A tarpit is a natural or artificial sticky trap, often composed of thick mud or asphalt, known for trapping animals or objects that stumble into it. These deceptive pits have historically ensnared unsuspecting creatures by immobilizing their movement through a combination of suction and viscosity. Discover how tar pits reveal ancient ecosystems and what secrets your exploration of their depths might uncover.
Table of Comparison
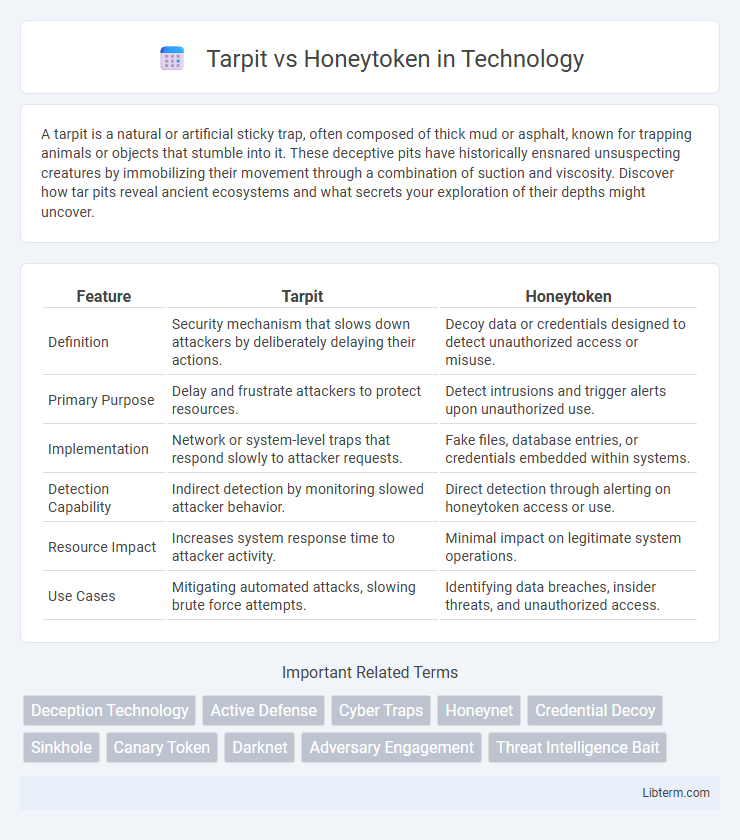
| Feature | Tarpit | Honeytoken |
|---|---|---|
| Definition | Security mechanism that slows down attackers by deliberately delaying their actions. | Decoy data or credentials designed to detect unauthorized access or misuse. |
| Primary Purpose | Delay and frustrate attackers to protect resources. | Detect intrusions and trigger alerts upon unauthorized use. |
| Implementation | Network or system-level traps that respond slowly to attacker requests. | Fake files, database entries, or credentials embedded within systems. |
| Detection Capability | Indirect detection by monitoring slowed attacker behavior. | Direct detection through alerting on honeytoken access or use. |
| Resource Impact | Increases system response time to attacker activity. | Minimal impact on legitimate system operations. |
| Use Cases | Mitigating automated attacks, slowing brute force attempts. | Identifying data breaches, insider threats, and unauthorized access. |
Introduction to Tarpit and Honeytoken
Tarpits slow down attackers by intentionally delaying their progress, creating a time-consuming environment that frustrates intrusion efforts and helps identify malicious activity. Honeytokens are deceptive data artifacts such as fake credentials or files designed to alert administrators when accessed, signaling unauthorized access without delaying attackers. Both tools enhance cybersecurity by detecting and mitigating threats through distinct strategies: tarpit impedes attacker movement while honeytokens trigger alerts on suspicious interactions.
What is a Tarpit?
A tarpit is a cybersecurity defense mechanism designed to slow down an attacker by intentionally delaying their progress, typically by making network connections or services appear unresponsive or sluggish. Unlike a honeytoken, which is a decoy resource or data designed to detect unauthorized access, a tarpit actively absorbs and prolongs the attacker's activity to waste their time and resources. Tarpits are commonly used in email spam filtering and intrusion prevention systems to trap and frustrate automated attacks.
