A Man-in-the-Middle (MitM) attack occurs when a malicious actor secretly intercepts and possibly alters communication between two parties without their knowledge. This type of cyberattack can compromise sensitive information like login credentials, financial data, and personal messages, posing significant security risks. Discover how you can identify, prevent, and defend against MitM attacks by reading the rest of this article.
Table of Comparison
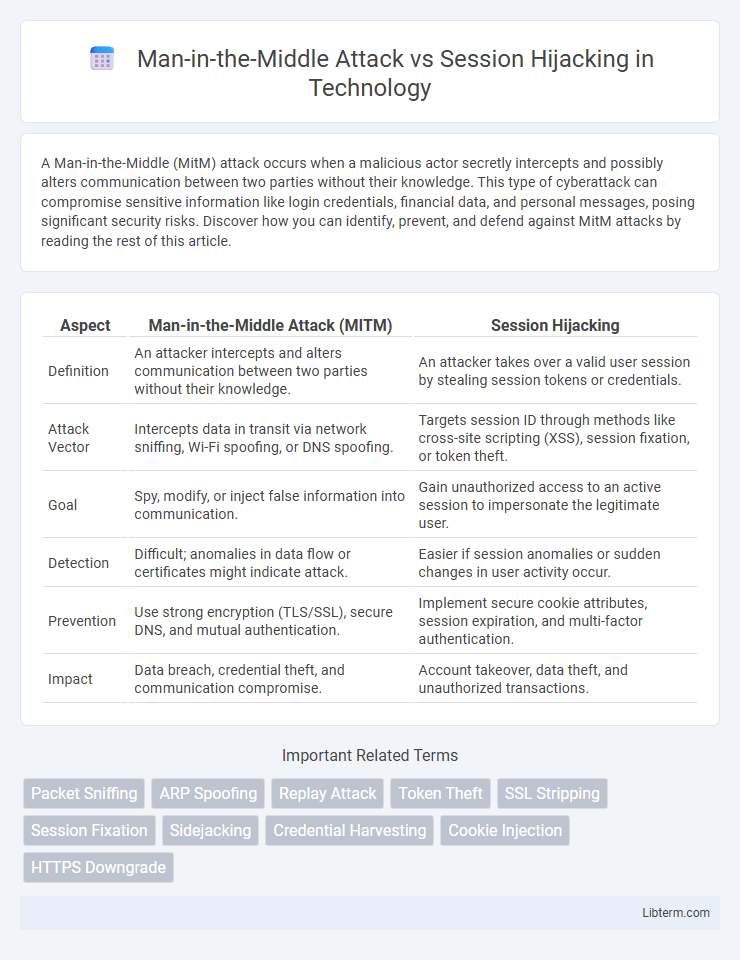
| Aspect | Man-in-the-Middle Attack (MITM) | Session Hijacking |
|---|---|---|
| Definition | An attacker intercepts and alters communication between two parties without their knowledge. | An attacker takes over a valid user session by stealing session tokens or credentials. |
| Attack Vector | Intercepts data in transit via network sniffing, Wi-Fi spoofing, or DNS spoofing. | Targets session ID through methods like cross-site scripting (XSS), session fixation, or token theft. |
| Goal | Spy, modify, or inject false information into communication. | Gain unauthorized access to an active session to impersonate the legitimate user. |
| Detection | Difficult; anomalies in data flow or certificates might indicate attack. | Easier if session anomalies or sudden changes in user activity occur. |
| Prevention | Use strong encryption (TLS/SSL), secure DNS, and mutual authentication. | Implement secure cookie attributes, session expiration, and multi-factor authentication. |
| Impact | Data breach, credential theft, and communication compromise. | Account takeover, data theft, and unauthorized transactions. |
Introduction to Man-in-the-Middle Attacks and Session Hijacking
Man-in-the-Middle (MitM) attacks involve an attacker secretly intercepting and potentially altering communication between two parties without their knowledge, targeting data integrity and confidentiality in transit. Session hijacking focuses specifically on taking over an active session established between a user and a service, exploiting valid session tokens or credentials to impersonate the user. Both attacks threaten online security by breaching trust during data exchanges but differ in scope, with MitM attacks intercepting communication broadly and session hijacking aiming to control ongoing sessions.
