Fully Homomorphic Encryption (FHE) allows computation on encrypted data without needing to decrypt it first, ensuring maximum privacy and security. This technology enables secure cloud computing and data processing by keeping your sensitive information confidential throughout operations. Explore the rest of the article to understand how FHE can transform data privacy and secure computing for your needs.
Table of Comparison
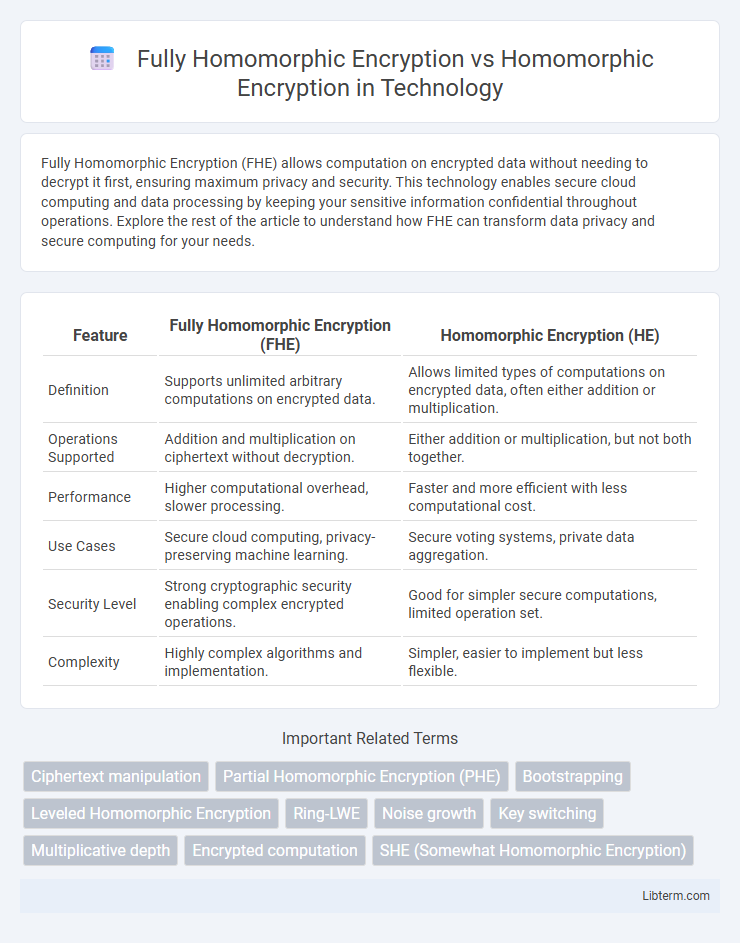
| Feature | Fully Homomorphic Encryption (FHE) | Homomorphic Encryption (HE) |
|---|---|---|
| Definition | Supports unlimited arbitrary computations on encrypted data. | Allows limited types of computations on encrypted data, often either addition or multiplication. |
| Operations Supported | Addition and multiplication on ciphertext without decryption. | Either addition or multiplication, but not both together. |
| Performance | Higher computational overhead, slower processing. | Faster and more efficient with less computational cost. |
| Use Cases | Secure cloud computing, privacy-preserving machine learning. | Secure voting systems, private data aggregation. |
| Security Level | Strong cryptographic security enabling complex encrypted operations. | Good for simpler secure computations, limited operation set. |
| Complexity | Highly complex algorithms and implementation. | Simpler, easier to implement but less flexible. |
Introduction to Homomorphic Encryption
Homomorphic encryption enables computations on encrypted data without decryption, preserving privacy in cloud computing and data analysis. Fully Homomorphic Encryption (FHE) allows unlimited operations on ciphertexts, unlike partial homomorphic encryption, which supports only specific functions such as addition or multiplication. This capability makes FHE crucial for secure, privacy-preserving machine learning and secure multiparty computation applications.
What is Fully Homomorphic Encryption?
Fully Homomorphic Encryption (FHE) is an advanced cryptographic method allowing computations on encrypted data without decryption, preserving privacy throughout processing. Unlike traditional Homomorphic Encryption, which supports either addition or multiplication on ciphertexts, FHE enables arbitrary operations, making it suitable for complex cloud computing and secure data analysis. This capability transforms data security by enabling confidential machine learning, encrypted databases, and private outsourcing of computations without exposing sensitive information.
