Classical key distribution relies on traditional cryptographic methods to securely exchange encryption keys over potentially insecure channels. This process often involves symmetric or asymmetric algorithms to ensure confidentiality and authentication without relying on quantum technologies. Explore the full article to understand how classical key distribution methods safeguard your communication in various network environments.
Table of Comparison
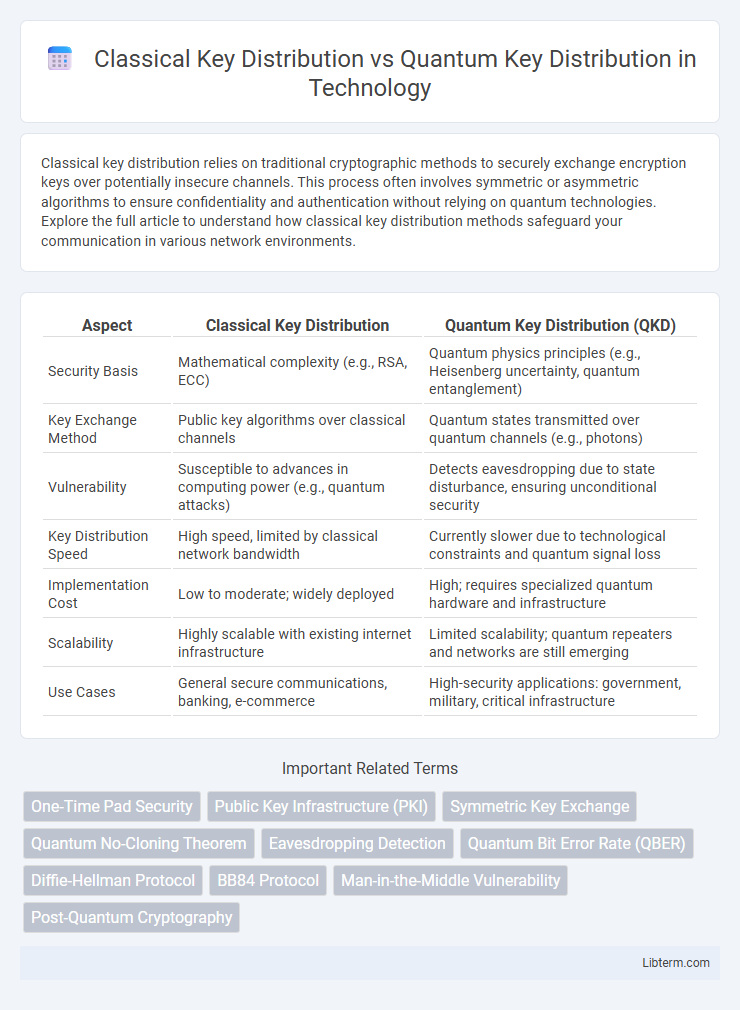
| Aspect | Classical Key Distribution | Quantum Key Distribution (QKD) |
|---|---|---|
| Security Basis | Mathematical complexity (e.g., RSA, ECC) | Quantum physics principles (e.g., Heisenberg uncertainty, quantum entanglement) |
| Key Exchange Method | Public key algorithms over classical channels | Quantum states transmitted over quantum channels (e.g., photons) |
| Vulnerability | Susceptible to advances in computing power (e.g., quantum attacks) | Detects eavesdropping due to state disturbance, ensuring unconditional security |
| Key Distribution Speed | High speed, limited by classical network bandwidth | Currently slower due to technological constraints and quantum signal loss |
| Implementation Cost | Low to moderate; widely deployed | High; requires specialized quantum hardware and infrastructure |
| Scalability | Highly scalable with existing internet infrastructure | Limited scalability; quantum repeaters and networks are still emerging |
| Use Cases | General secure communications, banking, e-commerce | High-security applications: government, military, critical infrastructure |
Introduction to Key Distribution Methods
Classical Key Distribution methods rely on mathematical algorithms such as RSA and Diffie-Hellman to securely exchange cryptographic keys over public channels, but are vulnerable to advances in computational power and algorithmic attacks. Quantum Key Distribution (QKD) utilizes principles of quantum mechanics, like photon polarization and quantum entanglement, to enable theoretically unbreakable encryption by detecting any eavesdropping attempts during key exchange. The fundamental difference lies in QKD's ability to guarantee security based on physical laws rather than computational complexity, making it a promising solution for future-proof secure communication.
Overview of Classical Key Distribution
Classical key distribution relies on mathematical algorithms such as RSA and Diffie-Hellman to securely exchange cryptographic keys over public channels, depending on computational hardness assumptions like factoring large primes. Its security can be compromised by advances in computing power or algorithmic breakthroughs, posing risks for long-term confidentiality. Despite widespread use in current communications infrastructure, classical methods lack the inherent physical security properties offered by quantum key distribution (QKD).
