White Team represents a crucial group dedicated to testing and improving cybersecurity defenses by simulating real-world attack scenarios and analyzing vulnerabilities within an organization's systems. Their efforts ensure proactive identification of security gaps, safeguarding your digital environment against emerging threats. Discover how the White Team's strategies can strengthen your cybersecurity posture by reading the rest of the article.
Table of Comparison
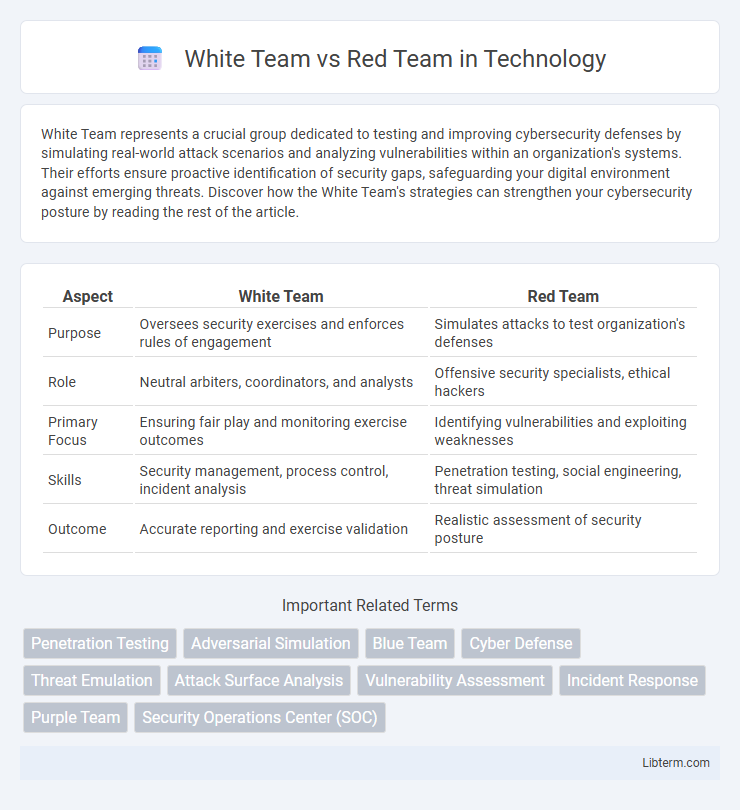
| Aspect | White Team | Red Team |
|---|---|---|
| Purpose | Oversees security exercises and enforces rules of engagement | Simulates attacks to test organization's defenses |
| Role | Neutral arbiters, coordinators, and analysts | Offensive security specialists, ethical hackers |
| Primary Focus | Ensuring fair play and monitoring exercise outcomes | Identifying vulnerabilities and exploiting weaknesses |
| Skills | Security management, process control, incident analysis | Penetration testing, social engineering, threat simulation |
| Outcome | Accurate reporting and exercise validation | Realistic assessment of security posture |
Introduction to White Team and Red Team
White Team and Red Team represent opposing roles in cybersecurity exercises, with the White Team acting as neutral arbiters responsible for organizing, monitoring, and evaluating the simulation. The White Team ensures adherence to rules and maintains overall event integrity, providing real-time oversight and decision-making support. In contrast, the Red Team simulates adversarial attacks, employing offensive tactics to identify vulnerabilities and test the defenses of an organization's security infrastructure.
Defining White Team: Roles and Responsibilities
White Team members serve as referees and coordinators in cybersecurity exercises, ensuring fair play and accurate assessment by monitoring Red Team (attackers) and Blue Team (defenders) activities. Their roles include managing the scenario timeline, enforcing rules of engagement, and facilitating communication among teams while maintaining the integrity of the simulation. White Team responsibilities also extend to evaluating performance metrics and documenting outcomes to enhance future security strategies and training programs.
Understanding the Red Team: Key Functions
The Red Team simulates real-world cyberattacks to identify vulnerabilities in an organization's security posture. Their key functions include penetration testing, social engineering, and exploiting system weaknesses to assess potential risks. This proactive approach helps organizations strengthen defenses and improve overall cybersecurity resilience.
Objectives: White Team vs Red Team
The White Team focuses on managing and overseeing cybersecurity exercises by defining rules, monitoring actions, and evaluating performance to ensure realistic and effective testing environments. The Red Team simulates adversarial attacks by exploiting vulnerabilities and testing defenses to identify security weaknesses and improve organizational resilience. Their combined efforts enhance threat detection, response strategies, and overall security posture.
Skills and Tools Used by Each Team
The White Team utilizes comprehensive risk assessment tools, incident response frameworks, and forensic analysis software to simulate defensive strategies and manage security protocols. The Red Team employs advanced penetration testing tools such as Metasploit, Nmap, and Burp Suite to exploit vulnerabilities and mimic real-world cyberattack techniques. Both teams leverage threat intelligence platforms and collaboration software to enhance situational awareness and improve overall organizational cybersecurity resilience.
Collaboration and Coordination Between Teams
Effective collaboration and coordination between White Team and Red Team enhances cybersecurity resilience by ensuring comprehensive threat detection and response. White Team oversees the simulation environment and evaluates Red Team's attack strategies, fostering real-time communication to quickly identify vulnerabilities. Regular joint debriefings and shared intelligence facilitate continuous improvement of defense mechanisms and incident response protocols.
Key Differences: White Team vs Red Team
The White Team oversees the coordination, monitoring, and assessment of cybersecurity exercises, ensuring rules compliance and analyzing results to improve defense strategies. The Red Team simulates real-world attacks by identifying vulnerabilities and exploiting system weaknesses to test organizational security posture. Key differences lie in their roles: the White Team acts as impartial referees and evaluators, while the Red Team functions as attackers aiming to expose security gaps.
Scenarios and Use Cases in Cybersecurity
White Team and Red Team exercises simulate real-world cybersecurity threats to enhance organizational defense mechanisms. Red Team executes simulated attacks mimicking adversaries to identify vulnerabilities, while White Team oversees the operation, ensures rules of engagement, and provides objective evaluation. Use cases include breach simulation, incident response training, and assessing security posture in critical infrastructure, financial services, and government sectors.
Benefits of Implementing Both Teams
Implementing both White Team and Red Team enhances organizational cybersecurity by combining offensive and defensive strategies, offering comprehensive threat detection and response. White Teams oversee simulations and ensure adherence to rules, promoting structured engagement and continuous improvement, while Red Teams identify vulnerabilities through realistic attack scenarios. This dual approach improves resilience by fostering collaboration, refining defense mechanisms, and accelerating incident response capabilities against evolving cyber threats.
Conclusion: Choosing the Right Approach
Selecting the appropriate cybersecurity strategy between White Team and Red Team depends on organizational goals and risk tolerance. White Teams provide structured oversight and ensure compliance during security exercises, while Red Teams simulate real-world attacks to identify vulnerabilities. A balanced integration of both teams enhances comprehensive threat detection and response capabilities.
White Team Infographic
 libterm.com
libterm.com