Packet filtering firewall monitors and controls network traffic based on predefined security rules, analyzing packet headers to allow or block data transmissions. It operates at the network layer, making decisions without inspecting the packet contents, which enhances speed but might limit security against sophisticated threats. Explore the rest of the article to understand how packet filtering firewalls can safeguard your network while balancing performance and protection.
Table of Comparison
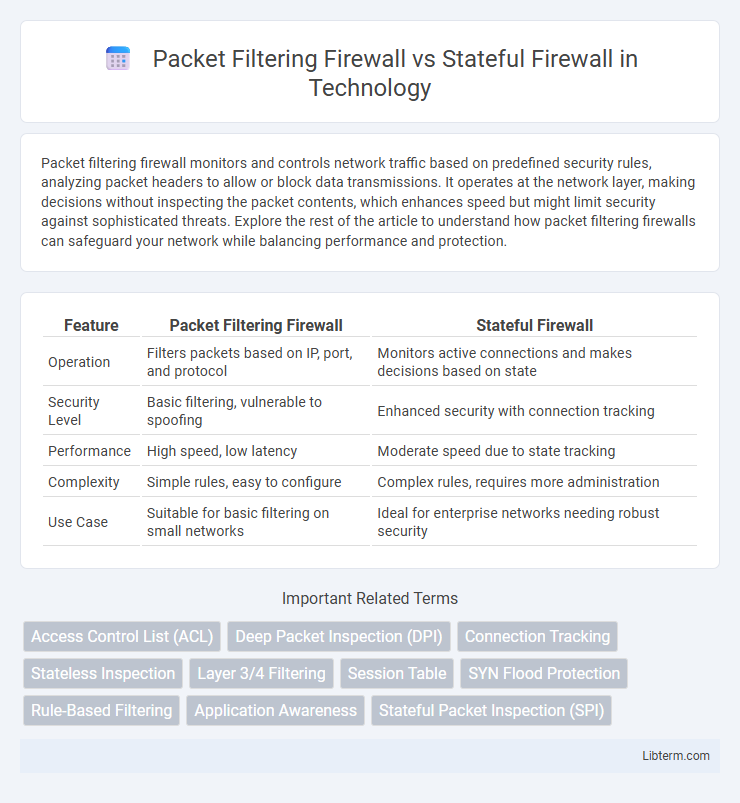
| Feature | Packet Filtering Firewall | Stateful Firewall |
|---|---|---|
| Operation | Filters packets based on IP, port, and protocol | Monitors active connections and makes decisions based on state |
| Security Level | Basic filtering, vulnerable to spoofing | Enhanced security with connection tracking |
| Performance | High speed, low latency | Moderate speed due to state tracking |
| Complexity | Simple rules, easy to configure | Complex rules, requires more administration |
| Use Case | Suitable for basic filtering on small networks | Ideal for enterprise networks needing robust security |
Understanding Packet Filtering Firewalls
Packet filtering firewalls inspect packets based solely on predefined rules related to IP addresses, ports, and protocols without considering the context of the traffic flow. This stateless approach allows for fast processing but lacks the capability to track connection states, making it less effective against sophisticated attacks that exploit packet sequences. Understanding packet filtering firewalls involves recognizing their role as a fundamental security layer that provides basic access control by permitting or denying packets based on static criteria.
Defining Stateful Firewalls
Stateful firewalls monitor the state of active connections and make decisions based on the context of traffic, offering more dynamic security than packet filtering firewalls. Unlike packet filtering firewalls, which inspect packets individually without considering connection state, stateful firewalls track the entire session, enabling more precise filtering based on the connection history. This approach improves protection against unauthorized access and network attacks by understanding the relationship between packets and ensuring only legitimate traffic is allowed.
Core Functional Differences
Packet filtering firewalls inspect packets based solely on header information such as IP addresses, ports, and protocols, enabling or blocking traffic according to predefined rules without maintaining any context of the connection state. Stateful firewalls track the state of active connections by monitoring the sequence of packets within a session, allowing them to detect and prevent unauthorized or suspicious packets that do not match the expected state. The core difference lies in stateful firewalls providing more robust security through connection awareness, whereas packet filtering firewalls offer faster but less comprehensive traffic filtering.
How Packet Filtering Firewalls Work
Packet filtering firewalls inspect packets individually, evaluating headers for source and destination IP addresses, ports, and protocol types to decide whether to allow or block traffic based on predefined rules. They operate at the network layer, making fast decisions without storing session information, which limits their ability to detect complex attacks or track session state. This stateless inspection contrasts with stateful firewalls, which maintain context by monitoring active connections and dynamically adjusting rules accordingly.
How Stateful Firewalls Operate
Stateful firewalls operate by monitoring the full state of active network connections, tracking attributes such as source and destination IP addresses, port numbers, and connection states within a state table. Unlike packet filtering firewalls that examine individual packets in isolation, stateful firewalls analyze packets in the context of an established session, allowing or denying traffic based on the connection's state and rules. This dynamic inspection enables stateful firewalls to provide enhanced security through real-time traffic analysis and prevention of unauthorized access attempts that exploit session vulnerabilities.
Pros and Cons of Packet Filtering Firewalls
Packet filtering firewalls provide a lightweight, fast method for controlling network access by examining packet headers based on predefined rules, making them efficient for simple filtering tasks. Their main advantage lies in low resource consumption and ease of configuration, but they lack the ability to track connection states, which limits their effectiveness against sophisticated attacks. This omission often results in less robust security compared to stateful firewalls that maintain context awareness for ongoing traffic sessions.
Advantages and Disadvantages of Stateful Firewalls
Stateful firewalls monitor the full state of active connections, providing enhanced security by tracking context and allowing or blocking traffic based on connection state and rules. They offer advantages such as improved protection against unauthorized access and reduced false positives compared to packet filtering firewalls, which analyze packets individually without connection awareness. However, stateful firewalls require more system resources, can be more complex to configure, and may struggle with high traffic loads, potentially impacting performance.
Security Implications: Packet Filtering vs Stateful
Packet filtering firewalls inspect packets independently, using predefined rules based on IP addresses, ports, and protocols, which limits their ability to detect complex threats or unauthorized connection states, posing risks of spoofing and session hijacking. Stateful firewalls monitor the full state of active connections, tracking session information and allowing only legitimate packets that belong to established sessions, significantly enhancing security against spoofing, Denial of Service (DoS) attacks, and unauthorized access. This state-awareness enables stateful firewalls to enforce more granular security policies, reducing vulnerabilities inherent in simple packet filtering.
Performance and Resource Utilization Comparison
Packet filtering firewalls offer high performance with minimal resource utilization as they inspect packet headers without maintaining session states, making them efficient for simple filtering tasks. Stateful firewalls consume more resources because they track the state of active connections, enabling deeper analysis and enhanced security but at the cost of increased CPU and memory usage. The trade-off between speed and resource consumption versus security depth is a key consideration when choosing between packet filtering and stateful firewalls in network environments.
Choosing the Right Firewall for Your Network
Packet filtering firewalls inspect packets individually based on predefined rules regarding IP addresses, ports, and protocols, making them efficient for simple, low-resource environments. Stateful firewalls track the state and context of network connections, providing enhanced security by monitoring active sessions and blocking unauthorized access more effectively. Choosing the right firewall depends on network complexity and security requirements; stateful firewalls are preferable for dynamic, high-security networks, while packet filtering firewalls suit smaller, less demanding setups.
Packet Filtering Firewall Infographic
 libterm.com
libterm.com