Symbolic execution systematically analyzes programs by using symbolic inputs instead of concrete values, allowing the exploration of multiple execution paths simultaneously. This technique helps identify vulnerabilities, bugs, and unreachable code by evaluating how different inputs affect program behavior. Discover how symbolic execution can enhance your software testing and debugging processes by reading the full article.
Table of Comparison
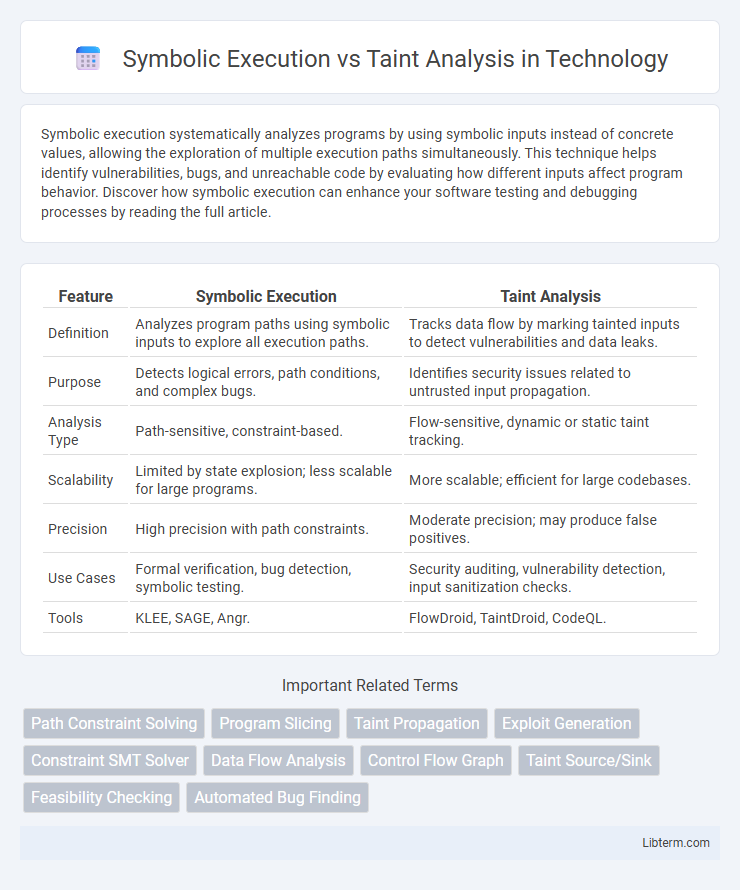
| Feature | Symbolic Execution | Taint Analysis |
|---|---|---|
| Definition | Analyzes program paths using symbolic inputs to explore all execution paths. | Tracks data flow by marking tainted inputs to detect vulnerabilities and data leaks. |
| Purpose | Detects logical errors, path conditions, and complex bugs. | Identifies security issues related to untrusted input propagation. |
| Analysis Type | Path-sensitive, constraint-based. | Flow-sensitive, dynamic or static taint tracking. |
| Scalability | Limited by state explosion; less scalable for large programs. | More scalable; efficient for large codebases. |
| Precision | High precision with path constraints. | Moderate precision; may produce false positives. |
| Use Cases | Formal verification, bug detection, symbolic testing. | Security auditing, vulnerability detection, input sanitization checks. |
| Tools | KLEE, SAGE, Angr. | FlowDroid, TaintDroid, CodeQL. |
Introduction to Symbolic Execution and Taint Analysis
Symbolic Execution maps program variables to symbolic values instead of concrete data, allowing comprehensive path exploration to detect potential vulnerabilities or bugs by analyzing constraints. Taint Analysis tracks the flow of untrusted or sensitive data through a program to identify unsafe operations or security breaches such as injection attacks and data leaks. Both techniques enhance software security testing but differ in approach: Symbolic Execution explores execution paths symbolically, while Taint Analysis monitors data propagation dynamically or statically.
