Fuzz testing is an automated software testing technique that involves inputting large amounts of random data, or fuzz, into a program to identify vulnerabilities and bugs. This method helps ensure your software can handle unexpected or malformed inputs without crashing or exposing security flaws. Explore the rest of this article to learn how fuzz testing can safeguard your applications effectively.
Table of Comparison
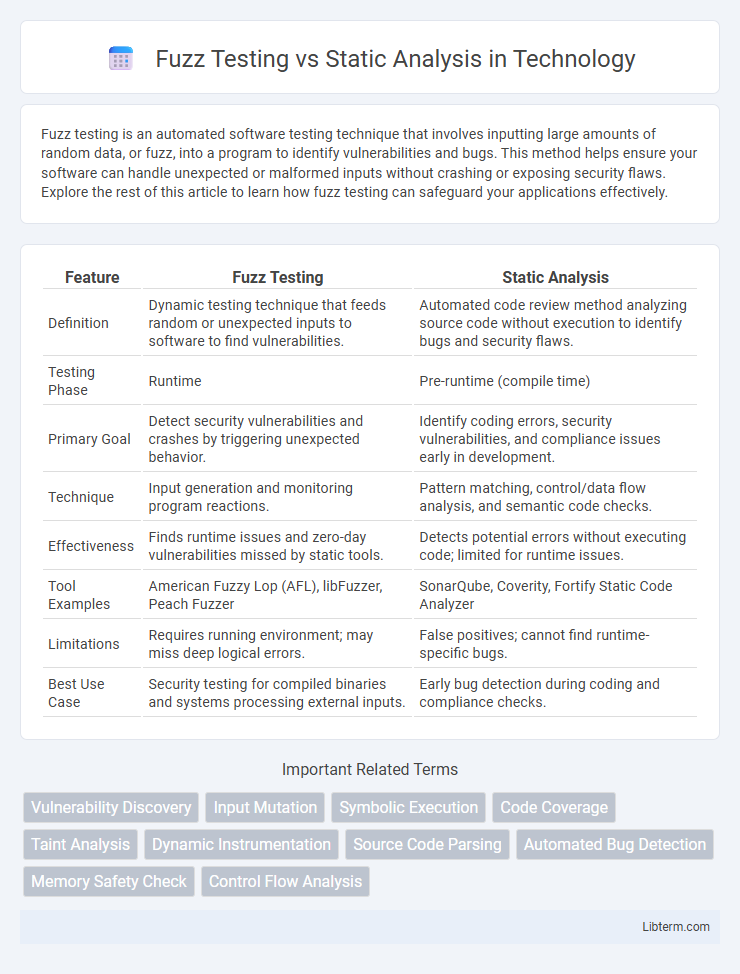
| Feature | Fuzz Testing | Static Analysis |
|---|---|---|
| Definition | Dynamic testing technique that feeds random or unexpected inputs to software to find vulnerabilities. | Automated code review method analyzing source code without execution to identify bugs and security flaws. |
| Testing Phase | Runtime | Pre-runtime (compile time) |
| Primary Goal | Detect security vulnerabilities and crashes by triggering unexpected behavior. | Identify coding errors, security vulnerabilities, and compliance issues early in development. |
| Technique | Input generation and monitoring program reactions. | Pattern matching, control/data flow analysis, and semantic code checks. |
| Effectiveness | Finds runtime issues and zero-day vulnerabilities missed by static tools. | Detects potential errors without executing code; limited for runtime issues. |
| Tool Examples | American Fuzzy Lop (AFL), libFuzzer, Peach Fuzzer | SonarQube, Coverity, Fortify Static Code Analyzer |
| Limitations | Requires running environment; may miss deep logical errors. | False positives; cannot find runtime-specific bugs. |
| Best Use Case | Security testing for compiled binaries and systems processing external inputs. | Early bug detection during coding and compliance checks. |
Introduction to Fuzz Testing and Static Analysis
Fuzz testing involves automated input generation to identify software vulnerabilities by exposing unexpected or malformed data, enabling dynamic detection of runtime errors. Static analysis examines source code or binaries without execution, detecting potential security flaws, coding errors, and compliance issues through pattern recognition and rule-based analysis. Combining both techniques enhances software security by capturing diverse vulnerability types early in the development lifecycle.
