Effective identity management ensures the protection of digital identities through secure authentication, access control, and user verification processes. Implementing robust strategies minimizes the risk of identity theft and data breaches while enhancing user experience. Discover how to strengthen your security framework by reading the full article.
Table of Comparison
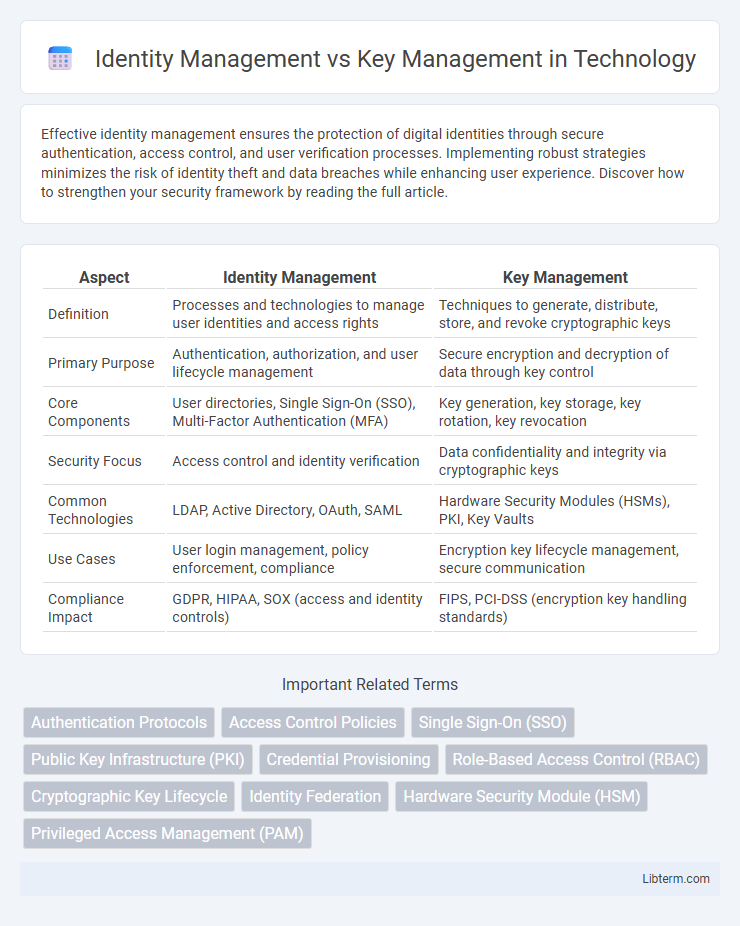
| Aspect | Identity Management | Key Management |
|---|---|---|
| Definition | Processes and technologies to manage user identities and access rights | Techniques to generate, distribute, store, and revoke cryptographic keys |
| Primary Purpose | Authentication, authorization, and user lifecycle management | Secure encryption and decryption of data through key control |
| Core Components | User directories, Single Sign-On (SSO), Multi-Factor Authentication (MFA) | Key generation, key storage, key rotation, key revocation |
| Security Focus | Access control and identity verification | Data confidentiality and integrity via cryptographic keys |
| Common Technologies | LDAP, Active Directory, OAuth, SAML | Hardware Security Modules (HSMs), PKI, Key Vaults |
| Use Cases | User login management, policy enforcement, compliance | Encryption key lifecycle management, secure communication |
| Compliance Impact | GDPR, HIPAA, SOX (access and identity controls) | FIPS, PCI-DSS (encryption key handling standards) |
Introduction to Identity Management and Key Management
Identity Management (IdM) involves the processes and technologies used to authenticate, authorize, and manage user identities and access rights within an organization, ensuring secure and efficient control over digital identities. Key Management focuses on the creation, distribution, storage, rotation, and destruction of cryptographic keys essential for securing encrypted data, enabling confidentiality, integrity, and authentication in communication systems. Both Identity Management and Key Management are critical components of cybersecurity frameworks, often integrated to safeguard sensitive information and maintain compliance with data protection regulations.
