An access control list (ACL) is a critical security feature used to define permissions for users or systems to access resources such as files, networks, or applications. By specifying who is allowed or denied access, ACLs help protect sensitive data and maintain organizational security. Discover how implementing effective ACLs can enhance Your system's security in the detailed article ahead.
Table of Comparison
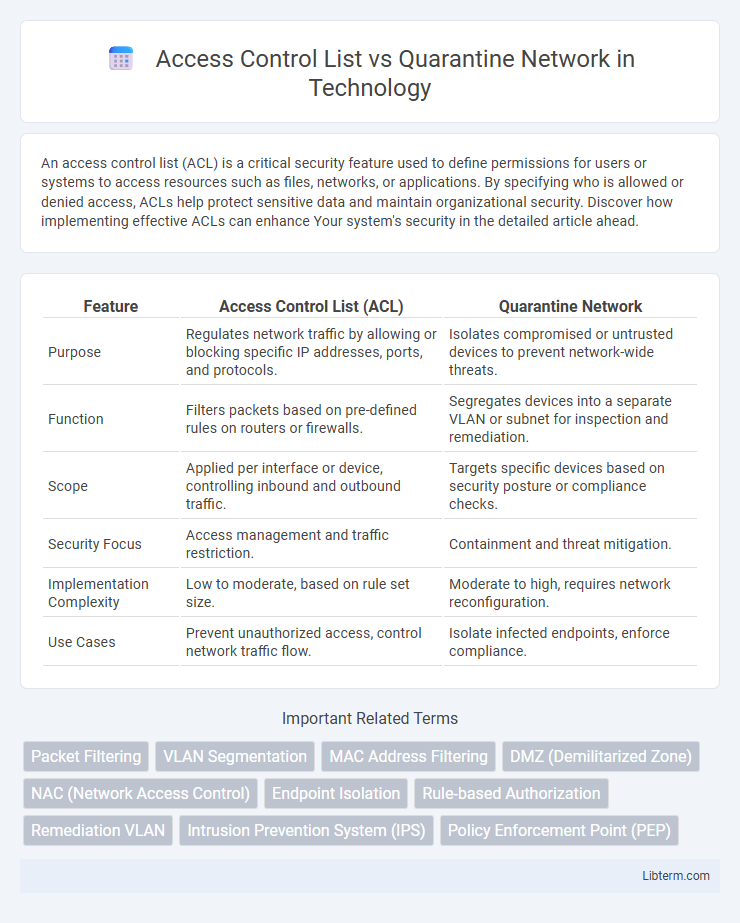
| Feature | Access Control List (ACL) | Quarantine Network |
|---|---|---|
| Purpose | Regulates network traffic by allowing or blocking specific IP addresses, ports, and protocols. | Isolates compromised or untrusted devices to prevent network-wide threats. |
| Function | Filters packets based on pre-defined rules on routers or firewalls. | Segregates devices into a separate VLAN or subnet for inspection and remediation. |
| Scope | Applied per interface or device, controlling inbound and outbound traffic. | Targets specific devices based on security posture or compliance checks. |
| Security Focus | Access management and traffic restriction. | Containment and threat mitigation. |
| Implementation Complexity | Low to moderate, based on rule set size. | Moderate to high, requires network reconfiguration. |
| Use Cases | Prevent unauthorized access, control network traffic flow. | Isolate infected endpoints, enforce compliance. |
Introduction to Access Control List (ACL) and Quarantine Network
Access Control List (ACL) is a security feature used to filter network traffic and regulate access to resources by defining rules based on IP addresses, protocols, or ports, enhancing network security and performance. Quarantine Network isolates infected or suspicious devices to prevent the spread of malware and unauthorized access, ensuring network integrity. Both ACL and Quarantine Network play crucial roles in safeguarding enterprise networks by controlling device access and mitigating security risks.
Core Concepts: What is an Access Control List?
An Access Control List (ACL) is a security feature implemented in network devices that defines rules to permit or deny traffic based on IP addresses, protocols, or ports. ACLs enforce granular access policies by filtering packets at various layers, effectively controlling network resource accessibility. This mechanism contrasts with quarantine networks, which isolate suspicious devices to prevent potential threats from spreading across the network.
