Virtual Private Networking (VPN) creates a secure and encrypted connection over the internet, protecting your data from hackers and unauthorized access. VPNs help you maintain privacy by masking your IP address and allowing access to restricted content, enhancing your online freedom. Explore the rest of the article to discover how a VPN can safeguard your digital activities and improve your internet experience.
Table of Comparison
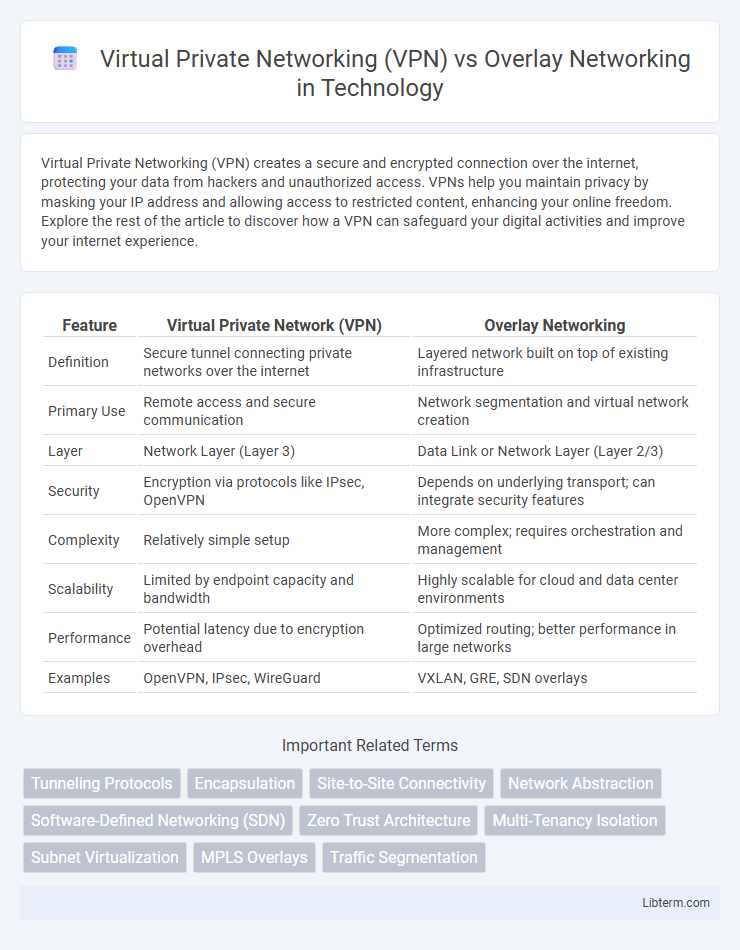
| Feature | Virtual Private Network (VPN) | Overlay Networking |
|---|---|---|
| Definition | Secure tunnel connecting private networks over the internet | Layered network built on top of existing infrastructure |
| Primary Use | Remote access and secure communication | Network segmentation and virtual network creation |
| Layer | Network Layer (Layer 3) | Data Link or Network Layer (Layer 2/3) |
| Security | Encryption via protocols like IPsec, OpenVPN | Depends on underlying transport; can integrate security features |
| Complexity | Relatively simple setup | More complex; requires orchestration and management |
| Scalability | Limited by endpoint capacity and bandwidth | Highly scalable for cloud and data center environments |
| Performance | Potential latency due to encryption overhead | Optimized routing; better performance in large networks |
| Examples | OpenVPN, IPsec, WireGuard | VXLAN, GRE, SDN overlays |
Introduction to Virtual Private Networking (VPN)
Virtual Private Networking (VPN) creates a secure, encrypted tunnel over the internet, enabling private communication between remote users and corporate networks. By masking IP addresses and encrypting data packets, VPNs ensure confidentiality, integrity, and anonymity for online activities. VPNs are essential for remote work, safeguarding sensitive information from cyber threats while providing seamless access to restricted resources.
Overview of Overlay Networking
Overlay networking creates a virtualized network layer that operates on top of existing physical networks, enabling flexible, scalable connectivity by abstracting underlying infrastructure details. This technology supports seamless communication between distributed resources, enhances network segmentation, and simplifies management without the need for physical reconfiguration. Unlike VPNs, which primarily focus on secure remote access, overlay networks provide comprehensive traffic routing, virtualization, and integration options ideal for cloud-native environments and large-scale data centers.
