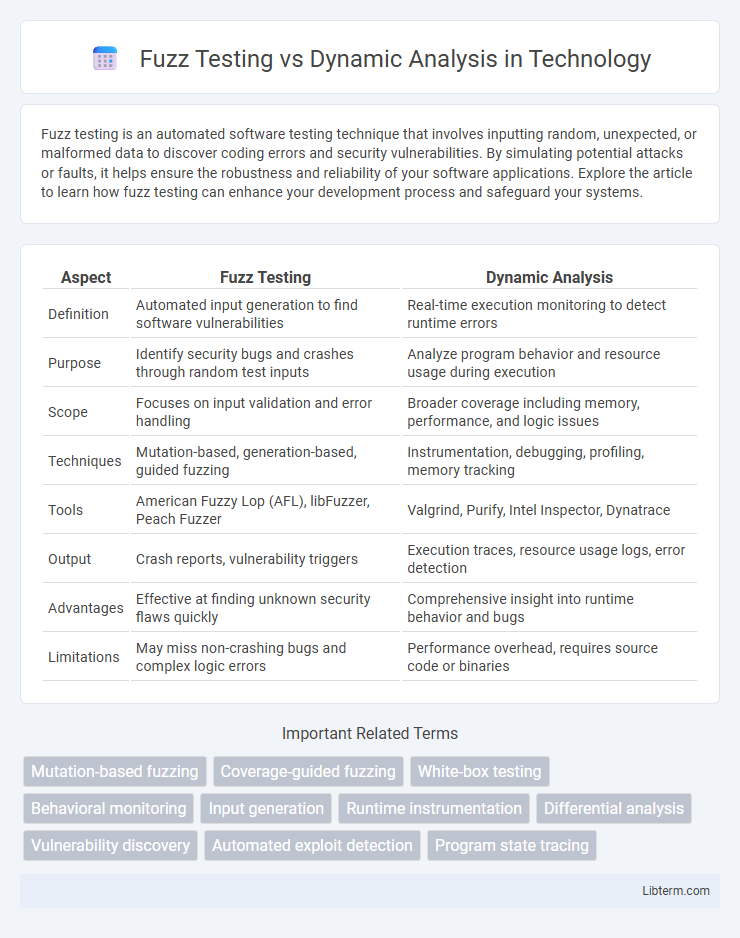
| Aspect | Fuzz Testing | Dynamic Analysis |
|---|---|---|
| Definition | Automated input generation to find software vulnerabilities | Real-time execution monitoring to detect runtime errors |
| Purpose | Identify security bugs and crashes through random test inputs | Analyze program behavior and resource usage during execution |
| Scope | Focuses on input validation and error handling | Broader coverage including memory, performance, and logic issues |
| Techniques | Mutation-based, generation-based, guided fuzzing | Instrumentation, debugging, profiling, memory tracking |
| Tools | American Fuzzy Lop (AFL), libFuzzer, Peach Fuzzer | Valgrind, Purify, Intel Inspector, Dynatrace |
| Output | Crash reports, vulnerability triggers | Execution traces, resource usage logs, error detection |
| Advantages | Effective at finding unknown security flaws quickly | Comprehensive insight into runtime behavior and bugs |
| Limitations | May miss non-crashing bugs and complex logic errors | Performance overhead, requires source code or binaries |
Introduction to Fuzz Testing and Dynamic Analysis
Fuzz testing involves automatically inputting large volumes of random or semi-random data into software to uncover security vulnerabilities and bugs by triggering unexpected behaviors. Dynamic analysis examines a program's execution in real-time, analyzing runtime behavior such as memory usage, performance, and interaction with the operating system. Both techniques play critical roles in identifying security flaws and ensuring software robustness by testing code under various, unpredictable conditions.
Defining Fuzz Testing: Techniques and Tools
Fuzz testing, a software testing technique aimed at uncovering security vulnerabilities and coding errors, involves inputting random, malformed, or unexpected data into programs to trigger crashes or unexpected behavior. Popular fuzz testing tools include AFL (American Fuzzy Lop), libFuzzer, and Peach Fuzzer, each designed for different environments and offering capabilities like coverage-guided fuzzing and protocol-aware inputs. These tools automate fuzz input generation and monitor software reactions in real-time, making fuzz testing an essential component within dynamic analysis frameworks for improving software robustness and security.
