Stateful inspection firewall technology monitors the state of active connections and makes decisions based on the context of the traffic rather than just individual packets. This approach enhances network security by tracking data flows and verifying that each packet is part of an established session, preventing unauthorized access and attacks. Discover how stateful inspection can improve your network defenses by exploring the details in the rest of the article.
Table of Comparison
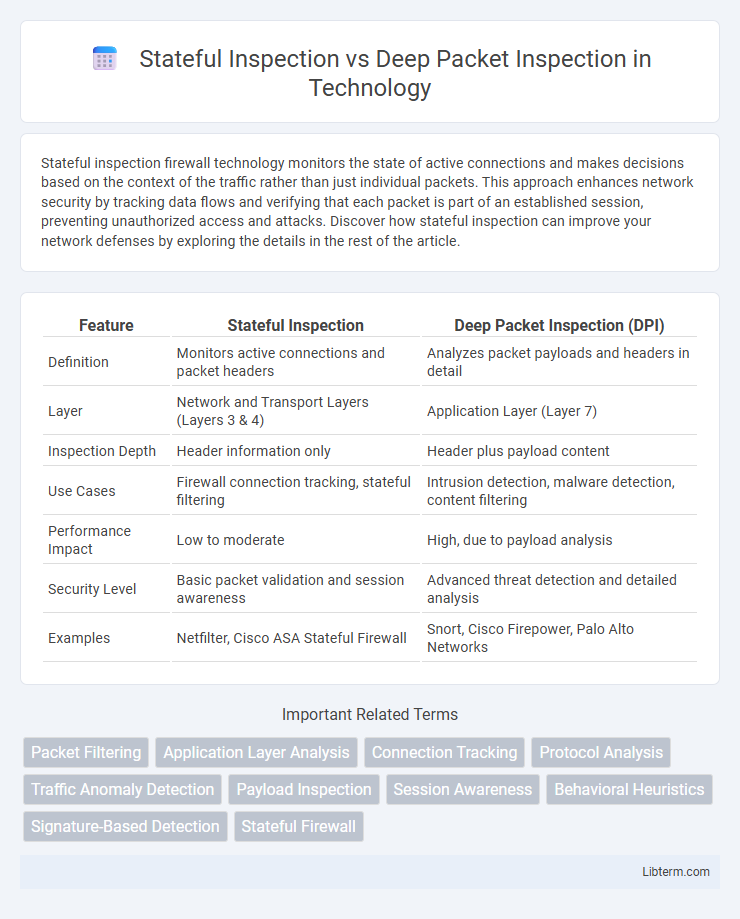
| Feature | Stateful Inspection | Deep Packet Inspection (DPI) |
|---|---|---|
| Definition | Monitors active connections and packet headers | Analyzes packet payloads and headers in detail |
| Layer | Network and Transport Layers (Layers 3 & 4) | Application Layer (Layer 7) |
| Inspection Depth | Header information only | Header plus payload content |
| Use Cases | Firewall connection tracking, stateful filtering | Intrusion detection, malware detection, content filtering |
| Performance Impact | Low to moderate | High, due to payload analysis |
| Security Level | Basic packet validation and session awareness | Advanced threat detection and detailed analysis |
| Examples | Netfilter, Cisco ASA Stateful Firewall | Snort, Cisco Firepower, Palo Alto Networks |
Introduction to Stateful Inspection and Deep Packet Inspection
Stateful Inspection monitors the state of active connections and makes decisions based on the context of traffic, enhancing firewall security by tracking packet sequences in a session. Deep Packet Inspection (DPI) examines the actual data payload within packets, enabling identification of application-level threats, malware, and policy violations. Both techniques serve critical roles in network security, with Stateful Inspection focusing on connection states while DPI focuses on content inspection.
How Stateful Inspection Works
Stateful Inspection works by monitoring the state and context of active network connections, tracking packet attributes such as source, destination IP addresses, port numbers, and sequence numbers to determine whether packets belong to an established session. It examines packet headers at the network and transport layers, maintaining a state table to quickly validate incoming packets against known connection states, enhancing security while maintaining efficient processing. This method contrasts with Deep Packet Inspection, which analyzes the packet payload for more granular content inspection beyond header information.
