Effective Identity and Access Management (IAM) ensures that the right individuals have secure access to your organization's resources while minimizing the risk of unauthorized entry. It involves implementing robust authentication methods, managing user permissions, and continuously monitoring access activities to protect sensitive data. Discover how to strengthen your security posture with advanced IAM strategies by reading the full article.
Table of Comparison
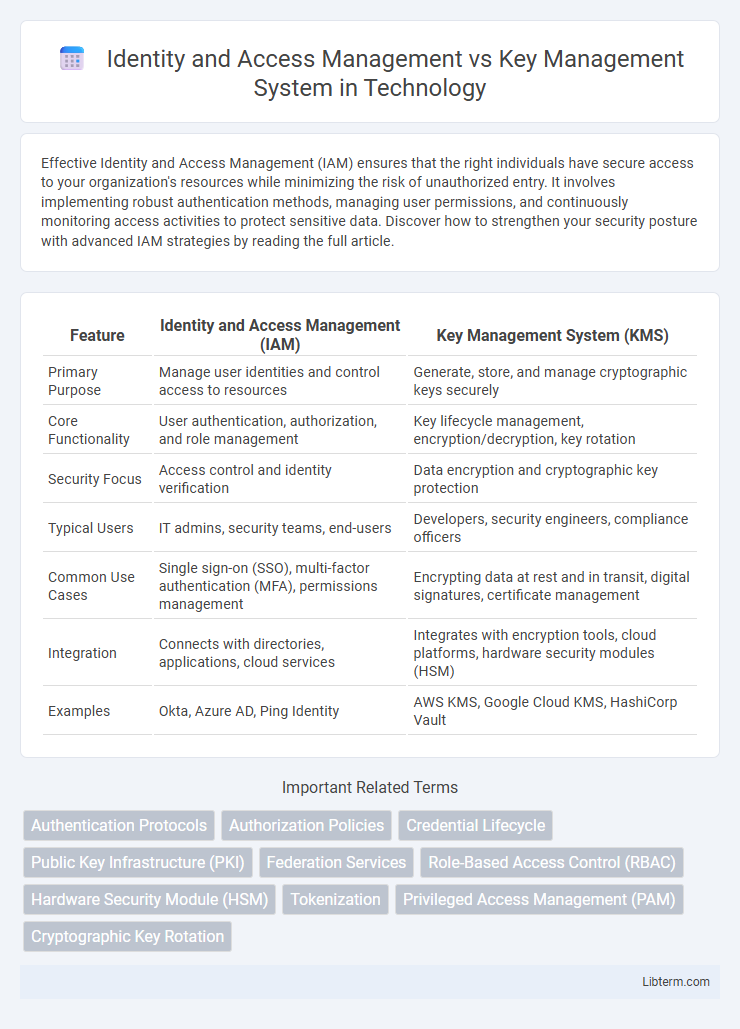
| Feature | Identity and Access Management (IAM) | Key Management System (KMS) |
|---|---|---|
| Primary Purpose | Manage user identities and control access to resources | Generate, store, and manage cryptographic keys securely |
| Core Functionality | User authentication, authorization, and role management | Key lifecycle management, encryption/decryption, key rotation |
| Security Focus | Access control and identity verification | Data encryption and cryptographic key protection |
| Typical Users | IT admins, security teams, end-users | Developers, security engineers, compliance officers |
| Common Use Cases | Single sign-on (SSO), multi-factor authentication (MFA), permissions management | Encrypting data at rest and in transit, digital signatures, certificate management |
| Integration | Connects with directories, applications, cloud services | Integrates with encryption tools, cloud platforms, hardware security modules (HSM) |
| Examples | Okta, Azure AD, Ping Identity | AWS KMS, Google Cloud KMS, HashiCorp Vault |
Introduction to Identity and Access Management (IAM)
Identity and Access Management (IAM) is a framework of policies and technologies that ensures the right individuals access the right resources at the right times for the right reasons, enhancing organizational security. IAM manages digital identities and controls user authentication and authorization across IT environments to prevent unauthorized access. In contrast to Key Management Systems, which focus specifically on cryptographic key lifecycle management, IAM provides a broader scope that encompasses user identity verification and access control processes.
