Security as Code integrates security practices directly into the software development lifecycle, ensuring vulnerabilities are addressed from the earliest stages. Automating security checks and policy enforcement reduces human error and accelerates compliance, protecting your applications continuously. Explore the rest of the article to learn how implementing Security as Code can strengthen your overall cybersecurity strategy.
Table of Comparison
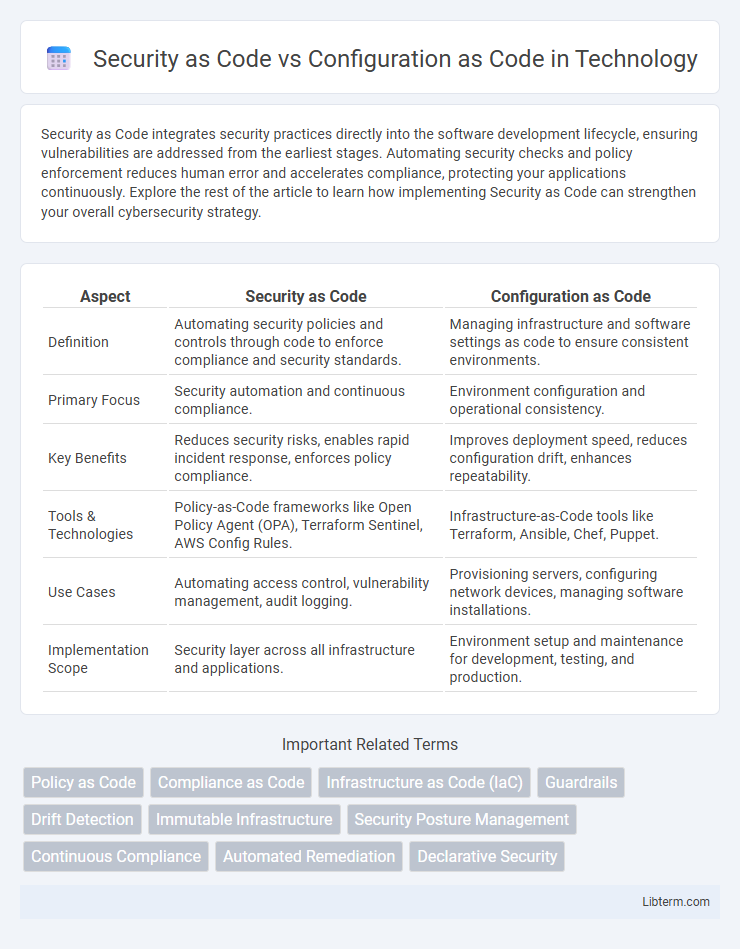
| Aspect | Security as Code | Configuration as Code |
|---|---|---|
| Definition | Automating security policies and controls through code to enforce compliance and security standards. | Managing infrastructure and software settings as code to ensure consistent environments. |
| Primary Focus | Security automation and continuous compliance. | Environment configuration and operational consistency. |
| Key Benefits | Reduces security risks, enables rapid incident response, enforces policy compliance. | Improves deployment speed, reduces configuration drift, enhances repeatability. |
| Tools & Technologies | Policy-as-Code frameworks like Open Policy Agent (OPA), Terraform Sentinel, AWS Config Rules. | Infrastructure-as-Code tools like Terraform, Ansible, Chef, Puppet. |
| Use Cases | Automating access control, vulnerability management, audit logging. | Provisioning servers, configuring network devices, managing software installations. |
| Implementation Scope | Security layer across all infrastructure and applications. | Environment setup and maintenance for development, testing, and production. |
Introduction to Security as Code and Configuration as Code
Security as Code integrates security policies and controls directly into the software development lifecycle, enabling automated enforcement and continuous compliance through code. Configuration as Code involves managing and provisioning infrastructure and application settings using declarative code to ensure consistency, repeatability, and version control. Together, these practices enhance operational efficiency by embedding security and configuration management into automated DevOps workflows.