How Deep Packet Inspection Works
Deep Packet Inspection (DPI) analyzes the data content within packets by examining both header information and payload in real-time, enabling detection of complex threats and policy violations. Unlike Stateful Inspection, which tracks connection states and header information, DPI inspects packet payloads to identify application-layer signatures, malware, and unauthorized content. This granular analysis allows network devices to enforce advanced security policies, filter malware, and manage bandwidth effectively.
Key Differences Between Stateful and Deep Packet Inspection
Stateful Inspection monitors active connections by tracking packet state and context using TCP/IP header information, enabling efficient firewall decisions based on session history. Deep Packet Inspection (DPI) examines the entire packet content, including payload data, to identify and block specific applications, viruses, or intrusions, providing granular security beyond header analysis. While Stateful Inspection prioritizes connection state and protocol compliance, DPI offers comprehensive threat detection by analyzing data patterns and application-layer content.
Performance and Efficiency Comparison
Stateful Inspection firewalls efficiently track active connections by maintaining session state information, resulting in faster packet processing and lower latency compared to Deep Packet Inspection (DPI), which examines packet payloads in detail for enhanced security but requires significantly more processing power. DPI's thorough analysis improves threat detection accuracy but can lead to reduced network throughput and increased CPU usage, impacting overall performance. For environments prioritizing high-speed data transfer and minimal delay, Stateful Inspection offers superior efficiency, while DPI suits scenarios demanding comprehensive traffic analysis despite its heavier resource consumption.
Security Capabilities of Each Method
Stateful Inspection enhances network security by monitoring the state and context of active connections, allowing it to block unauthorized access based on predefined rules and session information. Deep Packet Inspection (DPI) offers advanced security capabilities by examining the content of data packets at the application layer, enabling detection of malware, intrusions, and policy violations with precise granular control. While Stateful Inspection excels in tracking connection states to prevent unauthorized traffic, DPI provides deeper insights for identifying sophisticated threats and enforcing comprehensive security policies.
Pros and Cons of Stateful Inspection
Stateful Inspection provides efficient packet filtering by tracking the state of active connections, which enhances network security with lower resource consumption compared to Deep Packet Inspection. It excels at managing large volumes of traffic with minimal latency but lacks the detailed content analysis capabilities necessary to detect sophisticated threats hidden within packet payloads. Despite its performance advantages, Stateful Inspection may miss application-layer attacks that Deep Packet Inspection can identify through comprehensive packet payload inspection.
Pros and Cons of Deep Packet Inspection
Deep Packet Inspection (DPI) allows for detailed analysis of packet payloads, enabling enhanced security through detection of viruses, malware, and intrusions beyond what Stateful Inspection offers. DPI's ability to inspect data content deeply improves threat identification and policy enforcement but raises concerns over privacy violations and increased processing latency. While DPI provides granular control and improved threat detection, its resource-intensive nature and potential privacy issues can complicate network management and user trust.
Real-World Use Cases for Both Techniques
Stateful Inspection is widely used in enterprise firewalls to monitor active connections and ensure only legitimate packets matching the state of a session are allowed, securing applications like VPNs and VoIP. Deep Packet Inspection (DPI) excels in network security by analyzing packet content for threats such as malware, data leaks, and policy violations, making it critical for intrusion detection systems and content filtering in ISPs. Both techniques complement each other, with Stateful Inspection providing efficient connection tracking and DPI offering granular inspection, optimizing network security in environments demanding high performance and detailed traffic analysis.
Choosing the Right Inspection Method for Your Network
Stateful Inspection monitors active connections and examines packet headers to effectively manage allowed traffic, ideal for networks requiring efficient, low-latency firewall protection. Deep Packet Inspection analyzes the entire data payload within packets, offering granular security by detecting intrusions, malware, and application-level threats, making it essential for high-security environments. Selecting between Stateful and Deep Packet Inspection depends on network size, required security level, performance constraints, and specific threat detection needs to balance speed and comprehensive analysis.
Stateful Inspection Infographic
 libterm.com
libterm.com