Pentesting reveals vulnerabilities in your system by simulating real-world cyberattacks to assess security weaknesses before attackers exploit them. Security audits provide a comprehensive evaluation of your organization's policies, controls, and compliance with industry standards to strengthen your defense mechanisms. Discover how these critical techniques can protect your digital assets by reading the full article.
Table of Comparison
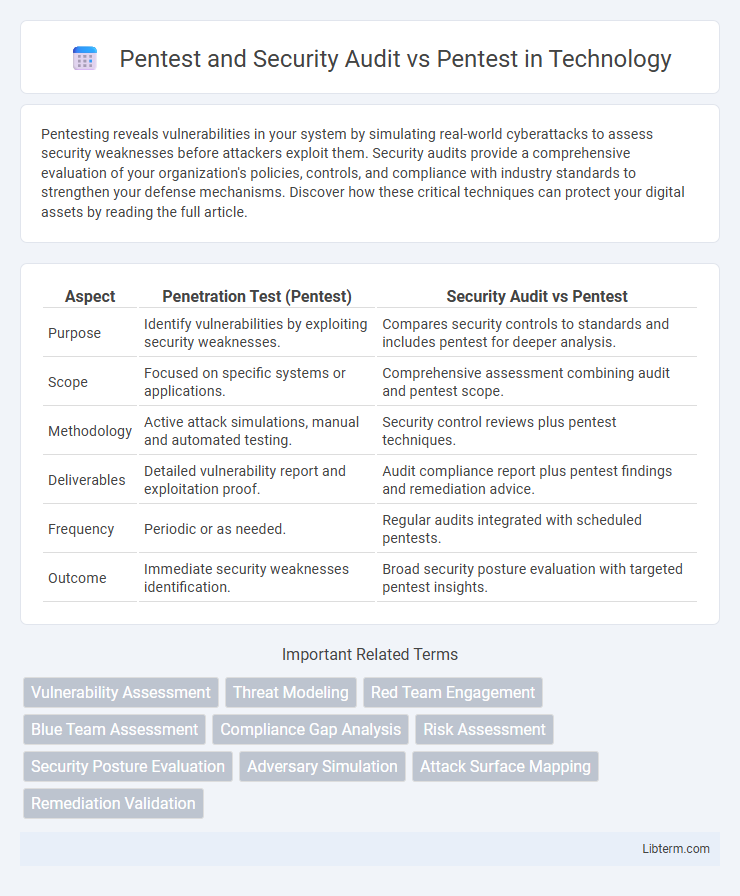
| Aspect | Penetration Test (Pentest) | Security Audit vs Pentest |
|---|---|---|
| Purpose | Identify vulnerabilities by exploiting security weaknesses. | Compares security controls to standards and includes pentest for deeper analysis. |
| Scope | Focused on specific systems or applications. | Comprehensive assessment combining audit and pentest scope. |
| Methodology | Active attack simulations, manual and automated testing. | Security control reviews plus pentest techniques. |
| Deliverables | Detailed vulnerability report and exploitation proof. | Audit compliance report plus pentest findings and remediation advice. |
| Frequency | Periodic or as needed. | Regular audits integrated with scheduled pentests. |
| Outcome | Immediate security weaknesses identification. | Broad security posture evaluation with targeted pentest insights. |
Understanding Pentest and Security Audit: Key Differences
Penetration testing (Pentest) identifies vulnerabilities by simulating cyberattacks, while a security audit evaluates an organization's overall security policies, procedures, and compliance with standards. Pentests focus on technical weaknesses in systems and networks, providing actionable insights to improve defenses, whereas security audits assess governance, risk management, and regulatory adherence. Understanding these key differences helps organizations implement comprehensive security strategies combining both in-depth technical testing and thorough policy evaluation.
What is a Security Audit?
A Security Audit is a comprehensive evaluation of an organization's security policies, procedures, and controls to ensure compliance with regulatory standards and industry best practices. Unlike a Pentest, which focuses on identifying vulnerabilities through simulated attacks, a Security Audit assesses the overall effectiveness and implementation of security measures across the entire IT infrastructure. This process includes reviewing documentation, configuration settings, and operational processes to identify gaps and recommend improvements for maintaining robust security posture.