Understanding Man-in-the-Middle Attacks
Man-in-the-Middle (MitM) attacks involve an attacker intercepting and potentially altering communication between two parties without their knowledge, often by exploiting vulnerabilities in network protocols or insecure connections. This type of attack enables the attacker to eavesdrop on sensitive data, inject malicious content, or impersonate one of the parties to gain unauthorized access. Understanding MitM attacks is crucial for implementing encryption protocols like TLS and using secure authentication methods to prevent interception and ensure data integrity during transmission.
How Session Hijacking Works
Session hijacking exploits active web sessions by intercepting and taking over a user's authenticated session with a web server, often through stolen session cookies or session IDs. Attackers insert themselves between the user and the server in a communication channel, capturing tokens that grant access without needing to re-authenticate. This enables unauthorized users to impersonate legitimate users, accessing sensitive information or performing unauthorized actions within the hijacked session.
Key Differences Between MITM and Session Hijacking
Man-in-the-Middle (MITM) attacks involve intercepting and altering communication between two parties without their knowledge to steal information or inject malicious content. Session hijacking specifically exploits active user sessions by taking over a session token or cookie to gain unauthorized access without needing to decrypt the entire communication. The key difference lies in MITM's focus on real-time communication interception and manipulation, whereas session hijacking targets pre-established sessions to impersonate legitimate users.
Common Techniques Used in MITM Attacks
Common techniques used in Man-in-the-Middle (MITM) attacks include packet sniffing to intercept data, ARP spoofing to deceive network devices, and DNS spoofing to redirect traffic to malicious sites. Attackers exploit vulnerabilities in unsecured Wi-Fi networks and use HTTPS spoofing to impersonate legitimate websites. These methods enable adversaries to eavesdrop, manipulate, or steal sensitive information during communication sessions.
Methods Employed in Session Hijacking
Session hijacking employs techniques such as session fixation, where attackers set a user's session ID before login, and session sidejacking, which involves intercepting session cookies over unsecured networks. Attackers also use cross-site scripting (XSS) to steal session tokens embedded in web applications. These methods enable unauthorized access to active sessions, compromising user data and application security.
Real-World Examples of MITM vs Session Hijacking
Man-in-the-Middle (MITM) attacks include incidents like the 2013 Superfish adware scandal, where Lenovo laptops intercepted secure HTTPS connections, enabling attackers to eavesdrop on user data. Session hijacking is exemplified by the Firesheep extension attack in 2010, which exploited unsecured Wi-Fi networks to capture session cookies on social media platforms such as Facebook and Twitter. Both attack types demonstrate critical vulnerabilities in network security, with MITM targeting communication interception and session hijacking focusing on seizing authenticated user sessions.
Potential Impact on Users and Organizations
Man-in-the-Middle (MitM) attacks enable attackers to intercept and manipulate communications, leading to data breaches, credential theft, and unauthorized access, severely compromising user privacy and organizational security. Session hijacking exploits active session tokens to impersonate legitimate users, resulting in unauthorized transactions, data loss, and potential financial damage. Both threats can disrupt trust, incur regulatory penalties, and cause significant operational downtime for affected organizations.
Prevention Strategies for Both Attack Types
Implement robust encryption protocols such as SSL/TLS to prevent Man-in-the-Middle (MitM) attacks by securing data in transit. Use multi-factor authentication (MFA) and secure session management practices, including session timeouts and token validation, to mitigate risks of session hijacking. Regularly update software and monitor network traffic with intrusion detection systems to identify and block suspicious activities associated with both attack types.
Conclusion: Protecting Against Cyber Threats
Effective protection against Man-in-the-Middle (MitM) attacks and Session Hijacking revolves around implementing robust encryption protocols such as TLS/SSL and ensuring secure authentication methods like multi-factor authentication (MFA). Employing network security tools like Intrusion Detection Systems (IDS) and maintaining updated software also reduce vulnerabilities exploited by cyber attackers. Organizations must prioritize continuous monitoring and user education to mitigate risks associated with these sophisticated cyber threats.
Man-in-the-Middle Attack Infographic
 libterm.com
libterm.com