Public Key Infrastructure (PKI) is a framework that secures digital communications by using a pair of cryptographic keys: a public key and a private key. It enables secure data exchange, authentication, and encryption, protecting sensitive information from unauthorized access. Discover how PKI can enhance your cybersecurity strategy and protect your digital assets by reading the full article.
Table of Comparison
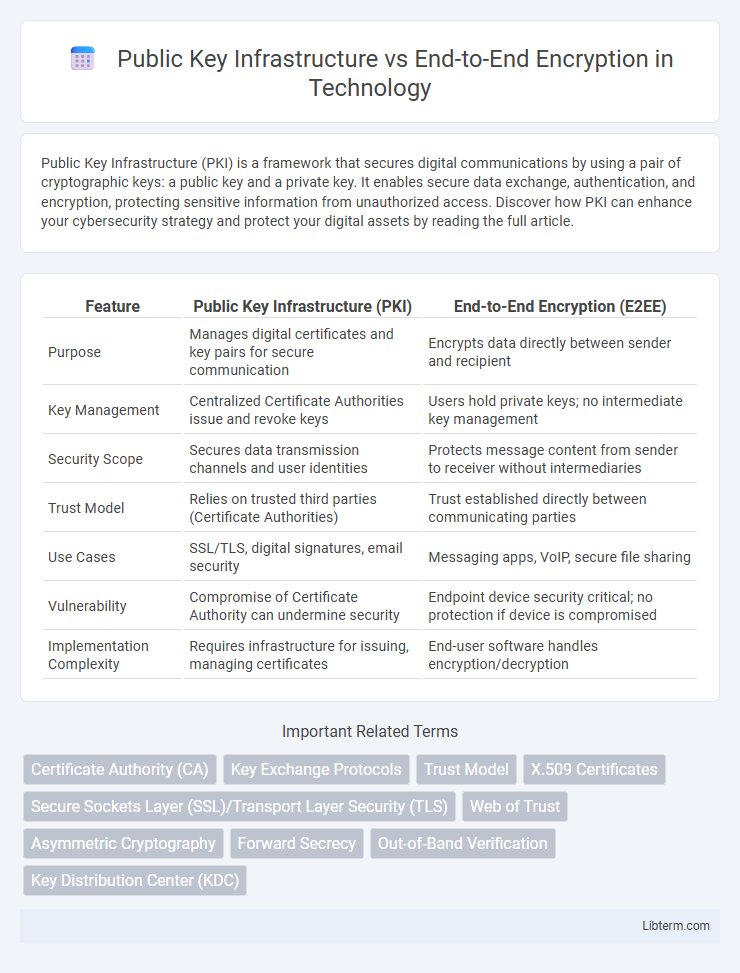
| Feature | Public Key Infrastructure (PKI) | End-to-End Encryption (E2EE) |
|---|---|---|
| Purpose | Manages digital certificates and key pairs for secure communication | Encrypts data directly between sender and recipient |
| Key Management | Centralized Certificate Authorities issue and revoke keys | Users hold private keys; no intermediate key management |
| Security Scope | Secures data transmission channels and user identities | Protects message content from sender to receiver without intermediaries |
| Trust Model | Relies on trusted third parties (Certificate Authorities) | Trust established directly between communicating parties |
| Use Cases | SSL/TLS, digital signatures, email security | Messaging apps, VoIP, secure file sharing |
| Vulnerability | Compromise of Certificate Authority can undermine security | Endpoint device security critical; no protection if device is compromised |
| Implementation Complexity | Requires infrastructure for issuing, managing certificates | End-user software handles encryption/decryption |
Introduction to Public Key Infrastructure and End-to-End Encryption
Public Key Infrastructure (PKI) establishes a framework for secure electronic communication by using a pair of cryptographic keys--a public key for encryption and a private key for decryption--supported by digital certificates and trusted certificate authorities. End-to-End Encryption (E2EE) ensures that data is encrypted on the sender's device and only decrypted on the recipient's device, preventing intermediaries from accessing the information. PKI facilitates secure key distribution and authentication, while E2EE guarantees message confidentiality throughout transmission, providing complementary but distinct security functions.
Core Principles of Public Key Infrastructure
Public Key Infrastructure (PKI) centers on the management of digital certificates and asymmetric key pairs to establish a trusted environment for secure communications and data exchange. It relies on certificate authorities (CAs) to authenticate identities and validate public keys, ensuring data integrity and non-repudiation. In contrast to End-to-End Encryption (E2EE), which protects data exclusively between communicating parties, PKI provides a structured framework for identity verification and key distribution across diverse users and systems.