What is a Honeytoken?
A honeytoken is a deceptive security mechanism that acts as a digital bait to detect unauthorized access or malicious activity by embedding fake data or credentials within a system. Unlike a tarpit, which slows down attackers by intentionally delaying responses, honeytokens immediately alert security teams when accessed, enabling rapid identification of breaches. By strategically placing honeytokens in sensitive areas, organizations can monitor and track intrusion attempts without interfering with normal system operations.
Tarpit Mechanism: How It Works
The tarpit mechanism slows down attackers by intentionally delaying their network connections, making reconnaissance and exploitation time-consuming and costly. It traps unauthorized users in a prolonged interaction loop, consuming their resources while minimizing harm to legitimate traffic. Unlike honeytokens, which are deceptive data elements designed to detect unauthorized access, tarpits actively engage and frustrate attackers through response delays.
Honeytoken Mechanism: How It Works
A honeytoken operates by embedding deceptive data, such as fake credentials or bogus database entries, designed to attract and identify unauthorized access attempts. When an attacker interacts with a honeytoken, it triggers alerts that enable security teams to track and analyze the breach without exposing real assets. This mechanism provides early warning and forensic insights, enhancing threat detection within network defenses.
Key Differences Between Tarpit and Honeytoken
Tarpits are cybersecurity mechanisms designed to slow down attackers by intentionally delaying their actions, often through techniques like throttling or resource exhaustion, while honeytokens are deceptive data elements or digital breadcrumbs planted to detect unauthorized access or insider threats. Tarpits primarily focus on hindering attacker progress and buying time for defenders, whereas honeytokens serve as alerts by triggering notifications when accessed or used maliciously. The effectiveness of a tarpit lies in its ability to exhaust attacker resources, whereas honeytokens rely on their stealth and integration within real data to identify breaches.
Use Cases for Tar Pit in Cybersecurity
Tar pits are primarily used in cybersecurity to slow down attackers by deliberately delaying their progress during network intrusions, making it harder for them to execute rapid attacks or gather valuable information quickly. They are effective in defending against brute force attacks and automated scanning by increasing response times and resource consumption on the attacker's end. Unlike honeytokens, which serve as decoys to detect unauthorized access or data exfiltration, tar pits focus on active defense by impeding attacker movements within the network.
Use Cases for Honeytoken in Cyber Threat Detection
Honeytokens serve as deceptive artifacts embedded within digital environments to detect unauthorized access by triggering alerts when interacted with, making them invaluable for insider threat detection and data exfiltration monitoring. Unlike tar pits that slow down attackers by consuming resources, honeytokens offer precise intelligence by identifying malicious activities without hindering legitimate operations. Common use cases include baiting attackers with fake credentials, tracking unauthorized data access, and uncovering lateral movement within networks, enhancing real-time cyber threat detection and response.
Pros and Cons: Tarpit vs Honeytoken
Tarpits slow down attackers by intentionally delaying their progress, effectively buying time for defense systems but can also lead to resource exhaustion and increased system latency. Honeytokens act as deceptive data or credentials designed to alert security teams when accessed, offering precise threat detection without impacting system performance but may generate false positives if improperly deployed. Choosing between tarpit and honeytoken depends on balancing active defense engagement against stealthy threat identification and minimizing operational impact.
Choosing the Right Tool: Tarpit or Honeytoken
Choosing between a tarpit and a honeytoken depends on the specific cybersecurity goals and threat landscape of an organization. Tarpits slow down attackers by intentionally delaying their progress in network interactions, making them ideal for deterring brute-force attacks and analyzing attacker behavior in real-time. Honeytokens, on the other hand, serve as deceptive data elements such as fake credentials or files that alert defenders when accessed, providing early detection and forensic insights without engaging the attacker directly.
Tarpit Infographic
 libterm.com
libterm.com