Core Concepts: Symbolic Execution Explained
Symbolic execution involves running programs with symbolic inputs instead of concrete values, allowing exploration of multiple execution paths simultaneously by representing inputs as symbolic variables. This technique generates path constraints that can be solved using SMT solvers to identify bugs, vulnerabilities, or path feasibility. Core to symbolic execution is the symbolic state, which tracks symbolic expressions for program variables and conditions encountered during execution.
Fundamentals of Taint Analysis Methods
Taint analysis tracks the flow of sensitive data through program variables to detect potential security vulnerabilities such as information leaks or injection attacks. It assigns "taint" labels to untrusted inputs and propagates these labels through operations, identifying code regions where tainted data influences control flow or outputs. Unlike symbolic execution, which systematically explores program paths using symbolic inputs, taint analysis offers a dynamic or static approximation focused on data dependencies and taint propagation for efficient vulnerability detection.
Key Differences Between Symbolic Execution and Taint Analysis
Symbolic execution systematically explores program paths by treating inputs as symbolic variables, enabling precise path constraint solving and detecting complex vulnerabilities. Taint analysis tracks data flow from untrusted sources through variables to identify potential security issues related to tainted data usage, emphasizing speed and scalability over path exploration depth. Symbolic execution excels in accuracy and path coverage but suffers from path explosion, while taint analysis provides faster detection with possible false positives due to its conservative taint propagation approach.
Use Cases: When to Use Symbolic Execution
Symbolic execution is ideal for detecting deep logical errors, generating high-coverage test cases, and verifying security properties in complex software systems where input conditions influence control flow. Use cases include vulnerability discovery in cryptographic protocols, path-sensitive bug detection in embedded systems, and automated test generation for safety-critical applications. Its precise path exploration surpasses taint analysis in scenarios demanding execution path completeness and constraint solving.
Use Cases: When to Use Taint Analysis
Taint analysis excels in detecting vulnerabilities related to user input, such as SQL injection, cross-site scripting (XSS), and information leakage by tracking the flow of untrusted data through a program. It is particularly effective in large codebases where identifying how external inputs propagate can uncover security flaws without exhaustive path exploration. Taint analysis is ideal for security auditing in web applications, input validation testing, and discovering privacy violations caused by improper data handling.
Strengths and Limitations of Symbolic Execution
Symbolic execution excels at systematically exploring program paths by using symbolic inputs, enabling precise detection of logical errors and vulnerabilities in complex software. Its strength lies in generating concrete test cases for deep program analysis, but the technique struggles with path explosion and scalability issues in large codebases. Limited handling of external environment interactions and loops further restricts its applicability in real-world scenarios compared to taint analysis.
Strengths and Limitations of Taint Analysis
Taint analysis excels at tracking the flow of untrusted data through a program to identify security vulnerabilities such as SQL injection and cross-site scripting, offering high efficiency and scalability in handling large codebases. Its main limitation lies in the inability to reason about complex program states or path conditions, often resulting in false positives or missed vulnerabilities when program logic is highly intricate. While symbolic execution provides comprehensive path coverage and precise vulnerability detection, taint analysis remains preferred for quick, targeted analysis due to lower computational overhead.
Integration and Hybrid Approaches in Software Security
Symbolic execution and taint analysis are integrated in hybrid approaches to enhance software security by combining the path exploration capability of symbolic execution with the data flow tracking strength of taint analysis. These integrated methods enable more precise vulnerability detection, especially for complex software where pure symbolic execution faces path explosion and taint analysis suffers from false positives. Hybrid frameworks leverage symbolic constraints derived from taint propagation to systematically explore feasible execution paths, improving accuracy in detecting security issues such as injection flaws and buffer overflows.
Future Trends in Program Analysis Techniques
Future trends in program analysis techniques emphasize integrating symbolic execution with taint analysis to enhance vulnerability detection accuracy. Advances in machine learning-driven heuristics aim to optimize path exploration in symbolic execution, reducing state explosion issues while improving taint propagation precision. Emerging hybrid frameworks leveraging formal methods and dynamic taint tracking promise scalable, real-time security analysis tailored for complex software systems.
Symbolic Execution Infographic
 libterm.com
libterm.com