Plaintext refers to unencrypted information that is easily readable and understood by humans or computers without requiring decryption. It serves as the original data before any encryption or encoding processes are applied to protect its confidentiality. Explore the rest of the article to learn how plaintext is transformed into secure ciphertext and its role in data security.
Table of Comparison
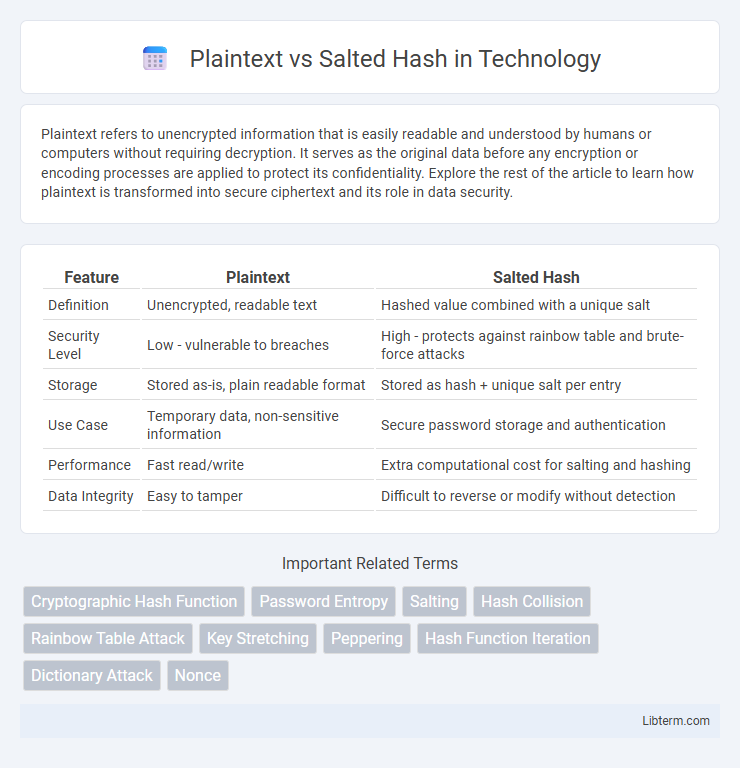
| Feature | Plaintext | Salted Hash |
|---|---|---|
| Definition | Unencrypted, readable text | Hashed value combined with a unique salt |
| Security Level | Low - vulnerable to breaches | High - protects against rainbow table and brute-force attacks |
| Storage | Stored as-is, plain readable format | Stored as hash + unique salt per entry |
| Use Case | Temporary data, non-sensitive information | Secure password storage and authentication |
| Performance | Fast read/write | Extra computational cost for salting and hashing |
| Data Integrity | Easy to tamper | Difficult to reverse or modify without detection |
Understanding Plaintext: The Basics
Plaintext refers to raw, unencrypted data that is directly readable and understandable without any transformation. It is the original form of input before applying any cryptographic functions such as hashing, making it highly vulnerable to unauthorized access. Understanding plaintext is crucial in security frameworks, as storing or transmitting sensitive data in plaintext exposes it to potential breaches.
Defining Salted Hash: A Modern Security Measure
Salted hash is a cryptographic technique that enhances password security by adding a unique random value, called a salt, to the plaintext before hashing, thereby preventing attacks like rainbow table and precomputed hash breaches. Unlike plaintext storage, salted hashes store hashed values combined with salts, ensuring that identical passwords result in distinct hashes, increasing resilience against brute force and dictionary attacks. Modern security frameworks widely implement salted hashing algorithms such as bcrypt, Argon2, and PBKDF2 to protect user credentials in authentication systems.
How Plaintext Exposes Sensitive Data
Plaintext stores sensitive data in an unencrypted, readable format, making it easily accessible to unauthorized users during data breaches or interceptions. Attackers gaining access to plaintext credentials can directly exploit accounts, leading to identity theft, financial loss, or unauthorized system access. Unlike salted hashes, plaintext offers no protection or obfuscation, significantly increasing the risk of data exposure and compromise.
The Process Behind Hashing and Salting
Hashing transforms plaintext into a fixed-length string using cryptographic algorithms, ensuring data integrity and non-reversibility. Salting involves adding a unique random value to the plaintext before hashing, significantly enhancing security by preventing attacks such as rainbow table lookups. The combined process creates a salted hash that protects stored data by making each hash output unique even for identical plaintext inputs.
Security Risks of Storing Data in Plaintext
Storing data in plaintext poses significant security risks including unauthorized access, data breaches, and identity theft due to its unencrypted format. Plaintext passwords can be easily exposed during cyberattacks, leading to compromised user accounts and network vulnerabilities. Salting hashes enhances protection by adding unique, random data before hashing, making it computationally difficult for attackers to reverse-engineer passwords or use precomputed rainbow tables.
Advantages of Using Salted Hashes
Salted hashes enhance security by adding a unique random value, or salt, to each password before hashing, which prevents attackers from using precomputed tables like rainbow tables for cracking. This process ensures that identical passwords result in different hashes, making it significantly harder for cybercriminals to perform mass attacks or identify common passwords. Salting also mitigates risks associated with hash collisions and provides robust defense against brute-force and dictionary attacks.
Real-World Examples: Data Breaches and Their Causes
Data breaches such as the 2013 Adobe incident exposed millions of plaintext passwords, highlighting the severe risks of unencrypted storage. In contrast, the 2012 LinkedIn breach leveraged unsalted SHA-1 hashes, enabling attackers to quickly crack hashed passwords due to lack of salting and weak hashing algorithms. Modern security practices mandate salted hashing with algorithms like bcrypt or Argon2 to mitigate real-world attack vectors and protect user credentials effectively.
Implementing Salted Hash in Authentication Systems
Implementing salted hash in authentication systems significantly enhances security by adding a unique random value, or salt, to each password before hashing, preventing attackers from using precomputed rainbow tables. Each salt is stored alongside the hashed password, ensuring that identical passwords result in distinct hash values, mitigating risks from database breaches. Modern frameworks utilize algorithms like bcrypt or Argon2 that integrate salting and multiple hashing rounds, providing robust protection against brute-force and collision attacks in authentication processes.
Comparing Performance: Plaintext vs Salted Hash
Plaintext storage offers faster retrieval times due to the absence of encryption overhead but drastically compromises security by exposing sensitive data directly. Salted hash processes introduce computational complexity to enhance security, significantly increasing hashing time, especially when using strong algorithms like bcrypt or Argon2. Despite slower performance, salted hashes provide robust defense against rainbow table attacks, making them essential for secure password storage.
Best Practices for Secure Data Storage
Storing passwords as salted hashes significantly enhances security by adding a unique random value to each password before hashing, preventing attackers from using precomputed rainbow tables. Plaintext storage leaves data vulnerable to breaches, exposing sensitive information without any protection. Implementing strong, adaptive hash functions like bcrypt, Argon2, or PBKDF2 alongside proper salting ensures robust defense against brute-force and collision attacks.
Plaintext Infographic
 libterm.com
libterm.com