Overview of Key Management Systems (KMS)
Key Management Systems (KMS) are specialized frameworks designed to generate, store, distribute, and control cryptographic keys vital for data encryption and digital security. They ensure secure key lifecycle management, including key creation, rotation, revocation, and archival, thereby protecting sensitive information from unauthorized access. Unlike Identity and Access Management (IAM), which focuses on user authentication and authorization, KMS centers on encrypting data through robust key handling policies and compliance with industry standards such as FIPS 140-2.
Core Functions of IAM
Identity and Access Management (IAM) primarily focuses on verifying user identities, managing user roles, and controlling access permissions to ensure secure and authorized access within an organization. Core functions of IAM include authentication, authorization, user provisioning, single sign-on (SSO), and auditing user activities to maintain compliance and enhance security posture. In contrast, Key Management Systems (KMS) concentrate on the generation, storage, distribution, and lifecycle management of encryption keys, supporting data protection rather than direct user access control.
Primary Features of KMS
Key Management Systems (KMS) primarily focus on the secure generation, storage, distribution, and lifecycle management of cryptographic keys, ensuring data encryption and decryption processes are protected. Unlike Identity and Access Management (IAM) that governs user authentication and authorization, KMS emphasizes centralized control over encryption keys to maintain data confidentiality and integrity across cloud environments and enterprise applications. Core features of KMS include automated key rotation, hardware security module (HSM) integration, audit logging, and policy enforcement for secure key usage.
IAM vs KMS: Key Differences
Identity and Access Management (IAM) primarily controls user authentication, authorization, and access policies to ensure secure resource usage, while Key Management System (KMS) focuses on the generation, storage, and lifecycle management of cryptographic keys. IAM manages digital identities and permissions across systems, whereas KMS protects data confidentiality by securely handling encryption keys. The fundamental difference lies in IAM's role in user identity verification versus KMS's role in safeguarding encryption keys critical for secure data encryption and decryption processes.
Security Implications of IAM and KMS
Identity and Access Management (IAM) ensures secure user authentication and authorization by controlling access to resources based on verified identities, reducing the risk of unauthorized access and insider threats. Key Management Systems (KMS) focus on securing cryptographic keys, enabling encryption and decryption processes while protecting keys from compromise through access policies and hardware security modules (HSMs). Both IAM and KMS complement each other in enterprise security by combining user-centric access controls with robust key protection, minimizing data breaches and enhancing compliance with security standards like GDPR and HIPAA.
Integration of IAM and KMS in Enterprise Environments
Integrating Identity and Access Management (IAM) with Key Management Systems (KMS) in enterprise environments enhances security by ensuring seamless authentication and authorization for cryptographic key usage. This integration allows centralized control over user identities and access policies while securely managing encryption keys, reducing risks of unauthorized data access. Enterprises benefit from unified audit logs and compliance reporting, streamlining governance and strengthening protection against cyber threats.
Common Use Cases for IAM and KMS
Identity and Access Management (IAM) streamlines user authentication, authorization, and role-based access control across enterprise systems to ensure secure and compliant user access. Key Management Systems (KMS) handle the generation, storage, rotation, and lifecycle management of cryptographic keys used for data encryption, digital signing, and secure communication. Common IAM use cases include managing employee access to cloud applications and enforcing least privilege policies, while KMS is essential for protecting sensitive data in databases, securing API keys, and enabling encryption-at-rest and in-transit.
Choosing Between IAM and KMS
Choosing between Identity and Access Management (IAM) and Key Management System (KMS) depends on the security objectives and operational needs of an organization. IAM primarily controls user identities, roles, and access permissions to applications and resources, ensuring secure authentication and authorization processes. KMS focuses on the creation, storage, and management of cryptographic keys used to encrypt and decrypt data, making it essential for protecting sensitive information at the data level.
Future Trends in IAM and KMS Technologies
Future trends in Identity and Access Management (IAM) emphasize the integration of artificial intelligence and machine learning to enhance adaptive authentication and risk-based access controls. Key Management Systems (KMS) are evolving with advancements in quantum-resistant encryption algorithms and automated key lifecycle management to address emerging cybersecurity threats. Both IAM and KMS technologies are converging toward unified platforms that provide seamless, scalable security solutions for cloud-native and hybrid IT environments.
Identity and Access Management Infographic
 libterm.com
libterm.com