A Man-in-the-Middle (MitM) attack occurs when a cybercriminal intercepts communication between two parties to steal or manipulate data without their knowledge. This type of attack exploits vulnerabilities in network security, making it crucial for individuals and organizations to implement strong encryption and authentication measures. Discover effective strategies to protect Your digital information from MitM attacks in the rest of this article.
Table of Comparison
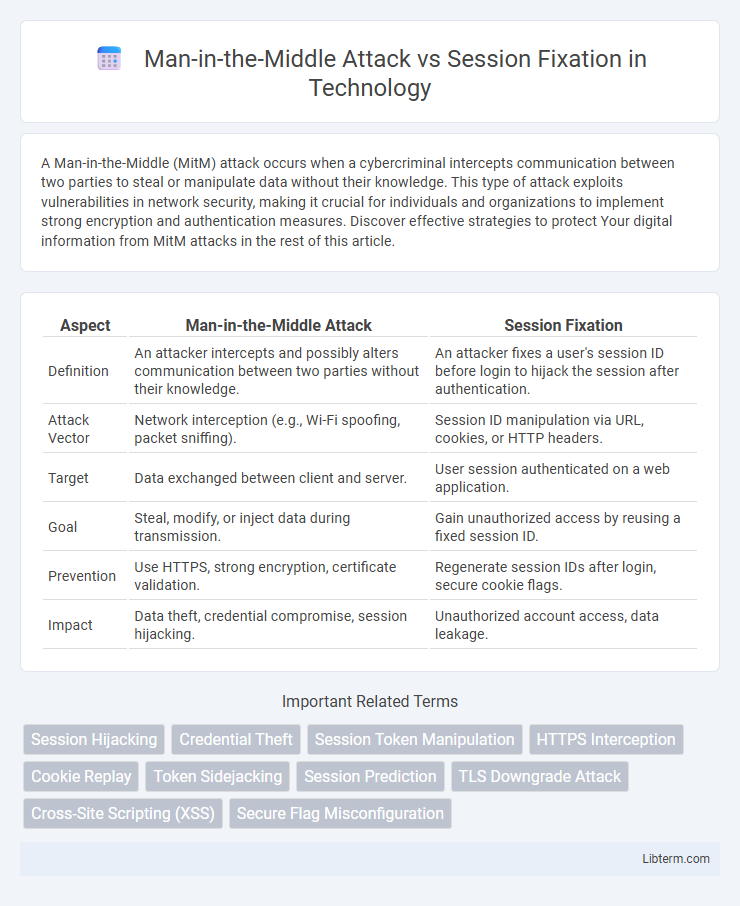
| Aspect | Man-in-the-Middle Attack | Session Fixation |
|---|---|---|
| Definition | An attacker intercepts and possibly alters communication between two parties without their knowledge. | An attacker fixes a user's session ID before login to hijack the session after authentication. |
| Attack Vector | Network interception (e.g., Wi-Fi spoofing, packet sniffing). | Session ID manipulation via URL, cookies, or HTTP headers. |
| Target | Data exchanged between client and server. | User session authenticated on a web application. |
| Goal | Steal, modify, or inject data during transmission. | Gain unauthorized access by reusing a fixed session ID. |
| Prevention | Use HTTPS, strong encryption, certificate validation. | Regenerate session IDs after login, secure cookie flags. |
| Impact | Data theft, credential compromise, session hijacking. | Unauthorized account access, data leakage. |
Understanding Man-in-the-Middle (MitM) Attacks
Man-in-the-Middle (MitM) attacks involve an attacker secretly intercepting and potentially altering communication between two parties, allowing unauthorized access to sensitive data such as login credentials or financial information. Unlike session fixation, which exploits session IDs to hijack user sessions, MitM attacks actively manipulate data in transit by impersonating one or both communication endpoints. Effective MitM prevention techniques include robust encryption protocols like TLS, strong mutual authentication, and vigilant network monitoring to detect suspicious activity.
What is Session Fixation?
