Session hijacking exploits vulnerabilities in web sessions to gain unauthorized access to a user's account by stealing session cookies or tokens. This attack compromises sensitive information and can lead to identity theft, data breaches, and financial loss. Discover how to protect your online privacy and recognize the signs of session hijacking in the rest of this article.
Table of Comparison
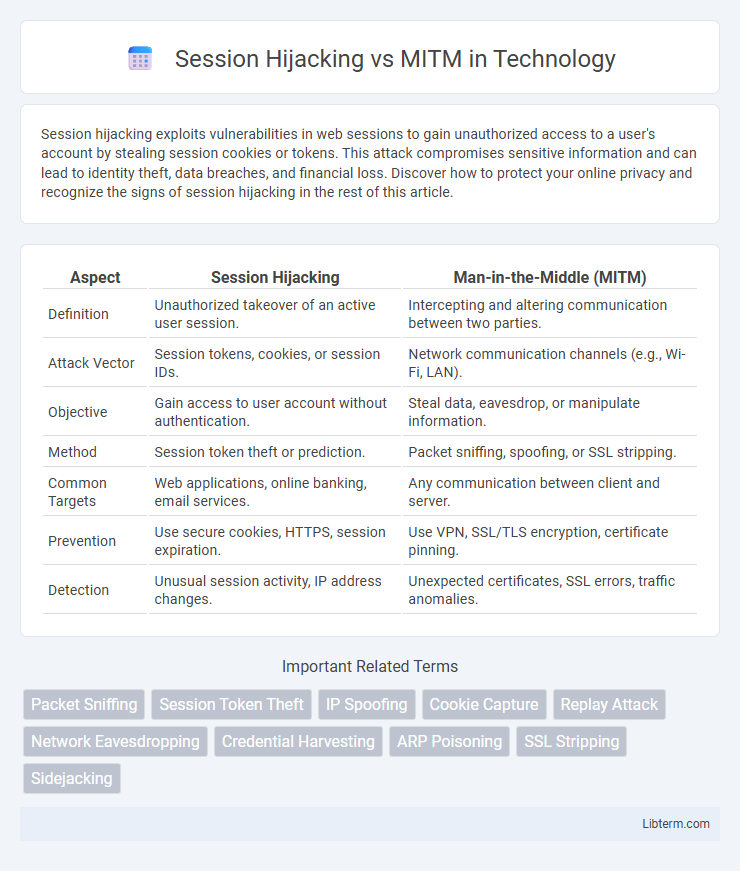
| Aspect | Session Hijacking | Man-in-the-Middle (MITM) |
|---|---|---|
| Definition | Unauthorized takeover of an active user session. | Intercepting and altering communication between two parties. |
| Attack Vector | Session tokens, cookies, or session IDs. | Network communication channels (e.g., Wi-Fi, LAN). |
| Objective | Gain access to user account without authentication. | Steal data, eavesdrop, or manipulate information. |
| Method | Session token theft or prediction. | Packet sniffing, spoofing, or SSL stripping. |
| Common Targets | Web applications, online banking, email services. | Any communication between client and server. |
| Prevention | Use secure cookies, HTTPS, session expiration. | Use VPN, SSL/TLS encryption, certificate pinning. |
| Detection | Unusual session activity, IP address changes. | Unexpected certificates, SSL errors, traffic anomalies. |
Introduction to Session Hijacking and MITM
Session hijacking involves intercepting and taking over an active user session to gain unauthorized access, exploiting session tokens or cookies. Man-in-the-Middle (MITM) attacks occur when an attacker secretly intercepts and possibly alters communication between two parties without their knowledge. Both attacks target communication security but differ as session hijacking focuses on exploiting ongoing sessions, while MITM compromises the communication channel itself.
Understanding Session Hijacking
Session hijacking involves an attacker taking over a valid user session by stealing or predicting a session token, allowing unauthorized access to the victim's account. This exploit targets web applications using cookies or session IDs to maintain authenticated sessions, bypassing the need for user credentials. Unlike Man-in-the-Middle (MITM) attacks that intercept and alter communication between two parties, session hijacking directly exploits the session management mechanism to impersonate the user.