Key Differences Between Homomorphic Encryption and Fully Homomorphic Encryption
Homomorphic Encryption allows computations to be performed on encrypted data without decryption, but is typically limited to either addition (Partially Homomorphic Encryption) or multiplication (Somewhat Homomorphic Encryption). Fully Homomorphic Encryption (FHE) supports both addition and multiplication operations on ciphertexts, enabling arbitrary computation on encrypted data. The key difference lies in FHE's capability for unlimited operation types on encrypted data, enhancing versatility for complex secure data processing tasks.
Types of Homomorphic Encryption: Partial, Somewhat, and Fully
Homomorphic encryption enables computation on encrypted data without decryption, classified into three main types: Partial, Somewhat, and Fully Homomorphic Encryption (FHE). Partial Homomorphic Encryption supports unlimited operations of only one type--either addition or multiplication--while Somewhat Homomorphic Encryption allows a limited number of both addition and multiplication operations, constrained by noise growth. Fully Homomorphic Encryption overcomes these limitations by permitting unlimited arbitrary computations on ciphertexts, making it the most versatile yet computationally intensive form used in privacy-preserving cloud computing and secure data analysis.
Security Implications: FHE vs Traditional Homomorphic Encryption
Fully Homomorphic Encryption (FHE) enables computations on encrypted data without decryption, providing stronger security guarantees compared to traditional Homomorphic Encryption, which supports limited operations and exposes more attack surfaces. FHE's robust cryptographic constructs prevent leakage of data during complex processing, significantly reducing vulnerabilities to inference and side-channel attacks. The enhanced security of FHE makes it ideal for sensitive applications requiring comprehensive privacy preservation in cloud computing and multi-party data analysis.
Performance and Efficiency Considerations
Fully Homomorphic Encryption (FHE) enables arbitrary computations on encrypted data but incurs significant performance overheads, often resulting in milliseconds to seconds per operation due to complex noise management and bootstrapping processes. In contrast, Somewhat Homomorphic Encryption (SHE) or Partial Homomorphic Encryption (PHE) schemes offer faster encryption and decryption with limited operation support, enhancing efficiency for targeted applications like addition or multiplication only. Performance trade-offs between FHE and homomorphic encryption variants must consider factors such as computational complexity, memory usage, and the required depth of homomorphic operations to balance security with practical efficiency.
Real-World Use Cases for Homomorphic Encryption
Fully Homomorphic Encryption (FHE) enables computations on encrypted data without decryption, supporting complex operations and enhancing data privacy in cloud computing and secure multi-party computations. Homomorphic Encryption (HE), including partially and somewhat homomorphic schemes, is widely used in secure voting systems, privacy-preserving machine learning, and encrypted data analytics where limited types of operations suffice. Real-world applications like secure medical data sharing, confidential financial calculations, and encrypted search demonstrate the transformative potential of homomorphic encryption to protect sensitive information while maintaining functional utility.
Fully Homomorphic Encryption: Current Challenges
Fully Homomorphic Encryption (FHE) enables arbitrary computations on encrypted data without decryption, offering unparalleled data privacy but facing significant challenges such as high computational overhead and large ciphertext sizes. Current research focuses on improving efficiency through optimized schemes like BGV, BFV, and CKKS to reduce latency and resource consumption. Despite advances, practical deployment of FHE remains limited by hardware constraints and the complexity of key management in real-world applications.
Future Trends in Homomorphic Encryption Technologies
Fully Homomorphic Encryption (FHE) represents the pinnacle of homomorphic encryption technologies by enabling arbitrary computations on encrypted data without decryption, significantly advancing data privacy in cloud computing and secure multi-party computations. Future trends indicate increased efforts to optimize FHE schemes for practical deployment through improved computational efficiency, reduced ciphertext expansion, and integration with quantum-resistant cryptographic protocols. Research is also exploring hybrid models combining FHE with other privacy-preserving techniques to balance performance and security for real-world applications across finance, healthcare, and AI.
Conclusion: Choosing the Right Encryption Scheme
Fully Homomorphic Encryption (FHE) enables unlimited computation on encrypted data, making it ideal for complex cloud-based applications requiring maximum security and privacy. In contrast, traditional Homomorphic Encryption (HE) supports limited operations and is more efficient for simpler tasks with lower resource demands. Selecting the right encryption scheme depends on balancing performance needs and security requirements, with FHE suited for advanced, privacy-critical use cases and HE preferred for faster, less intensive processes.
Fully Homomorphic Encryption Infographic
 libterm.com
libterm.com