A Certificate Authority (CA)-signed certificate is a digital certificate issued by a trusted third party that verifies the authenticity of a website or organization, ensuring secure communication and data encryption. These certificates are crucial for establishing trust in online transactions and protecting sensitive information from cyber threats. Discover how a CA-signed certificate can enhance your digital security by reading the rest of the article.
Table of Comparison
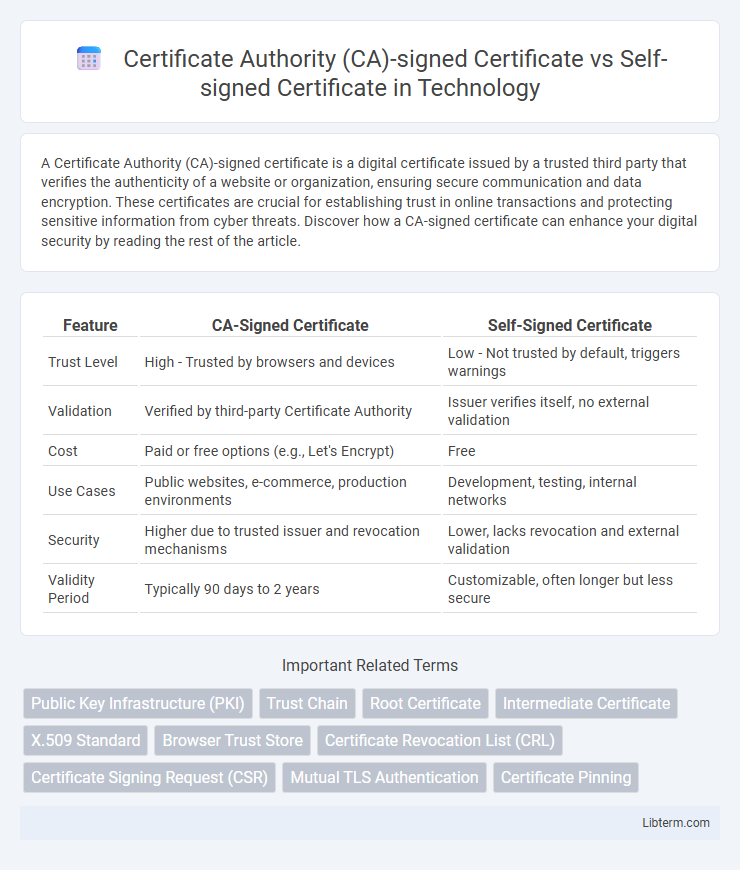
| Feature | CA-Signed Certificate | Self-Signed Certificate |
|---|---|---|
| Trust Level | High - Trusted by browsers and devices | Low - Not trusted by default, triggers warnings |
| Validation | Verified by third-party Certificate Authority | Issuer verifies itself, no external validation |
| Cost | Paid or free options (e.g., Let's Encrypt) | Free |
| Use Cases | Public websites, e-commerce, production environments | Development, testing, internal networks |
| Security | Higher due to trusted issuer and revocation mechanisms | Lower, lacks revocation and external validation |
| Validity Period | Typically 90 days to 2 years | Customizable, often longer but less secure |
Introduction to Digital Certificates
Digital certificates serve as digital passports that verify the identity of entities in online communications, establishing trust through encryption. A Certificate Authority (CA)-signed certificate is issued by a trusted third-party organization that validates the entity's identity, ensuring wide acceptance and security across browsers and devices. In contrast, a self-signed certificate is created and signed by the entity itself, lacking external validation, which often results in limited trust and security warnings during web interactions.
What is a Certificate Authority (CA)?
A Certificate Authority (CA) is a trusted organization that issues digital certificates used to verify the identity of websites, individuals, or entities in online communications. CA-signed certificates are widely trusted by browsers and operating systems because the CA validates the certificate holder's identity through a rigorous verification process. Self-signed certificates lack this external validation, making them less reliable for secure transactions and often triggering security warnings in web browsers.