What Is Dynamic Analysis? Methods and Applications
Dynamic analysis is a software testing technique that evaluates a program's behavior during execution, identifying runtime errors, memory leaks, and performance bottlenecks through methods such as profiling, instrumentation, and debugging tools. This approach contrasts with static analysis by analyzing the live behavior of applications in real-time under various conditions, enabling detection of vulnerabilities such as concurrency issues and security flaws. Dynamic analysis is widely applied in security testing, performance optimization, and ensuring software reliability in environments ranging from embedded systems to large-scale enterprise applications.
Key Differences Between Fuzz Testing and Dynamic Analysis
Fuzz testing primarily involves automated input generation to identify vulnerabilities by triggering unexpected behaviors or crashes, while dynamic analysis encompasses broader runtime examination techniques such as profiling, memory analysis, and behavior monitoring. Fuzz testing focuses on robustness by injecting malformed or random data to uncover security flaws, whereas dynamic analysis evaluates program execution to detect performance issues, memory leaks, and logical errors. The core difference lies in fuzz testing's emphasis on input-driven fault discovery versus dynamic analysis's holistic runtime insight for software quality assurance.
Advantages of Fuzz Testing in Vulnerability Detection
Fuzz testing excels in identifying unknown software vulnerabilities by automatically generating and injecting malformed inputs, uncovering edge cases that traditional dynamic analysis might overlook. Its ability to continuously test applications with diverse, random data increases the likelihood of exposing memory corruption, buffer overflows, and input validation flaws. This proactive, high-coverage approach enables early detection of critical security issues, improving software robustness and reducing the attack surface proactively.
Benefits of Dynamic Analysis for Software Security
Dynamic analysis enhances software security by identifying vulnerabilities during actual code execution, allowing detection of runtime errors such as memory leaks, buffer overflows, and race conditions. This method provides comprehensive insights into system behavior under real-world conditions, improving the accuracy of threat detection compared to static techniques like fuzz testing. Incorporating dynamic analysis enables early remediation of security flaws, reducing the risk of exploitation and strengthening overall application resilience.
Use Cases: When to Choose Fuzz Testing vs Dynamic Analysis
Fuzz testing excels in identifying security vulnerabilities and robustness issues by generating large volumes of randomized input data, making it ideal for uncovering unexpected crashes or memory leaks in software applications. Dynamic analysis is best suited for performance profiling, debugging, and detecting runtime errors by monitoring program execution in real-time, which helps developers understand code behavior and resource usage. Choose fuzz testing for automated vulnerability detection and dynamic analysis for in-depth, real-time behavioral insights during software development and testing phases.
Integration of Fuzz Testing and Dynamic Analysis in SDLC
Integrating fuzz testing and dynamic analysis within the Software Development Life Cycle (SDLC) enhances vulnerability detection by combining automated input mutation with runtime behavior monitoring. This synergy allows continuous identification of memory leaks, crashes, and logic errors during various development stages, improving overall software reliability. Industry leaders report that embedding both techniques early in SDLC reduces security flaws by up to 40%, accelerating remediation and delivery timelines.
Challenges and Limitations of Both Approaches
Fuzz testing faces challenges such as generating meaningful inputs for complex software and dealing with time-consuming false positives that hinder effective vulnerability identification. Dynamic analysis struggles with incomplete code coverage and high resource consumption due to runtime monitoring, which limits its scalability for large applications. Both approaches have limitations in handling intricate input structures and often require complementary techniques for thorough security assessment.
Future Trends in Software Security Testing
Fuzz testing and dynamic analysis are evolving rapidly with the integration of artificial intelligence and machine learning to enhance vulnerability detection and reduce false positives. The future of software security testing emphasizes automated, continuous testing pipelines that leverage real-time behavioral monitoring and adaptive fuzzing techniques. Increasingly, cloud-native environments and containerized applications drive the need for scalable, intelligent security testing frameworks that combine fuzz testing with dynamic analysis to identify complex runtime threats effectively.
Fuzz Testing Infographic
 libterm.com
libterm.com