Session Fixation is a cyberattack technique where an attacker sets or fixes a user's session ID before the user logs into a web application, enabling the attacker to hijack the authenticated session. Unlike Man-in-the-Middle attacks that intercept communication between two parties, Session Fixation exploits the session management mechanism by forcing a known session ID on the victim. Preventing Session Fixation involves secure session ID regeneration upon login and ensuring session IDs are not accepted from untrusted sources.
How Man-in-the-Middle Attacks Work
Man-in-the-Middle (MitM) attacks occur when an attacker secretly intercepts and potentially alters communication between two parties without their knowledge, often targeting unencrypted data or weak encryption protocols. Attackers position themselves between the user and the intended service to capture sensitive information such as login credentials, session tokens, or confidential messages before forwarding them to the legitimate recipient. Unlike session fixation, which exploits session ID vulnerabilities, MitM attacks actively intercept and manipulate data in transit, making encryption methods like TLS crucial for defense.
The Mechanisms Behind Session Fixation
Session fixation exploits the web application's session management by forcing a user's session ID before authentication, allowing an attacker to take over the session post-login. This attack mechanism often involves tricking victims into using a predefined session ID through URL parameters, cookies, or hidden fields. Unlike man-in-the-middle attacks that intercept communications, session fixation relies on manipulating session ID assignment to maintain persistent unauthorized access.
Key Differences Between MitM and Session Fixation
Man-in-the-Middle (MitM) attacks intercept and alter communications between two parties without their knowledge, compromising data integrity and confidentiality. Session Fixation exploits a known session ID to hijack a user's authenticated session, allowing attackers to assume the user's identity. The key difference lies in MitM targeting communication channels for eavesdropping and manipulation, while Session Fixation specifically targets session management to gain unauthorized access.
Common Attack Vectors and Techniques
Man-in-the-Middle (MITM) attacks commonly exploit unsecured Wi-Fi networks and DNS spoofing to intercept and manipulate communications between users and servers, compromising sensitive data in transit. Session Fixation attacks target vulnerabilities in session management by forcing victims to use a predetermined session ID, often through URL parameters or cookie injection, allowing attackers to hijack authenticated sessions. Both attack types leverage weaknesses in session token handling and network security protocols to breach user trust and access restricted resources.
Real-World Examples of Both Attacks
Man-in-the-Middle (MITM) attacks famously disrupted the 2011 DigiNotar breach, where attackers intercepted communications to issue fraudulent SSL certificates, compromising secure web traffic. Session Fixation was notably exploited in a 2007 vulnerability in PHP applications, allowing attackers to hijack authenticated sessions by forcing users to adopt a known session ID. These real-world incidents highlight the critical need for robust encryption and secure session management to prevent unauthorized access and data interception.
Security Implications: Risk Assessment
Man-in-the-Middle (MITM) attacks intercept and manipulate communications between two parties, posing risks of data theft, credential exposure, and session hijacking, leading to severe confidentiality and integrity breaches. Session fixation attacks exploit weaknesses in session management by forcing a user to utilize a known session ID, increasing the risk of unauthorized access and identity impersonation. Both attack vectors demand robust encryption protocols, secure session handling, and vigilant monitoring to mitigate significant security risks in web applications and network environments.
Prevention and Mitigation Strategies
Man-in-the-Middle (MitM) attack prevention relies heavily on strong encryption protocols like TLS/SSL to secure communication channels and the use of multi-factor authentication (MFA) to reduce unauthorized access risks. Session Fixation mitigation involves regenerating session IDs upon user authentication and enforcing secure, HttpOnly cookie attributes to prevent attackers from hijacking valid sessions. Regular security audits, timely software updates, and implementing intrusion detection systems further strengthen defenses against both MitM and session fixation threats.
Conclusion: Safeguarding Against Session Hijacking Attacks
Man-in-the-Middle (MitM) attacks intercept and manipulate communication, while Session Fixation exploits pre-established session IDs to gain unauthorized access. Implementing secure protocols like HTTPS, enforcing strict cookie attributes (HttpOnly, Secure), and regenerating session IDs after authentication significantly reduce the risk of session hijacking. Continuous monitoring and employing multi-factor authentication provide robust defense mechanisms against both MitM and Session Fixation threats.
Man-in-the-Middle Attack Infographic
 libterm.com
libterm.com