Core Principles of Security as Code
Security as Code emphasizes embedding security practices directly into the software development lifecycle through automated, version-controlled security policies and controls. It prioritizes continuous security validation, policy enforcement, and threat modeling to ensure proactive risk mitigation and compliance. Configuration as Code manages infrastructure and application settings declaratively, while Security as Code integrates security as an intrinsic component, enabling faster detection and response to vulnerabilities.
Core Principles of Configuration as Code
Configuration as Code (CaC) centers on managing infrastructure and application settings through declarative, version-controlled files that ensure consistency, repeatability, and automation. Core principles include idempotency, enabling the same configuration to be applied repeatedly without side effects, and immutability, promoting predictable environments by avoiding manual changes. Security as Code integrates security policies and controls into this framework, but CaC primarily emphasizes transparency, scalability, and reliability in system configuration management.
Key Differences Between Security as Code and Configuration as Code
Security as Code integrates security policies, controls, and compliance checks directly into the software development lifecycle, ensuring automated enforcement and continuous security testing. Configuration as Code manages infrastructure and software settings through machine-readable files, enabling version-controlled and consistent environment provisioning. The key difference lies in their scopes: Security as Code emphasizes embedding security measures and validation, while Configuration as Code focuses on defining and maintaining system configurations and deployments.
Benefits of Implementing Security as Code
Implementing Security as Code enhances automated security testing, embedding security policies directly into development pipelines to detect vulnerabilities early and reduce risks. It ensures consistent enforcement of compliance standards across environments, minimizing human error and streamlining audits. Integrating Security as Code accelerates incident response through continuous monitoring and real-time alerts, improving overall organizational cybersecurity resilience.
Advantages of Configuration as Code for DevOps
Configuration as Code offers significant advantages for DevOps by enabling consistent, repeatable infrastructure deployments through version-controlled configuration files, which reduce human errors and enhance collaboration across teams. This approach accelerates the delivery pipeline by automating environment setup, ensuring environments are identical across development, testing, and production. Furthermore, Configuration as Code integrates seamlessly with CI/CD tools, improving scalability and compliance by maintaining auditable, transparent infrastructure changes.
Common Tools for Security as Code
Common tools for Security as Code include HashiCorp Vault, which manages secrets and encryption keys, and Aqua Security, providing container security integrated into CI/CD pipelines. Open Policy Agent (OPA) enables policy enforcement across cloud-native environments, while Snyk offers vulnerability scanning for code and dependencies. These tools automate security controls, embed compliance checks early in development, and reduce risks by enforcing security policies through code.
Popular Solutions for Configuration as Code
Popular solutions for Configuration as Code include Terraform, Ansible, and Puppet, which enable automation of infrastructure provisioning and management through declarative code. These tools streamline configuration consistency, reduce errors, and improve scalability across cloud and on-premises environments. Security as Code solutions, like HashiCorp Vault and AWS IAM policies managed via code, complement Configuration as Code by embedding security controls directly into infrastructure definitions.
Challenges and Considerations in Adoption
Security as Code requires integrating security policies directly into development pipelines, which often faces challenges such as toolchain compatibility, real-time threat detection, and balancing automation with manual oversight. Configuration as Code demands consistent environment management, but risks misconfigurations due to complex multi-cloud setups and version control issues. Both approaches necessitate strong collaboration between development, security, and operations teams to address cultural shifts and enforce continuous compliance effectively.
Best Practices for Integrating Both Approaches
Security as Code and Configuration as Code together form a robust framework for infrastructure management and security enforcement. Best practices for integrating both approaches include embedding security policies directly into configuration files, automating compliance checks using CI/CD pipelines, and maintaining version control for auditability. Leveraging tools like HashiCorp Vault for secrets management and Terraform for infrastructure provisioning ensures consistent, repeatable, and secure deployments.
Security as Code Infographic
 libterm.com
libterm.com