Deep Packet Inspection (DPI) is a sophisticated data filtering technique that analyzes the content of data packets transmitted across a network, enabling precise identification and management of network traffic. This process enhances security by detecting malware, enforcing policies, and optimizing network performance through real-time inspection. Discover how DPI can transform your network strategy by reading the rest of the article.
Table of Comparison
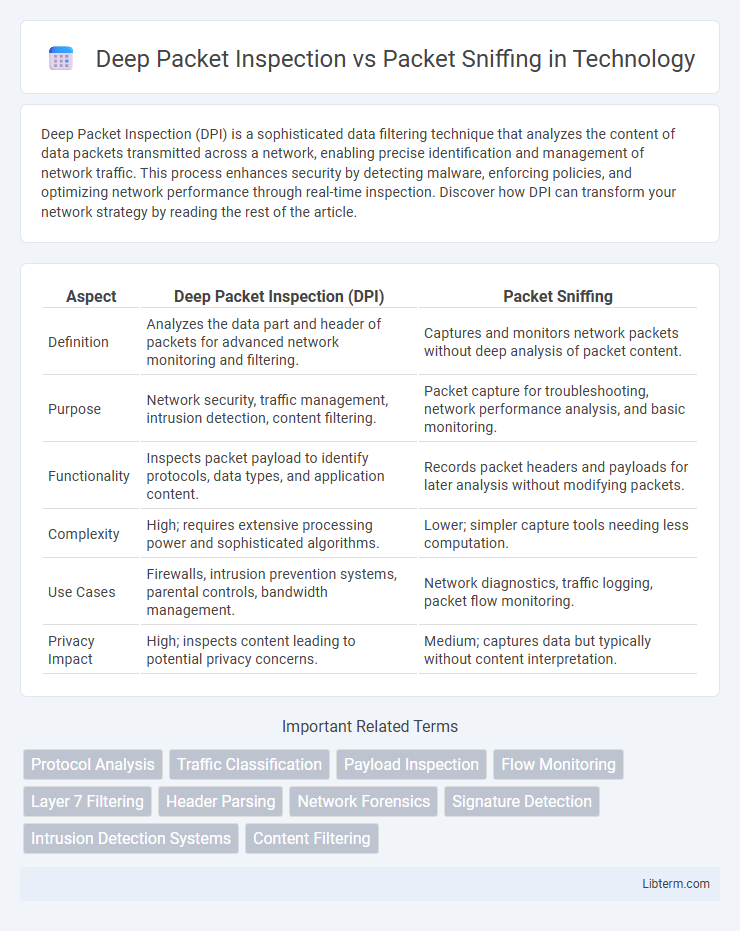
| Aspect | Deep Packet Inspection (DPI) | Packet Sniffing |
|---|---|---|
| Definition | Analyzes the data part and header of packets for advanced network monitoring and filtering. | Captures and monitors network packets without deep analysis of packet content. |
| Purpose | Network security, traffic management, intrusion detection, content filtering. | Packet capture for troubleshooting, network performance analysis, and basic monitoring. |
| Functionality | Inspects packet payload to identify protocols, data types, and application content. | Records packet headers and payloads for later analysis without modifying packets. |
| Complexity | High; requires extensive processing power and sophisticated algorithms. | Lower; simpler capture tools needing less computation. |
| Use Cases | Firewalls, intrusion prevention systems, parental controls, bandwidth management. | Network diagnostics, traffic logging, packet flow monitoring. |
| Privacy Impact | High; inspects content leading to potential privacy concerns. | Medium; captures data but typically without content interpretation. |
Introduction to Network Traffic Analysis
Deep Packet Inspection (DPI) and Packet Sniffing are essential techniques in network traffic analysis, providing insights into data flow and security. DPI examines the content and headers of packets in real-time to identify malicious activity, enforce policies, and optimize network performance. In contrast, Packet Sniffing captures raw packet data for monitoring and troubleshooting without altering or interpreting the packet content extensively.
What is Deep Packet Inspection (DPI)?
Deep Packet Inspection (DPI) is an advanced network packet filtering technique that examines the data part and header of each packet passing through a checkpoint to identify, classify, and manage network traffic based on content. DPI enables detailed analysis for security purposes, such as detecting malware, enforcing data policies, and preventing cyber threats by inspecting packet payloads beyond standard header information. Unlike traditional packet sniffing, which passively monitors network traffic, DPI provides active control by enabling real-time packet modification or blocking through deep content inspection.
