Deterministic systems follow a predictable pattern where outcomes are precisely determined by initial conditions and rules, eliminating randomness from their behavior. These systems play a crucial role in fields like computing, physics, and engineering by enabling accurate modeling and simulation. Explore the detailed article to understand how deterministic principles influence your daily technology and decision-making processes.
Table of Comparison
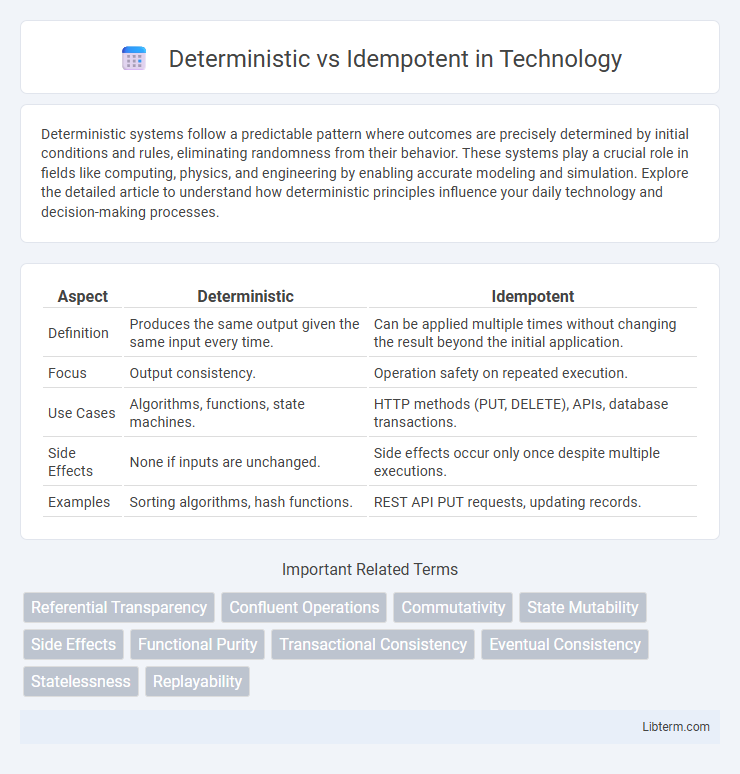
| Aspect | Deterministic | Idempotent |
|---|---|---|
| Definition | Produces the same output given the same input every time. | Can be applied multiple times without changing the result beyond the initial application. |
| Focus | Output consistency. | Operation safety on repeated execution. |
| Use Cases | Algorithms, functions, state machines. | HTTP methods (PUT, DELETE), APIs, database transactions. |
| Side Effects | None if inputs are unchanged. | Side effects occur only once despite multiple executions. |
| Examples | Sorting algorithms, hash functions. | REST API PUT requests, updating records. |
Understanding Deterministic Processes
Deterministic processes consistently produce the same output given identical inputs, ensuring predictability and reliability in system behavior. This characteristic enables accurate replication and debugging since every execution path yields a predefined result. Understanding deterministic processes is crucial for designing algorithms and systems that require stable and repeatable outcomes without variance.
Defining Idempotent Operations
Idempotent operations produce the same result and state regardless of how many times they are executed, ensuring consistency in distributed systems and APIs. These operations, such as HTTP PUT requests or database update commands, prevent unintended side effects by maintaining data integrity through repeated calls. Defining idempotent operations is crucial for designing reliable, fault-tolerant applications where retry mechanisms are involved without causing duplicate processing or data corruption.
Key Differences: Deterministic vs Idempotent
Deterministic operations consistently produce the same output from identical inputs, ensuring predictability in processing, while idempotent operations yield the same outcome even when performed multiple times, emphasizing effect stability over repetitions. Determinism centers on function output uniformity, whereas idempotency highlights state consistency despite repeated executions. Understanding this distinction is crucial in system design for error handling and retry mechanisms.
Real-World Examples of Determinism
Deterministic systems consistently produce the same output given the same initial conditions, exemplified by traditional calculators and embedded control systems in automotive airbags where exact responses are critical. In contrast, idempotent operations, such as HTTP PUT requests to update a resource, ensure that multiple identical requests result in the same state without unintended side effects. Real-world determinism dominates safety-critical applications, where predictability and repeatability, like in aviation autopilot systems, drive system reliability and user trust.
Real-World Examples of Idempotence
Idempotence in real-world applications is evident in RESTful APIs where HTTP methods like GET, PUT, and DELETE ensure multiple identical requests yield the same result without side effects, such as fetching or updating a resource. Payment processing systems utilize idempotent operations to prevent duplicate charges by recognizing repeated transactions with the same identifier. DNS queries also demonstrate idempotence by consistently returning the same IP address for a domain name regardless of how many times the request is repeated.
Benefits of Deterministic Systems
Deterministic systems guarantee predictable and consistent outputs for identical inputs, enhancing reliability in critical applications like financial transactions and automated controls. This predictability simplifies debugging and testing processes, reducing development time and costs. Strong determinism also improves system resilience by enabling precise recovery mechanisms after failures, ensuring stable and secure operations.
Advantages of Idempotent Design
Idempotent design in APIs ensures that multiple identical requests have the same effect as a single request, enhancing reliability and fault tolerance in distributed systems. This approach reduces unintended side effects and simplifies error recovery by allowing safe retries without compromising data integrity. Idempotent operations improve system resilience and user experience by preventing duplicate actions and enabling consistent state management.
Common Use Cases in Software Engineering
Deterministic functions consistently produce the same output for a given input, making them essential in caching, testing, and debugging applications where reproducibility is critical. Idempotent operations deliver the same result even when executed multiple times, a key property in RESTful APIs and distributed systems to ensure safe retries and fault tolerance. Both concepts improve reliability and predictability but serve distinct roles: deterministic for consistency in computation and idempotent for safe state manipulation.
Challenges and Limitations
Deterministic and idempotent operations face challenges in distributed systems where network failures and retries can cause inconsistencies or duplicate processing. Deterministic processes may struggle with non-deterministic inputs or external state changes, limiting their predictability. Idempotent operations require careful design to ensure repeated requests produce the same outcome, which can be complex in stateful services and lead to performance overhead.
Best Practices for Implementation
Deterministic functions produce consistent outputs for the same input, ensuring predictable behavior crucial for reliable system operations and debugging, while idempotent functions guarantee that multiple identical requests have the same effect as a single request, preventing unintended side effects in distributed systems. Best practices for implementing deterministic functions include avoiding reliance on external state, random values, or time-dependent data, and ensuring pure calculations are isolated from side effects. For idempotent implementations, design APIs to safely handle repeated calls by using unique request identifiers, stateless processing, and ensuring database operations are atomic and repeat-safe to maintain data integrity.
Deterministic Infographic
 libterm.com
libterm.com