What is a Man-in-the-Middle (MITM) Attack?
A Man-in-the-Middle (MITM) attack involves an attacker secretly intercepting and potentially altering communication between two parties without their knowledge. Unlike session hijacking, which targets an active session to gain unauthorized access, MITM attacks focus on eavesdropping or injecting malicious content during data transmission. Common methods include IP spoofing, DNS spoofing, and SSL stripping, all aimed at compromising confidentiality and integrity of the communication.
Key Differences Between Session Hijacking and MITM
Session hijacking involves an attacker taking over an active user session by stealing session tokens or cookies, enabling unauthorized access to that session without the user's knowledge. Man-in-the-Middle (MITM) attacks intercept and potentially alter communications between two parties by positioning the attacker between the sender and receiver, often capturing sensitive data in real-time. The key difference lies in the attack's focus: session hijacking targets session tokens to impersonate users post-authentication, while MITM attacks compromise the communication channel itself to eavesdrop or manipulate data during transmission.
Common Techniques Used in Session Hijacking
Session hijacking commonly employs techniques such as session fixation, where attackers set a known session ID before user login, and session sidejacking, which involves intercepting unencrypted session cookies over Wi-Fi networks. Cross-site scripting (XSS) is frequently exploited to steal session tokens by injecting malicious scripts into trusted websites. Packet sniffing tools and malware also facilitate unauthorized access by capturing or manipulating active session credentials.
MITM Attack Methods and Tools
Man-in-the-Middle (MITM) attacks involve intercepting and manipulating communications between two parties without their knowledge. Common MITM attack methods include ARP spoofing, DNS spoofing, and HTTPS spoofing, which exploit network vulnerabilities to redirect or capture data. Tools like Ettercap, Cain & Abel, and Wireshark facilitate these attacks by enabling attackers to intercept, analyze, and alter traffic in real-time.
Impact and Risks of Session Hijacking
Session hijacking poses significant risks by allowing attackers to gain unauthorized access to a user's active session, potentially leading to data theft, identity impersonation, and unauthorized transactions. Unlike man-in-the-middle (MITM) attacks, which intercept communications between two parties, session hijacking specifically targets the session token or cookie, compromising session integrity and user authentication. The impact includes financial loss, privacy breaches, and long-term damage to organizational trust and security posture.
Consequences of MITM Attacks
Man-in-the-Middle (MITM) attacks compromise the confidentiality and integrity of communications by intercepting and potentially altering data between two parties without their knowledge. Consequences include theft of sensitive information such as login credentials, financial data, and personal information, leading to identity theft, unauthorized transactions, and significant financial loss. Unlike session hijacking, which targets active user sessions, MITM attacks expose continuous data streams to interception, enabling prolonged eavesdropping and manipulation.
Prevention and Mitigation Strategies
Session hijacking prevention relies on implementing secure cookie attributes like HttpOnly and Secure flags, using HTTPS to encrypt session data, and employing multi-factor authentication to reduce unauthorized access risks. Man-in-the-middle (MITM) attack mitigation includes deploying strong encryption protocols such as TLS, validating SSL/TLS certificates to prevent impersonation, and using VPNs or secure Wi-Fi connections to safeguard data integrity. Both attack types benefit from continuous network monitoring, timely software patching, and user education on recognizing phishing and suspicious activities.
Conclusion: Comparing Session Hijacking and MITM
Session hijacking involves exploiting an active web session to gain unauthorized access, whereas Man-in-the-Middle (MITM) attacks intercept and alter communication between two parties without their knowledge. Both threats compromise data confidentiality and integrity, but session hijacking targets an authenticated session, while MITM intercepts communication at the network level. Effective mitigation requires robust encryption, strong authentication protocols, and real-time monitoring to detect anomalies in session behavior and network traffic.
Session Hijacking Infographic
 libterm.com
libterm.com