Understanding CA-signed Certificates
CA-signed certificates are digital certificates issued and verified by a trusted Certificate Authority, ensuring the authenticity and legitimacy of a website or service. These certificates enable secure SSL/TLS encryption, protect data integrity, and establish user trust by linking the certificate holder's identity to a verified entity. Organizations rely on CA-signed certificates to prevent man-in-the-middle attacks and meet industry compliance standards for secure communications.
What is a Self-signed Certificate?
A self-signed certificate is a digital certificate that is signed by the same entity whose identity it certifies, rather than by a trusted Certificate Authority (CA). It provides encryption and authentication for secure communication but lacks the inherent trust and validation from an external CA, making it less trusted by browsers and operating systems. Self-signed certificates are often used for internal testing, development environments, or systems where trust can be manually configured.
Key Differences between CA-signed and Self-signed Certificates
CA-signed certificates are issued by trusted Certificate Authorities, ensuring widespread recognition and validation across browsers and devices, while self-signed certificates are created and signed by the entity itself, lacking external validation. CA-signed certificates enable higher trust levels, facilitate encrypted communications with verified identities, and prevent man-in-the-middle attacks, whereas self-signed certificates often trigger security warnings and are mainly used for internal testing or development. The issuance process for CA-signed certificates involves identity verification and a payment fee, contrasting with the free and instant creation of self-signed certificates without third-party verification.
Security Implications of CA-signed vs Self-signed Certificates
CA-signed certificates offer higher security assurance by validating the identity of the certificate holder through trusted third-party authorities, reducing the risk of man-in-the-middle attacks and impersonation. Self-signed certificates lack external validation, making them vulnerable to spoofing and phishing attacks since users cannot verify the authenticity without manual trust establishment. Implementing CA-signed certificates ensures better encryption integrity and widespread browser trust, critical for secure online communications.
Trust Models and Validation Processes
A Certificate Authority (CA)-signed certificate relies on a trusted third-party organization to validate the identity of the certificate holder, ensuring broader trust across browsers and operating systems through a hierarchical Public Key Infrastructure (PKI). In contrast, a self-signed certificate is generated and signed by the entity itself, lacking third-party validation, which limits trust to specific environments or internal networks. The validation process for CA-signed certificates involves rigorous verification and issuance protocols, while self-signed certificates bypass external validation, increasing the risk of man-in-the-middle attacks if not properly managed.
Use Cases for CA-signed Certificates
CA-signed certificates are essential for public-facing websites, e-commerce platforms, and applications requiring user trust and data encryption, ensuring identity verification by a trusted third party. They enable secure HTTPS connections that browsers recognize as legitimate, preventing security warnings and enhancing customer confidence. Enterprises also use CA-signed certificates for email encryption, code signing, and securing internal networks where validated identity and extensive compatibility are critical.
When to Use Self-signed Certificates
Self-signed certificates are ideal for internal testing environments, development phases, or intranet applications where trust is managed within a closed group. They eliminate the cost and waiting time associated with obtaining a Certificate Authority (CA)-signed certificate but lack external trust validation, causing browsers to flag warnings. When confidentiality is needed without public trust, such as in private networks or temporary use, self-signed certificates provide a practical security solution.
Summary: Choosing the Right Certificate for Your Needs
A Certificate Authority (CA)-signed certificate provides trusted validation by a recognized third party, ensuring widespread browser compatibility and enhanced security for public-facing websites. Self-signed certificates offer cost-effective encryption but lack third-party verification, making them suitable primarily for internal testing or development environments. Selecting the right certificate depends on balancing the need for trust, security, and budget, with CA-signed certificates preferred for production use and self-signed certificates viable for private or experimental purposes.
Certificate Authority (CA)-signed Certificate Infographic
 libterm.com
libterm.com