Symmetric key exchange involves sharing a single secret key between communicating parties to encrypt and decrypt messages efficiently and securely. This method relies on both parties safeguarding the key to prevent unauthorized access and maintain confidentiality. Explore the rest of the article to understand how symmetric key exchange works and its practical applications for your secure communications.
Table of Comparison
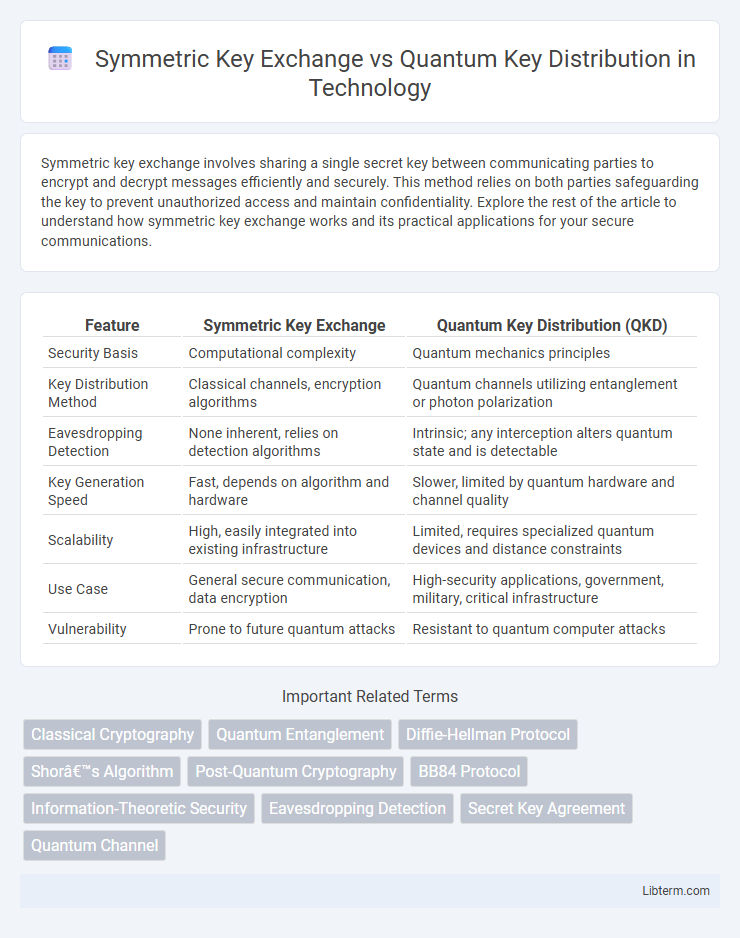
| Feature | Symmetric Key Exchange | Quantum Key Distribution (QKD) |
|---|---|---|
| Security Basis | Computational complexity | Quantum mechanics principles |
| Key Distribution Method | Classical channels, encryption algorithms | Quantum channels utilizing entanglement or photon polarization |
| Eavesdropping Detection | None inherent, relies on detection algorithms | Intrinsic; any interception alters quantum state and is detectable |
| Key Generation Speed | Fast, depends on algorithm and hardware | Slower, limited by quantum hardware and channel quality |
| Scalability | High, easily integrated into existing infrastructure | Limited, requires specialized quantum devices and distance constraints |
| Use Case | General secure communication, data encryption | High-security applications, government, military, critical infrastructure |
| Vulnerability | Prone to future quantum attacks | Resistant to quantum computer attacks |
Introduction to Secure Key Exchange
Symmetric key exchange relies on pre-shared secrets or trusted channels to securely transmit encryption keys, making it vulnerable to interception if the channel is compromised. Quantum key distribution (QKD) uses principles of quantum mechanics, such as entanglement and superposition, to detect eavesdropping and ensure secure key exchange with theoretically unbreakable security. QKD enhances traditional symmetric key exchange methods by enabling the generation of shared keys over insecure channels without risk of interception.
Understanding Symmetric Key Exchange
Symmetric Key Exchange relies on the secure sharing of a single secret key between parties for encrypting and decrypting messages, often using algorithms such as AES for encryption after the key is exchanged. This method depends heavily on secure channels or pre-established keys to prevent interception during key exchange, making it vulnerable to man-in-the-middle attacks if the key is exposed. Understanding symmetric key exchange is essential because it underpins many classical cryptographic systems despite the emerging prominence of quantum-resistant protocols like Quantum Key Distribution (QKD).