What is a Pentest (Penetration Test)?
A Pentest (Penetration Test) is a simulated cyberattack against a computer system, network, or application to identify vulnerabilities that malicious hackers could exploit. It involves actively probing for security weaknesses using tools and techniques that mimic real-world attack scenarios. Unlike a broader security audit that reviews policies and compliance, a Pentest focuses specifically on exploiting vulnerabilities to assess the practical effectiveness of security controls.
Scope Comparison: Security Audit vs. Pentest
Security audit encompasses a comprehensive evaluation of an organization's policies, procedures, and controls to ensure compliance and identify security gaps, covering both technical and administrative aspects. Penetration testing (pentest) zeroes in on identifying vulnerabilities by simulating cyberattacks on specific systems or networks to evaluate exploitable weaknesses. The scope of a security audit is broader, addressing overall risk management frameworks, while pentest provides a focused, practical assessment of real-world attack vectors within defined target environments.
Methodologies: How Audits and Pentests Differ
Security audits emphasize comprehensive evaluation based on established frameworks like ISO 27001 or NIST, focusing on policy compliance, risk management, and procedural effectiveness. Penetration tests employ offensive methodologies such as vulnerability scanning, exploitation, and real-world attack simulations to identify exploitable security flaws. Audits provide a broad security posture overview while pentests deliver in-depth technical insights by actively probing system defenses.
Objectives: Security Audit and Pentest Goals
Security audits focus on comprehensive evaluations of an organization's security policies, procedures, and controls to ensure compliance with standards and identify vulnerabilities at a systemic level. Penetration testing (pentest) aims to simulate real-world cyberattacks to identify exploitable weaknesses in specific systems, networks, or applications by actively attempting to breach defenses. The primary objective of security audits is risk management and policy enforcement, while pentest goals center on uncovering actionable security flaws to enhance defensive measures.
Depth and Breadth of Testing: Audit vs. Pentest
Security audits offer a broader assessment by systematically reviewing policies, procedures, and controls to ensure compliance and identify potential gaps across an entire organization. Penetration tests provide deeper, targeted evaluation by simulating real-world cyberattacks to exploit specific vulnerabilities and assess the effectiveness of defenses in practical scenarios. Combining audits with pentests creates a comprehensive security strategy, balancing extensive coverage with in-depth analysis of critical risks.
Reporting: Pentest Findings vs. Audit Reports
Pentest findings provide detailed, vulnerability-specific insights focused on exploit techniques and remediation steps, targeting technical teams for quick mitigation. Audit reports offer a comprehensive evaluation of security policies, compliance status, and risk management, tailored for management and regulatory review. Both emphasize clear, actionable reporting but differ in scope, with Pentest reports emphasizing technical details and Audit reports providing strategic security posture analysis.
When to Choose a Security Audit, Pentest, or Both
Security audits are ideal for organizations seeking comprehensive assessments of policies, procedures, and compliance to industry standards, while penetration testing targets identifying vulnerabilities by simulating real-world cyberattacks on specific systems or applications. Choose a security audit when the goal is to evaluate overall security posture and regulatory adherence, whereas penetration testing is preferable for testing system defenses against active threats. Combining both provides a thorough approach, ensuring not only compliance and process evaluation but also identifying exploitable weaknesses through practical attack simulations.
Integrating Pentests and Security Audits for Holistic Security
Integrating penetration testing and security audits creates a comprehensive security posture by combining vulnerability identification with policy and compliance evaluation. Penetration tests simulate real-world cyberattacks to uncover exploitable weaknesses, while security audits assess the effectiveness of security controls, configurations, and adherence to regulatory standards. This holistic approach ensures not only technical vulnerabilities are addressed but also organizational security governance, leading to robust risk management and improved defense strategies.
Pentest and Security Audit Infographic
 libterm.com
libterm.com