Fundamentals of End-to-End Encryption
End-to-End Encryption (E2EE) ensures that data is encrypted on the sender's device and decrypted only on the recipient's device, preventing intermediaries from accessing the plaintext information. Unlike Public Key Infrastructure (PKI), which relies on centralized Certificate Authorities to manage and validate digital certificates, E2EE uses cryptographic key pairs generated and exchanged directly between communicating parties. This fundamental approach guarantees confidentiality and data integrity across untrusted networks by eliminating reliance on third-party entities.
Key Differences Between PKI and E2EE
Public Key Infrastructure (PKI) relies on a centralized system of trusted Certificate Authorities (CAs) to issue and manage digital certificates that authenticate user identities and facilitate secure data exchange. End-to-End Encryption (E2EE) ensures that only communicating users hold the cryptographic keys, preventing intermediaries or servers from accessing the plaintext data. PKI provides broad trust models and scalable key management for diverse applications, while E2EE prioritizes direct, private communication by encrypting messages from sender to recipient without third-party access.
Use Cases for Public Key Infrastructure
Public Key Infrastructure (PKI) is essential for secure communication in enterprises by managing digital certificates and encryption keys to authenticate users, devices, and services. It supports use cases such as securing email communications with S/MIME, enabling SSL/TLS for secure web browsing, and ensuring identity verification in VPNs and enterprise networks. PKI's centralized trust model is vital for compliance-driven environments requiring strong authentication and data integrity across multiple stakeholders.
Use Cases for End-to-End Encryption
End-to-End Encryption (E2EE) is crucial for secure communication in messaging apps, ensuring that only the communicating users can read the messages by encrypting data from sender to receiver without intermediate access. It is widely used in personal messaging platforms like WhatsApp and Signal, as well as in secure email services and confidential file-sharing applications, protecting data from interception by servers or third-party entities. Public Key Infrastructure (PKI) supports broader security functions such as digital signatures and certificate management but E2EE specifically addresses privacy needs in direct communications and sensitive data exchanges.
Security Considerations: PKI vs E2EE
Public Key Infrastructure (PKI) offers robust identity verification and centralized management of cryptographic keys, facilitating secure communication across diverse systems but can be vulnerable to certificate authority compromises. End-to-End Encryption (E2EE) ensures that only communicating users can decrypt messages, providing stronger privacy by eliminating intermediaries' access to plaintext data. Security considerations highlight PKI's reliance on trusted third parties versus E2EE's decentralized, user-controlled encryption, impacting threat models and trust assumptions.
Scalability and Implementation Challenges
Public Key Infrastructure (PKI) offers scalable key management by enabling centralized issuance, revocation, and trust validation of digital certificates, but faces implementation challenges such as complex infrastructure setup and reliance on Certificate Authorities. End-to-End Encryption (E2EE) ensures direct secure communication between users without intermediaries, improving privacy but posing scalability issues due to the need for secure key exchange and management on individual devices. The trade-off between PKI's centralized scalability and E2EE's decentralized security model requires balancing infrastructure complexity with user experience and performance.
Compliance and Regulatory Implications
Public Key Infrastructure (PKI) offers a scalable framework for managing digital certificates and encryption keys, ensuring strong authentication and data integrity, which aligns with compliance standards like GDPR, HIPAA, and PCI DSS. End-to-End Encryption (E2EE) enhances data confidentiality by encrypting information directly between sender and receiver, but it may present challenges for regulatory requirements that mandate data access or monitoring, such as those imposed by financial and healthcare regulations. Organizations must carefully evaluate how PKI's versatile key management supports auditability and regulatory transparency, while E2EE's strict privacy safeguards could complicate lawful interception and compliance reporting obligations.
Choosing the Right Approach: PKI or E2EE
Public Key Infrastructure (PKI) provides a scalable framework for managing digital certificates and key distribution, ideal for enterprises requiring robust identity verification and secure communication across multiple users and devices. End-to-End Encryption (E2EE) ensures data privacy by encrypting messages directly between sender and receiver, preventing intermediaries from accessing sensitive information, making it ideal for personal or confidential communications. Selecting the right approach depends on the use case: PKI suits environments needing centralized trust management and authentication, while E2EE is optimal for maximizing data confidentiality in direct user communications.
Public Key Infrastructure Infographic
 libterm.com
libterm.com