LDAP (Lightweight Directory Access Protocol) is a protocol used for accessing and managing directory information services over a network, enabling efficient organization and retrieval of user credentials and resource details. It plays a critical role in authentication and authorization within enterprise environments, supporting seamless integration with various applications and systems. Explore the rest of the article to understand how LDAP can enhance Your network security and streamline directory management.
Table of Comparison
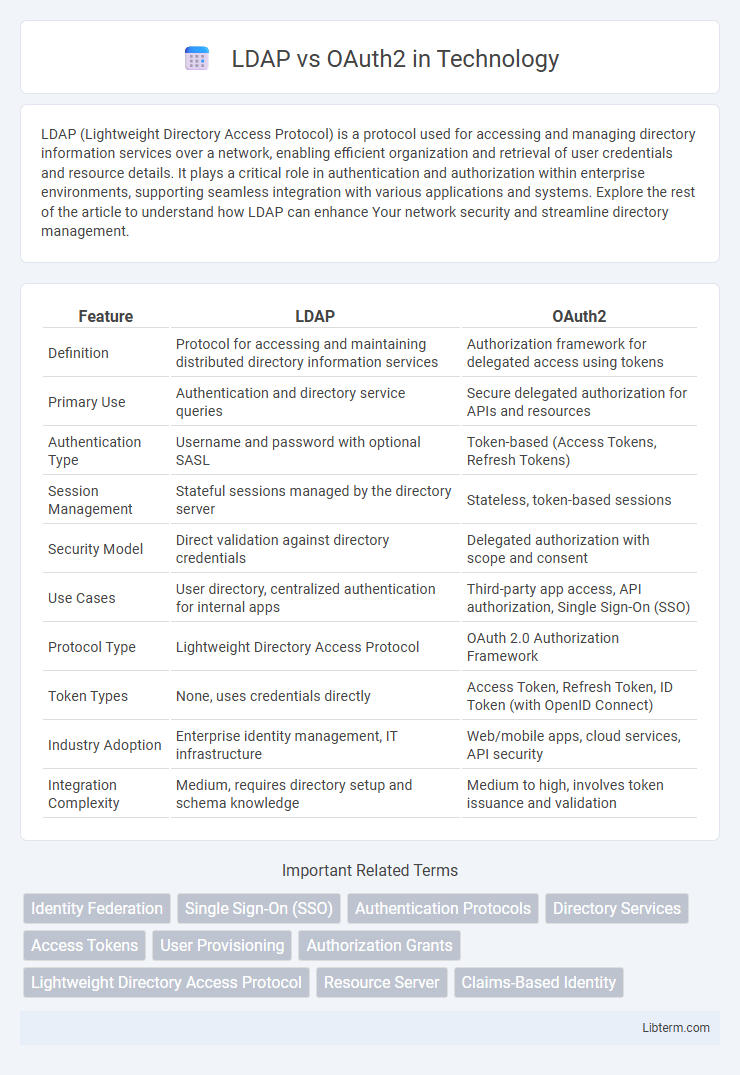
| Feature | LDAP | OAuth2 |
|---|---|---|
| Definition | Protocol for accessing and maintaining distributed directory information services | Authorization framework for delegated access using tokens |
| Primary Use | Authentication and directory service queries | Secure delegated authorization for APIs and resources |
| Authentication Type | Username and password with optional SASL | Token-based (Access Tokens, Refresh Tokens) |
| Session Management | Stateful sessions managed by the directory server | Stateless, token-based sessions |
| Security Model | Direct validation against directory credentials | Delegated authorization with scope and consent |
| Use Cases | User directory, centralized authentication for internal apps | Third-party app access, API authorization, Single Sign-On (SSO) |
| Protocol Type | Lightweight Directory Access Protocol | OAuth 2.0 Authorization Framework |
| Token Types | None, uses credentials directly | Access Token, Refresh Token, ID Token (with OpenID Connect) |
| Industry Adoption | Enterprise identity management, IT infrastructure | Web/mobile apps, cloud services, API security |
| Integration Complexity | Medium, requires directory setup and schema knowledge | Medium to high, involves token issuance and validation |
Introduction to LDAP and OAuth2
LDAP (Lightweight Directory Access Protocol) is a protocol used to access and maintain distributed directory information services over an IP network, commonly employed for user authentication and centralized management of user credentials in enterprise environments. OAuth2 is an open standard authorization framework that enables secure delegated access, allowing third-party applications to obtain limited access to user resources without exposing credentials, frequently utilized in web and mobile applications. Both LDAP and OAuth2 serve authentication and authorization purposes but differ fundamentally in protocol design, use cases, and security models.
