Replay attacks exploit intercepted data by maliciously retransmitting valid data to gain unauthorized access or disrupt communication. Protecting Your systems requires robust authentication protocols and time-sensitive tokens to detect and prevent these repeated transmissions. Explore the following sections to understand how to safeguard Your network against replay attacks effectively.
Table of Comparison
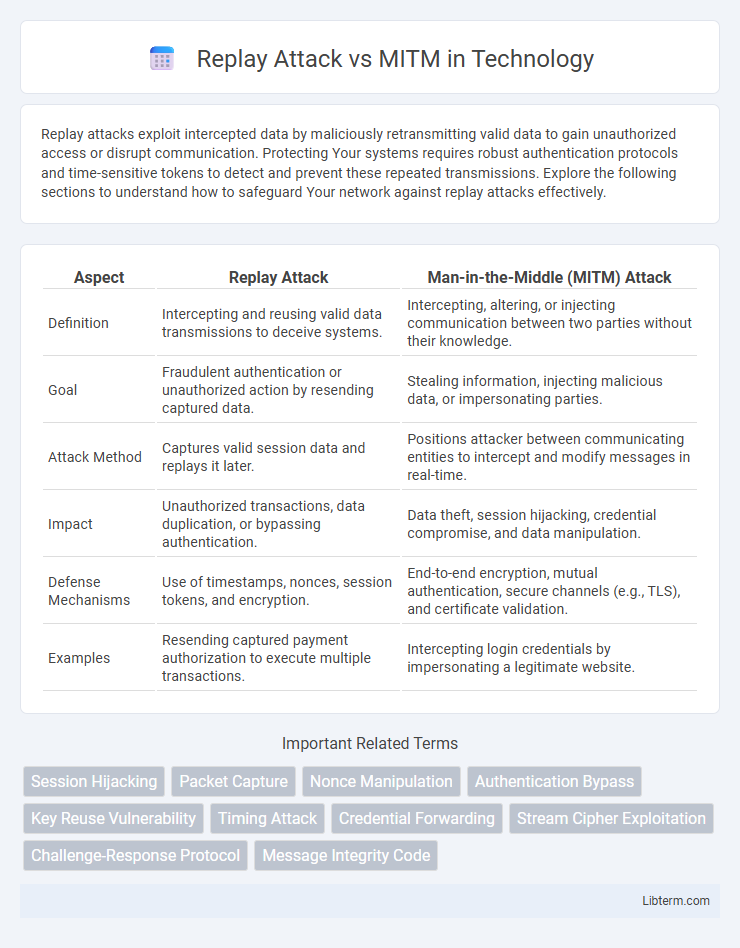
| Aspect | Replay Attack | Man-in-the-Middle (MITM) Attack |
|---|---|---|
| Definition | Intercepting and reusing valid data transmissions to deceive systems. | Intercepting, altering, or injecting communication between two parties without their knowledge. |
| Goal | Fraudulent authentication or unauthorized action by resending captured data. | Stealing information, injecting malicious data, or impersonating parties. |
| Attack Method | Captures valid session data and replays it later. | Positions attacker between communicating entities to intercept and modify messages in real-time. |
| Impact | Unauthorized transactions, data duplication, or bypassing authentication. | Data theft, session hijacking, credential compromise, and data manipulation. |
| Defense Mechanisms | Use of timestamps, nonces, session tokens, and encryption. | End-to-end encryption, mutual authentication, secure channels (e.g., TLS), and certificate validation. |
| Examples | Resending captured payment authorization to execute multiple transactions. | Intercepting login credentials by impersonating a legitimate website. |
Introduction to Replay Attack and MITM
Replay attacks involve intercepting and retransmitting valid data to impersonate a user or gain unauthorized access without altering the original message, exploiting weaknesses in authentication protocols. Man-in-the-Middle (MITM) attacks occur when an attacker secretly intercepts and possibly alters communication between two parties who believe they are directly communicating, compromising data confidentiality and integrity. Both attacks target network security but differ in their methods: replay attacks exploit repeated message transmission, while MITM involves active interception and manipulation.