Defining Identity Management
Identity Management involves the processes and technologies used to verify, authenticate, and authorize individuals or devices within a system, ensuring secure access control and user accountability. It encompasses identity lifecycle management, including provisioning, authentication mechanisms, and role-based access control to protect sensitive information and maintain compliance. Key Management, by contrast, focuses on the generation, distribution, storage, and lifecycle management of cryptographic keys used to secure data and communication channels.
Understanding Key Management
Key Management involves the secure generation, distribution, storage, and destruction of cryptographic keys essential for protecting data confidentiality and integrity. Unlike Identity Management, which governs user authentication and access rights, Key Management ensures that encryption keys remain protected from unauthorized access and are available when needed for cryptographic operations. Effective Key Management reduces the risk of data breaches by maintaining strict control over key lifecycle processes within security infrastructures.
Core Functions of Identity Management
Identity management primarily focuses on the authentication, authorization, and user lifecycle management to ensure that the right individuals have access to the appropriate resources. It encompasses core functions such as user provisioning, role-based access control, and single sign-on to streamline access and enhance security. Key management, on the other hand, deals with the generation, distribution, storage, and rotation of cryptographic keys critical for data encryption and integrity.
Core Functions of Key Management
Key management primarily involves the generation, distribution, storage, rotation, and destruction of cryptographic keys essential for secure communication and data protection. This core function ensures encryption keys are securely maintained throughout their lifecycle, preventing unauthorized access and maintaining data confidentiality and integrity. Effective key management integrates with identity management systems to link cryptographic keys to specific users or devices, streamlining authentication and access control processes.
Key Differences Between Identity Management and Key Management
Identity Management focuses on the authentication and authorization of users, ensuring secure access control by verifying identities, while Key Management involves the creation, distribution, storage, and lifecycle of cryptographic keys used to protect data. The primary difference lies in Identity Management managing user credentials and roles, whereas Key Management handles encryption keys that safeguard information confidentiality and integrity. Effective security infrastructure requires both systems to work in tandem, addressing user access validation and secure data encryption.
Security Implications of Identity vs Key Management
Identity management secures access by verifying user credentials and managing authentication and authorization policies to prevent unauthorized access and insider threats. Key management protects cryptographic keys used for data encryption and decryption, ensuring confidentiality and integrity by preventing key exposure, theft, or misuse. Both are critical for comprehensive security; identity management controls "who" can access systems, while key management safeguards "what" data remains secure.
Use Cases for Identity Management
Identity Management primarily addresses user authentication, access control, and role-based permissions across enterprise applications, facilitating secure user onboarding, single sign-on (SSO), and compliance with regulatory standards like GDPR and HIPAA. It ensures proper identification and authorization in scenarios such as employee access to internal systems, customer identity verification in financial services, and partner collaboration in supply chain networks. Key Management, in contrast, focuses on cryptographic key lifecycle management used for data encryption, digital signatures, and secure communication but does not handle user identity attributes or access policies directly.
Use Cases for Key Management
Key management is essential for cryptographic operations such as encryption, decryption, and digital signing, enabling secure data storage, transmission, and access control across cloud services and enterprise systems. It supports use cases like managing symmetrical and asymmetrical keys for securing IoT devices, protecting sensitive financial transactions, and ensuring compliance with data protection regulations such as GDPR and HIPAA. Identity management, by contrast, primarily focuses on user authentication and authorization, while key management safeguards cryptographic keys crucial for maintaining data confidentiality and integrity.
Choosing the Right Approach: Identity Management or Key Management
Choosing the right approach between Identity Management and Key Management depends on the specific security needs and organizational goals. Identity Management focuses on authenticating and authorizing users through credentials and access policies, ensuring robust user verification and role-based access control. Key Management centers on cryptographic keys used for data encryption and decryption, essential for maintaining data confidentiality and secure communications in sensitive environments.
Identity Management Infographic
 libterm.com
libterm.com