Core Concepts and Terminologies
LDAP (Lightweight Directory Access Protocol) is a protocol designed for accessing and maintaining distributed directory information services over an IP network, primarily using entries called objects organized in hierarchical directories. OAuth2 is an authorization framework enabling third-party applications to obtain limited access to user resources on an HTTP service through access tokens without exposing user credentials. Core LDAP terminologies include Distinguished Names (DN), Directory Information Trees (DIT), and Object Classes, whereas OAuth2 centers around concepts like Resource Owner, Client, Authorization Server, Access Token, and Refresh Token.
How LDAP Works
LDAP (Lightweight Directory Access Protocol) operates by querying and modifying directory services that store user information in a hierarchical structure. It uses a client-server model where clients send requests to an LDAP server to authenticate users or retrieve directory data based on Distinguished Names (DNs) and attributes. LDAP provides a stateless protocol, transmitting data over TCP/IP, enabling secure and efficient access to centralized authentication and authorization data within an organization.
How OAuth2 Works
OAuth2 works by allowing users to grant limited access tokens to third-party applications without exposing their passwords, facilitating secure authorization through a series of defined flows such as Authorization Code, Implicit, Resource Owner Password Credentials, and Client Credentials. The protocol relies on an authorization server to issue access tokens after authenticating the user, which client applications then use to access protected resources from resource servers. This token-based approach improves security and flexibility compared to LDAP's direct directory querying by minimizing credential exposure and supporting various access scopes and expiration policies.
Authentication vs Authorization: Key Differences
LDAP primarily serves as an authentication protocol, verifying user credentials against a centralized directory to grant access. OAuth2 functions mainly as an authorization framework, allowing third-party applications to obtain limited access tokens without exposing user credentials. The key difference lies in LDAP handling identity verification, whereas OAuth2 manages delegated permission to resources.
Use Cases for LDAP
LDAP excels in enterprise environments for directory services, enabling centralized authentication and access control across internal networks, particularly within legacy systems and on-premises applications. It is ideal for managing user credentials, group memberships, and permission hierarchies in organizations requiring strict internal security and structured data management. Industries like finance, healthcare, and education often rely on LDAP for robust identity management and compliance with regulatory standards.
Use Cases for OAuth2
OAuth2 is primarily used for delegated authorization in web and mobile applications, enabling users to grant third-party apps limited access to their resources without sharing credentials. It supports single sign-on (SSO) across multiple platforms, enhancing user experience and security in cloud environments. Common use cases include API access management, social logins via providers like Google or Facebook, and integration with microservices architectures.
Security Considerations
LDAP relies on direct directory access with credential validation, posing risks if communication is not encrypted, as sensitive data can be intercepted or exposed. OAuth2 delegates authentication to trusted providers using token-based access, reducing password exposure but requiring secure token handling and validation to prevent replay attacks or token leakage. Implementing TLS for LDAP and enforcing strict token expiration policies for OAuth2 are critical security measures to safeguard authentication processes.
Pros and Cons Comparison
LDAP offers robust directory services with centralized authentication, ideal for managing user credentials within internal networks; its main drawbacks include complexity in setup and limited support for modern web applications. OAuth2 excels in enabling secure, token-based authorization for web and mobile applications, providing seamless third-party access without exposing user credentials, but it requires careful implementation to avoid security vulnerabilities and depends on external authorization servers. Choosing between LDAP and OAuth2 depends on the specific use case: LDAP is better suited for internal, enterprise environments, while OAuth2 is preferred for scalable, internet-facing applications requiring delegated access.
Choosing Between LDAP and OAuth2
Choosing between LDAP and OAuth2 depends on the specific security requirements and infrastructure of your organization. LDAP is ideal for centralized directory services and internal authentication, providing robust access to hierarchical information within enterprises. OAuth2 excels in delegated authorization for third-party applications and APIs, offering flexible, token-based access control suited for modern web and mobile environments.
LDAP Infographic
 libterm.com
libterm.com