Validating webhooks ensure that incoming requests meet specific criteria before they are processed, enhancing the security and integrity of your applications. These webhooks verify the payload and signature to prevent unauthorized or malformed data from triggering actions. Discover how implementing validating webhooks can safeguard your systems and streamline your workflows by reading the full article.
Table of Comparison
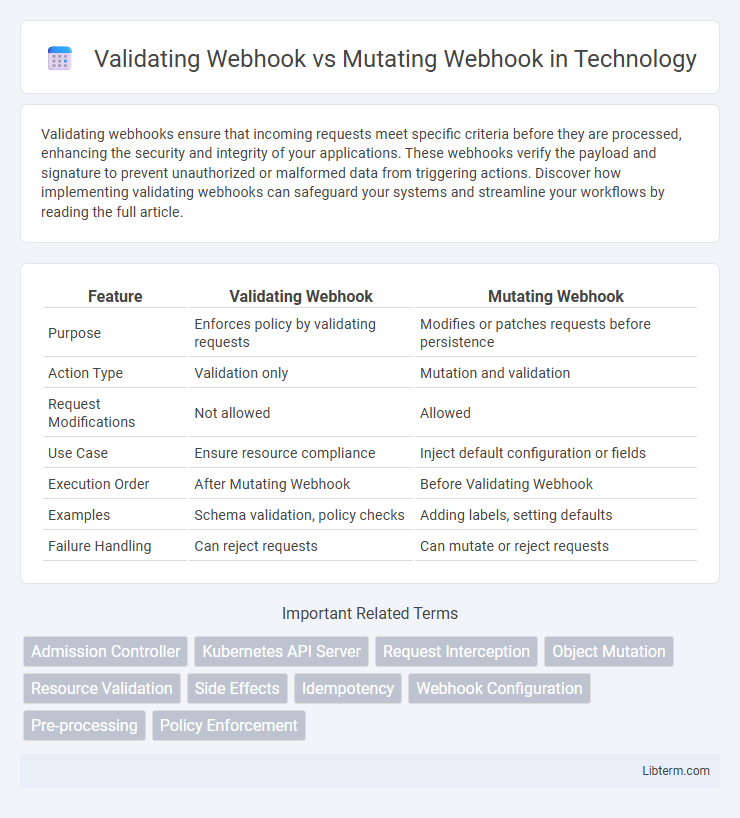
| Feature | Validating Webhook | Mutating Webhook |
|---|---|---|
| Purpose | Enforces policy by validating requests | Modifies or patches requests before persistence |
| Action Type | Validation only | Mutation and validation |
| Request Modifications | Not allowed | Allowed |
| Use Case | Ensure resource compliance | Inject default configuration or fields |
| Execution Order | After Mutating Webhook | Before Validating Webhook |
| Examples | Schema validation, policy checks | Adding labels, setting defaults |
| Failure Handling | Can reject requests | Can mutate or reject requests |
Introduction to Kubernetes Webhooks
Kubernetes webhooks extend cluster functionality by intercepting API server requests for custom processing. Validating webhooks enforce admission policies by inspecting and optionally rejecting requests, ensuring resource compliance before persistence. Mutating webhooks modify incoming requests to apply defaults or transformations, enabling dynamic configuration adjustments during resource creation or updates.
What is a Validating Webhook?
A Validating Webhook in Kubernetes is a type of admission controller that intercepts API requests to validate the object configuration before it is persisted in the cluster. It ensures that all resource changes comply with custom policies and rules, preventing invalid or non-compliant configurations from being admitted. Unlike Mutating Webhooks that modify requests, Validating Webhooks only accept or reject requests based on validation logic.
What is a Mutating Webhook?
A Mutating Webhook in Kubernetes is a type of admission webhook that intercepts requests to the API server and modifies the objects before they are persisted. It allows automatic changes such as adding default values, injecting sidecar containers, or altering configurations to enforce policies and improve workloads. Unlike Validating Webhooks that only approve or reject requests, Mutating Webhooks have the ability to mutate the incoming requests dynamically.
Key Differences: Validating vs Mutating Webhook
Validating Webhooks perform admission control by inspecting and either accepting or rejecting requests based on defined policies without modifying the objects, ensuring compliance and preventing invalid configurations. Mutating Webhooks intercept admission requests to modify or augment Kubernetes resources by applying defaults or transformations before persistence, enabling dynamic configuration adjustments. The key difference lies in Validating Webhooks enforcing rules through validation only, while Mutating Webhooks actively alter resource specifications during the admission process.
Common Use Cases for Validating Webhooks
Validating webhooks are commonly used in Kubernetes to enforce policy compliance by checking incoming API requests before they are persisted, ensuring configurations meet security and operational standards. They help prevent invalid or unauthorized modifications to resources, such as validating label integrity, enforcing resource quotas, or restricting image registries. This contrasts with mutating webhooks that modify the object configuration upon admission, while validating webhooks serve purely as gatekeepers without altering the request.
Common Use Cases for Mutating Webhooks
Mutating webhooks are commonly used for modifying or adding fields to Kubernetes objects during creation or updates, such as injecting sidecars for monitoring or security, setting default values for resource specifications, and enforcing labeling or annotation standards automatically. These webhooks facilitate dynamic customization and policy enforcement without requiring manual intervention or additional deployment steps. Unlike validating webhooks, which only approve or reject requests, mutating webhooks actively transform objects to align with organizational policies and operational best practices.
Workflow Sequence: Request Handling
Validating webhooks intercept API requests after they are authenticated but before they are persisted, allowing the system to approve or reject the request based on custom validation logic. Mutating webhooks operate earlier in the workflow, modifying the request through object transformation before the validation phase to enforce policies or enrich resources. Both webhook types are triggered synchronously during the admission control sequence, ensuring that requests are thoroughly vetted and appropriately altered before final acceptance in Kubernetes clusters.
Best Practices for Webhook Implementation
Validating webhooks enforce policy compliance by inspecting and rejecting invalid requests, ensuring data integrity before changes are persisted, while mutating webhooks modify requests to inject defaults or perform transformations. Best practices for webhook implementation include designing idempotent handlers to handle retries safely, minimizing latency to prevent API server timeouts, and securing communication through TLS and authentication mechanisms. Efficient error handling, logging, and version compatibility checks further enhance the reliability and maintainability of webhook integrations.
Security Considerations for Admission Webhooks
Validating Webhooks enforce security policies by inspecting and approving or rejecting Kubernetes API requests without altering the resource, ensuring that only compliant configurations are admitted. Mutating Webhooks can modify incoming requests to enforce security best practices, such as injecting sidecars or setting defaults, but improper mutation logic may introduce vulnerabilities or inconsistencies. Secure Admission Webhooks require stringent authentication, authorization, and TLS verification to prevent unauthorized access and ensure the integrity of the admission control process.
Choosing the Right Webhook for Your Use Case
Validating Webhooks ensure requests comply with policies by approving or rejecting them, making them ideal for strict validation scenarios like security or data integrity enforcement. Mutating Webhooks modify requests on-the-fly, enabling dynamic changes such as injecting sidecar containers or adjusting configuration before persistence. Choosing the right webhook depends on whether your use case requires enforcement of rules without alteration (Validating) or seamless adjustments to resource definitions (Mutating).
Validating Webhook Infographic
 libterm.com
libterm.com