What is Packet Sniffing?
Packet sniffing is the process of capturing and analyzing data packets transmitted over a network to monitor and troubleshoot network traffic. It operates at the network layer, intercepting packets without altering their content, and is commonly used for network diagnostics and performance analysis. Packet sniffing tools enable administrators to detect anomalies, monitor data flow, and enhance cybersecurity by identifying unauthorized access or data breaches.
Key Differences Between DPI and Packet Sniffing
Deep Packet Inspection (DPI) analyzes the content of data packets beyond just headers, enabling identification, classification, and filtering based on the payload, whereas Packet Sniffing primarily captures and logs packet data without deep content analysis. DPI operates at multiple layers of the OSI model, providing detailed insights for security, network management, and compliance, while Packet Sniffing is typically limited to passive monitoring for troubleshooting and network diagnostics. The key difference lies in DPI's active packet inspection and filtering capability versus Packet Sniffing's passive data collection and analysis.
Technical Mechanisms of DPI
Deep Packet Inspection (DPI) analyzes the contents of data packets beyond basic header information by examining payload data, which enables detection of application types, protocols, and potential security threats. DPI utilizes signature-based detection, pattern matching, and stateful inspection to classify and filter traffic in real-time, leveraging advanced algorithms and hardware acceleration for high-speed processing. Unlike packet sniffing that passively captures raw packet data, DPI actively interprets and modifies packet flows to enforce policies or mitigate malicious activity at the application layer.
Technical Mechanisms of Packet Sniffing
Packet sniffing captures network traffic by intercepting packets at the data link layer using network interface cards (NICs) in promiscuous mode, allowing the device to receive all packets on the network segment regardless of the intended recipient. This technique analyzes packet headers, including source and destination IP addresses, MAC addresses, and protocol information, without inspecting payload content, enabling basic traffic monitoring and diagnostics. Packet sniffing tools like Wireshark rely on capturing raw packet data for passive surveillance, whereas Deep Packet Inspection (DPI) extends functionality by analyzing payload content for detailed protocol compliance and security assessments.
Use Cases for Deep Packet Inspection
Deep Packet Inspection (DPI) is widely used in network security to identify and block malicious traffic, enforce data loss prevention policies, and optimize bandwidth by analyzing the content of packets beyond basic header information. Unlike packet sniffing, which passively captures data for monitoring or analysis, DPI actively examines the payload to detect intrusions, manage application traffic, and ensure compliance with regulatory standards. Key use cases for DPI include intrusion detection systems (IDS), Quality of Service (QoS) management, and firewall enforcement in enterprise and ISP networks.
Use Cases for Packet Sniffing
Packet sniffing is primarily used for network troubleshooting, allowing administrators to capture and analyze live traffic to identify connectivity issues, monitor bandwidth usage, and detect unauthorized access. It plays a critical role in cybersecurity by helping detect suspicious activities and potential intrusions through real-time packet capture without decrypting content. Packet sniffing is also utilized in network performance analysis to gather data on latency, packet loss, and throughput across various devices and applications.
Privacy and Security Implications
Deep Packet Inspection (DPI) enables granular analysis of packet payloads, allowing detection of malicious content and enforcement of security policies but raises significant privacy concerns due to its capacity to inspect sensitive data beyond headers. Packet Sniffing primarily captures packet headers for network diagnostics and traffic monitoring, offering less intrusion into user content yet still posing risks if intercepted data is mishandled. Both techniques have critical implications for privacy, requiring stringent regulatory frameworks and encryption practices to balance security benefits against potential abuses.
Choosing the Right Tool: DPI vs. Packet Sniffing
Deep Packet Inspection (DPI) provides granular analysis by examining the data payload and headers, making it ideal for identifying specific application-level threats and enforcing policies. Packet Sniffing captures raw network traffic for passive monitoring and troubleshooting, offering a broad overview without content inspection. Selecting the right tool depends on network security needs: use DPI for deep content filtering and intrusion detection, while packet sniffing suits general traffic analysis and performance monitoring.
Deep Packet Inspection Infographic
 libterm.com
libterm.com