Understanding Replay Attacks
Replay attacks involve intercepting valid data transmissions and fraudulently repeating them to gain unauthorized access or perform transactions without detection. Unlike Man-in-the-Middle (MITM) attacks that modify or alter communication between parties, replay attacks strictly resend captured messages, exploiting the lack of time-stamping or sequence verification in protocols. Protecting against replay attacks requires implementing nonce values, timestamps, and cryptographic challenges to ensure message freshness and authenticity.
What is a Man-in-the-Middle (MITM) Attack?
A Man-in-the-Middle (MITM) attack occurs when an attacker secretly intercepts and alters communication between two parties without their knowledge, aiming to steal sensitive information or inject malicious content. Unlike replay attacks that simply resend captured data to gain unauthorized access, MITM attacks actively manipulate the data flow, enabling real-time eavesdropping and data tampering. Effective defenses against MITM include strong encryption protocols such as TLS/SSL, mutual authentication, and the use of certificate pinning to verify communication endpoints.
Key Differences: Replay Attack vs MITM
Replay attacks involve intercepting and retransmitting valid data to deceive a system without altering the original message, primarily exploiting authentication weaknesses. Man-in-the-Middle (MITM) attacks intercept and potentially modify communications between two parties, allowing attackers to manipulate, eavesdrop, or inject malicious data in real-time. The key difference lies in replay attacks replicating previously captured data without modification, while MITM attacks actively intercept and alter ongoing communications.
Common Techniques Used in Replay Attacks
Replay attacks commonly utilize techniques such as packet capture and retransmission, where attackers intercept legitimate communication data and resend it to gain unauthorized access or disrupt network operations. Time-stamping manipulation and session key reuse are often exploited to bypass authentication mechanisms, enabling attackers to impersonate legitimate users. These methods differ from Man-in-the-Middle (MITM) attacks, which involve active interception and alteration of communication rather than mere repetition.
How MITM Attacks Are Executed
Man-in-the-Middle (MITM) attacks are executed by intercepting communication between two parties without their knowledge, allowing the attacker to eavesdrop, alter, or inject malicious data. Attackers often use techniques such as packet sniffing, session hijacking, or DNS spoofing to position themselves between the victim and the target server. Unlike replay attacks that reuse captured data, MITM actively manipulates ongoing communication, making detection more complex and enabling credential theft, data tampering, and unauthorized access.
Real-World Examples of Replay Attacks
Replay attacks involve intercepting and retransmitting valid data to fraudulently repeat a transaction, as seen in the 2018 Tesla key fob hack where attackers replayed stored signals to unlock vehicles. Unlike man-in-the-middle (MITM) attacks that actively intercept and alter communications in real-time, replay attacks rely on resending previously captured data without modification. High-profile examples include the 2013 Target breach, where attackers exploited captured credentials to replay login sessions and gain unauthorized access to payment systems.
Notable MITM Attack Incidents
Notable MITM attack incidents include the 2011 DigiNotar breach, where attackers intercepted communications to issue fraudulent SSL certificates, compromising secure internet traffic. The 2013 NSA PRISM program leaked details of widespread MITM surveillance on internet users worldwide, exposing vulnerabilities in data confidentiality. These incidents highlight how MITM attacks intercept and manipulate communication in real-time, differing fundamentally from replay attacks that retransmit captured data without alteration.
Prevention Strategies for Replay Attacks
Preventing replay attacks involves implementing robust timestamping and nonce mechanisms to ensure message freshness and uniqueness, effectively blocking attackers from reusing valid data packets. Utilizing strong cryptographic protocols like TLS with mutual authentication and session tokens further safeguards communication channels against unauthorized replay attempts. Network-level defenses such as strict access controls and anomaly detection systems help identify and mitigate suspicious re-transmission behaviors characteristic of replay attacks.
Effective Defenses Against MITM Attacks
Effective defenses against Man-in-the-Middle (MITM) attacks include the implementation of strong encryption protocols such as TLS/SSL to ensure secure communication channels. Multi-factor authentication (MFA) and robust public key infrastructure (PKI) prevent attackers from intercepting or impersonating legitimate users. Network-level protections like virtual private networks (VPNs) and intrusion detection systems (IDS) detect and block suspicious activities, significantly reducing the risk of MITM exploits.
Replay Attack Infographic
 libterm.com
libterm.com