Fundamentals of Quantum Key Distribution
Quantum Key Distribution (QKD) leverages principles of quantum mechanics such as superposition and entanglement to enable secure key exchange, ensuring that any eavesdropping attempt alters the quantum states and is thus detectable. Unlike traditional symmetric key exchange methods relying on computational hardness assumptions, QKD provides information-theoretic security by transmitting quantum bits (qubits) over optical fibers or free-space channels. Protocols like BB84 and E91 form the foundation of QKD, utilizing quantum properties to establish encryption keys that are provably secure against any computational attacks, including those from quantum computers.
Security Principles of Symmetric Key Exchange
Symmetric key exchange relies on the principle that both communicating parties share a secret key, which is used for both encryption and decryption, ensuring confidentiality through the secrecy of this key. Its security primarily depends on the difficulty of key interception or brute-force attacks, often enhanced by algorithms such as AES (Advanced Encryption Standard) that provide strong cryptographic resistance. Unlike quantum key distribution, which leverages quantum mechanics to detect eavesdropping, symmetric key exchange lacks inherent mechanisms to identify interception during key exchange, relying instead on secure channels or trusted third parties.
Quantum Key Distribution: How It Works
Quantum Key Distribution (QKD) utilizes principles of quantum mechanics, such as quantum entanglement and superposition, to securely transmit encryption keys between parties. It detects eavesdropping by measuring changes in the quantum states of photons, ensuring that any interception attempts alter the key sequence and are immediately noticed. This method provides unconditional security grounded in physical laws, surpassing conventional symmetric key exchange protocols that rely solely on computational hardness assumptions.
Vulnerabilities in Symmetric Key Exchange
Symmetric key exchange relies on pre-shared secrets or secure channels, making it vulnerable to interception and man-in-the-middle attacks during key distribution. The reliance on computational hardness for encryption algorithms exposes symmetric key exchange to potential breaches by advances in quantum computing. Quantum Key Distribution (QKD) mitigates these vulnerabilities by enabling secure key exchange based on the principles of quantum mechanics, ensuring that any eavesdropping attempt disturbs the quantum states and is thus detectable.
Quantum Advantages: Security and Limitations
Quantum Key Distribution (QKD) leverages the principles of quantum mechanics to provide theoretically unbreakable encryption by detecting any eavesdropping attempts through quantum state disturbances, significantly enhancing security over traditional symmetric key exchange methods. Unlike symmetric key exchange, which relies on computational hardness assumptions vulnerable to advances in computing power, including quantum computers, QKD offers forward secrecy and immunity to future algorithmic breakthroughs. However, QKD faces limitations such as limited transmission distance, high implementation costs, and the need for specialized quantum hardware, which currently restrict its widespread adoption.
Performance and Scalability Comparison
Symmetric key exchange methods typically offer higher performance and lower latency due to their straightforward algorithms and mature implementations, making them suitable for large-scale, high-speed communication systems. Quantum Key Distribution (QKD) provides theoretically unbreakable security by leveraging quantum mechanics but suffers from limited distance ranges and lower key generation rates due to current technological constraints. Scalability challenges in QKD arise from the need for specialized quantum hardware and trusted nodes, whereas symmetric key exchange benefits from widespread infrastructure compatibility and easier integration.
Real-World Applications and Use Cases
Symmetric key exchange methods are widely implemented in securing financial transactions, encrypted messaging, and cloud storage due to their efficiency and compatibility with existing infrastructure. Quantum key distribution (QKD) is increasingly explored for high-security government communications and critical infrastructure protection, leveraging quantum mechanics to detect eavesdropping and enhance security. While symmetric key exchange remains practical for everyday applications, QKD offers superior security for scenarios requiring protection against future quantum computing threats.
The Future of Key Exchange: Classical vs Quantum
Symmetric key exchange relies on pre-shared secret keys and classical cryptographic algorithms, which face increasing vulnerabilities against quantum computing advancements. Quantum key distribution (QKD) leverages principles of quantum mechanics to provide theoretically unbreakable encryption by detecting eavesdropping through quantum states. The future of key exchange likely involves hybrid approaches that integrate QKD with classical methods to enhance security while addressing practical deployment challenges.
Symmetric Key Exchange Infographic
 libterm.com
libterm.com