Fundamental Differences Between Fuzz Testing and Static Analysis
Fuzz testing involves dynamically inputting random or unexpected data into software to identify security vulnerabilities or crashes during execution, whereas static analysis examines source code without running the program to detect potential errors and security issues. Fuzz testing relies on runtime behavior and is effective in uncovering memory corruption and logic bugs, while static analysis uses pattern matching and data flow analysis for early detection of coding errors, vulnerabilities, and adherence to coding standards. The fundamental difference lies in fuzz testing's dynamic, execution-based approach versus static analysis's code-based, non-executing inspection methodology.
How Fuzz Testing Works
Fuzz testing operates by automatically generating and injecting numerous random or semi-random inputs into software to identify vulnerabilities, crashes, and unexpected behaviors. This dynamic testing method monitors program execution in real-time, uncovering security flaws that often evade static analysis by exploring edge cases and inputs beyond predefined code paths. Fuzz testing tools like AFL (American Fuzzy Lop) and libFuzzer enhance software robustness by continuously evolving input patterns based on observed feedback during runtime.
How Static Analysis Works
Static analysis works by examining source code or binaries without executing the program, using automated tools to detect potential vulnerabilities, coding errors, and security flaws early in the development lifecycle. It relies on pattern recognition, control flow analysis, and data flow analysis to identify issues such as buffer overflows, null pointer dereferences, and insecure coding practices. This method enables developers to enforce coding standards, reduce bugs, and improve software security before runtime testing or deployment.
Strengths of Fuzz Testing
Fuzz testing excels at uncovering runtime vulnerabilities by generating a vast range of unexpected or malformed inputs to trigger crashes, memory leaks, and buffer overflows. Its dynamic nature allows detection of complex, environment-dependent bugs that static analysis tools might miss due to code abstraction limitations. Fuzz testing is particularly effective for security-critical applications where uncovering zero-day exploits requires uncovering deep execution path errors.
Strengths of Static Analysis
Static analysis excels at detecting security vulnerabilities, coding errors, and compliance issues early in the development lifecycle by examining source code without execution. It provides comprehensive coverage of all code paths, enabling identification of potential defects that might be missed during dynamic testing methods such as fuzz testing. Integration with CI/CD pipelines enhances automated code quality enforcement, reducing the risk of costly bugs and improving maintainability.
Limitations and Challenges of Fuzz Testing
Fuzz testing faces limitations in effectively covering deep semantic code paths and detecting vulnerabilities within complex input structures, often resulting in shallow exploration of application logic. It struggles with stateful or highly interactive systems where maintaining context between inputs is crucial, leading to incomplete vulnerability detection. The technique requires significant computational resources and domain-specific input generation to improve coverage, presenting challenges in scalability and efficiency.
Limitations and Challenges of Static Analysis
Static analysis faces limitations such as high false-positive rates and difficulty in detecting runtime-specific issues like memory leaks or concurrency errors. It struggles with analyzing dynamically generated code and may miss vulnerabilities that only manifest during program execution. The complexity of interpreting large codebases often leads to scalability challenges and incomplete coverage.
When to Use Fuzz Testing vs Static Analysis
Fuzz testing is ideal for identifying runtime vulnerabilities by generating random inputs to test software behavior under unexpected conditions, making it effective during dynamic testing phases. Static analysis excels at early-stage code inspection, detecting syntactic errors, security flaws, and coding standard violations without executing the program, suitable for continuous integration workflows. Combining fuzz testing with static analysis provides comprehensive coverage by uncovering both surface-level bugs and deep logic errors across the development lifecycle.
Integrating Fuzz Testing and Static Analysis in the Development Lifecycle
Integrating fuzz testing and static analysis in the development lifecycle enhances software security and reliability by combining dynamic vulnerability detection with comprehensive code quality assessment. Fuzz testing identifies runtime errors and unexpected behaviors through automated input generation, while static analysis detects code defects, security flaws, and compliance issues early in development without executing the program. Utilizing both techniques in continuous integration pipelines accelerates remediation cycles, improves coverage of security vulnerabilities, and enforces coding standards efficiently.
Fuzz Testing Infographic
 libterm.com
libterm.com