Core Concepts: What is a Quarantine Network?
A Quarantine Network isolates devices suspected of being compromised or non-compliant by restricting their access to critical resources, thereby minimizing security risks. Access Control Lists (ACLs) define explicit permissions for users and devices to access network resources based on IP addresses, protocols, or ports. While ACLs enforce granular access policies, Quarantine Networks provide a controlled environment to remediate or monitor devices before granting broader network access.
Key Differences: ACL vs Quarantine Network
Access Control Lists (ACLs) regulate network traffic by defining rules that permit or deny packets based on IP addresses, protocols, or ports, providing granular access control at the device or interface level. Quarantine networks isolate suspicious or non-compliant devices into a separate VLAN or subnet to restrict their access to critical resources until remediation occurs. While ACLs focus on traffic filtering and permissions, quarantine networks emphasize containment and remediation by segmenting potentially harmful devices from the main network.
Use Cases for Access Control Lists
Access Control Lists (ACLs) are primarily used to regulate network traffic by defining rules that permit or deny access based on IP addresses, protocols, or ports, making them ideal for segmenting networks and enhancing security. ACLs are effective in use cases such as restricting unauthorized access to sensitive resources, controlling inbound and outbound traffic on routers and firewalls, and implementing role-based access policies within enterprise networks. In contrast, network quarantine isolates compromised devices to prevent threat spread, focusing on containment rather than granular traffic filtering.
Use Cases for Quarantine Networks
Quarantine networks are primarily used to isolate devices that exhibit suspicious behavior or fail security compliance checks, preventing them from accessing sensitive resources while allowing limited network connection for remediation. Unlike Access Control Lists (ACLs), which filter traffic based on predefined rules to enforce general access permissions, quarantine networks provide dynamic containment and controlled access to remediation services such as patch servers or antivirus updates. Use cases include containing infected or non-compliant endpoints during malware outbreaks, ensuring secure onboarding of bring-your-own-device (BYOD) hardware, and segmenting guest users to mitigate security risks without disrupting overall network operations.
Security Benefits of ACLs
Access Control Lists (ACLs) provide granular control over network traffic by specifying which users or devices can access specific resources, significantly reducing unauthorized access and potential attack surfaces. ACLs enable precise filtering of inbound and outbound packets based on IP addresses, protocols, and ports, enhancing protection against network threats. This targeted access management improves overall network security by enforcing strict traffic policies, which contrasts with quarantine networks that isolate potentially compromised devices but do not offer detailed traffic control.
Security Benefits of Quarantine Networks
Quarantine networks enhance security by isolating suspicious or non-compliant devices from the main network, preventing potential threats from spreading. Unlike Access Control Lists (ACLs) that primarily filter traffic based on predefined rules, quarantine networks dynamically contain compromised endpoints and enforce remediation before granting access. This proactive containment minimizes the risk of malware propagation, data breaches, and unauthorized access within enterprise environments.
Limitations and Challenges of ACLs and Quarantine Networks
Access Control Lists (ACLs) face limitations such as static rule enforcement, making dynamic threats difficult to mitigate, and often require extensive manual configuration, which increases the chances of human error. Quarantine networks, while effective in isolating suspicious devices, challenge scalability and can disrupt legitimate network traffic, leading to potential productivity loss. Both ACLs and quarantine networks struggle with adapting to evolving threats, necessitating continuous updates and sophisticated integration with other security frameworks.
Choosing the Right Solution: ACL or Quarantine Network?
Choosing between Access Control Lists (ACLs) and Quarantine Networks depends on the specific security needs and network architecture. ACLs provide granular control by defining explicit rules for traffic filtering based on IP addresses, protocols, and ports, making them ideal for preventing unauthorized access. Quarantine Networks isolate suspicious or non-compliant devices, limiting their access to critical resources while allowing remediation, which is essential for managing devices with potential security risks.
Access Control List Infographic
 libterm.com
libterm.com