Core Technologies Behind VPNs
Virtual Private Networking (VPN) relies on encryption protocols such as IPsec, OpenVPN, and WireGuard to create secure, encrypted tunnels over public networks, ensuring data confidentiality and integrity. Core VPN technologies include tunneling methods like GRE and L2TP, alongside authentication mechanisms like digital certificates and multi-factor authentication for secure access. In contrast, overlay networking primarily uses encapsulation techniques such as VXLAN and GRE to build virtual networks over physical infrastructure, emphasizing network segmentation and flexibility rather than end-to-end encryption.
How Overlay Networks Operate
Overlay networks operate by creating a virtualized network layer on top of existing physical infrastructures, enabling the abstraction and segmentation of traffic without altering the underlying hardware. These networks use encapsulation protocols such as VXLAN or GRE to tunnel data packets across multiple physical networks, facilitating secure and isolated communication channels. Unlike VPNs that primarily focus on encrypting traffic between endpoints, overlay networks provide enhanced flexibility for cloud-native applications and multi-tenant environments by dynamically managing network topologies and policies.
Security Features: VPN vs Overlay Networking
VPNs provide robust encryption protocols like IPsec and OpenVPN to secure data transmission across public networks, ensuring confidentiality and integrity by creating a secure tunnel. Overlay networking uses encapsulation techniques to abstract underlying network infrastructure, enabling dynamic, software-defined security policies that adapt to complex multi-cloud environments. While VPNs focus on point-to-point secure access, overlay networks offer granular segmentation and micro-segmentation capabilities for enhanced security in distributed architectures.
Performance Comparison: Speed and Latency
Virtual Private Networking (VPN) typically experiences higher latency due to encryption overhead and routing through secure servers, which can reduce overall speed compared to Overlay Networking. Overlay Networking leverages direct peer-to-peer connections and optimized routing protocols to minimize latency and enhance data transfer rates. Performance in Overlay Networking generally outperforms VPNs in speed and latency-sensitive applications such as real-time streaming and online gaming.
Scalability and Flexibility Considerations
VPNs offer secure network connections by creating encrypted tunnels over public networks but often face scalability challenges as the number of users and devices grows, impacting performance and management. Overlay networking, utilizing virtualized network layers built on top of physical infrastructure, provides greater flexibility and scalability through dynamic path selection and seamless integration of diverse network environments. Overlay networks enable more efficient resource allocation and simplified network segmentation, making them better suited for large-scale distributed systems and cloud-based applications.
Use Cases: When to Choose VPN or Overlay Networking
VPNs are ideal for secure remote access to corporate networks, protecting data over public internet by encrypting traffic between endpoints. Overlay networking excels in creating virtual networks across multiple physical infrastructures, supporting dynamic, scalable cloud-native applications and multi-cloud environments. Choose VPN for straightforward, secure point-to-site or site-to-site connections, and overlay networks for complex, programmable network topologies requiring agility and seamless multi-cloud integration.
Cost and Deployment Complexity
Virtual Private Networking (VPN) typically incurs lower upfront costs and simpler deployment compared to Overlay Networking, which often requires specialized hardware or software and more intricate configuration. VPNs use existing public internet infrastructure to create secure tunnels, minimizing investment in additional resources, whereas Overlay Networking involves building virtualized network layers over physical networks, increasing complexity and operational expenses. Enterprises seeking cost-effective and straightforward solutions often prefer VPNs, while Overlay Networking suits scenarios demanding scalable, flexible network segmentation despite higher deployment complexity.
Future Trends in Network Virtualization
Future trends in network virtualization emphasize the convergence of Virtual Private Networking (VPN) and Overlay Networking to enhance security, scalability, and traffic management across distributed cloud environments. Advanced VPN solutions are integrating with overlay networks to provide encrypted, seamless connectivity that supports dynamic, multi-cloud infrastructures and edge computing. Innovations in software-defined networking (SDN) and network function virtualization (NFV) drive the evolution of these technologies, enabling more adaptive, automated, and efficient network virtualization frameworks.
Virtual Private Networking (VPN) Infographic
 libterm.com
libterm.com