Fundamentals of Quantum Key Distribution
Classical key distribution relies on mathematical algorithms and computational complexity to secure cryptographic keys, making it vulnerable to attacks from powerful quantum computers. Quantum Key Distribution (QKD) leverages principles of quantum mechanics, such as quantum superposition and entanglement, to enable secure key exchange that detects eavesdropping through quantum state disturbance. The fundamental security of QKD stems from the no-cloning theorem and measurement-induced collapse, ensuring any interception attempt alters the quantum states and alerts legitimate parties.
Security Mechanisms in Classical vs Quantum Approaches
Classical Key Distribution relies on cryptographic algorithms like RSA and Diffie-Hellman, which depend on computational hardness assumptions for security but remain vulnerable to advances in computing power and algorithmic attacks. Quantum Key Distribution (QKD) leverages principles of quantum mechanics, such as superposition and entanglement, to detect eavesdropping and guarantee unconditional security through quantum no-cloning and measurement disturbance phenomena. While classical methods face risks from quantum computers, QKD offers provable security by enabling key exchange immune to computational attack, fundamentally transforming secure communication protocols.
Vulnerabilities and Attack Vectors
Classical key distribution relies on computational hardness assumptions, making it vulnerable to attacks such as man-in-the-middle, eavesdropping, and advances in quantum computing that can break traditional encryption algorithms like RSA and ECC. Quantum Key Distribution (QKD) leverages the principles of quantum mechanics, providing theoretically unbreakable security by detecting any eavesdropping attempts through quantum state disturbances. However, QKD is still susceptible to practical attack vectors including side-channel attacks, photon number splitting, and device imperfections that can be exploited to compromise key security.
Performance and Scalability Factors
Classical Key Distribution relies on computational algorithms like RSA and Diffie-Hellman, offering high-speed performance but limited by mathematical security assumptions vulnerable to quantum attacks. Quantum Key Distribution (QKD) uses quantum mechanics principles, providing theoretically unbreakable security with lower key generation rates and significant infrastructure demands, affecting scalability. QKD systems require specialized hardware such as single-photon detectors and quantum repeaters, limiting widespread deployment compared to classical methods that easily scale over existing network infrastructures.
Technological Requirements and Practicality
Classical Key Distribution relies on mathematical algorithms and computational security, requiring standard digital infrastructure such as computers and network devices, making it widely deployable and cost-effective. Quantum Key Distribution (QKD) uses principles of quantum mechanics, including photon transmission and quantum entanglement, demanding specialized hardware like single-photon sources, detectors, and quantum channels, which currently limits scalability and increases deployment complexity. Practical implementation of QKD is challenged by technological limitations such as distance constraints and sensitivity to environmental noise, whereas classical methods are more flexible and easier to integrate into existing communication networks.
Real-World Applications and Use Cases
Classical Key Distribution methods, such as Diffie-Hellman and RSA, remain prevalent in securing internet communications, banking transactions, and virtual private networks, but they are vulnerable to advances in computational power and quantum attacks. Quantum Key Distribution (QKD), leveraging principles of quantum mechanics like photon polarization, enables theoretically unbreakable encryption, making it ideal for high-security environments such as government communications, critical infrastructure protection, and financial institutions requiring long-term data confidentiality. Real-world QKD implementations exist in metropolitan fiber networks and satellite-based systems, demonstrating practical integration potential despite current scalability and cost challenges.
Future Trends in Key Distribution
Future trends in key distribution emphasize enhancing security and efficiency through quantum key distribution (QKD), which leverages the principles of quantum mechanics to provide theoretically unbreakable encryption keys. Classical key distribution methods rely on computational complexity, making them vulnerable to advances in computing power, including the eventual threat posed by quantum computers. Integration of QKD with existing communication networks and development of quantum repeaters are pivotal in enabling long-distance secure key exchange, signaling a shift towards quantum-resistant cryptographic infrastructures.
Summary and Comparative Analysis
Classical Key Distribution relies on mathematical algorithms like RSA and Diffie-Hellman, whose security depends on computational hardness assumptions vulnerable to advances in computing power, including quantum attacks. Quantum Key Distribution (QKD) uses quantum mechanics principles, such as quantum entanglement and no-cloning theorem, to enable unconditional security by detecting eavesdropping through changes in quantum states. Compared to classical methods, QKD offers provably secure key exchange but currently faces challenges like limited distance, high implementation cost, and integration complexity.
Classical Key Distribution Infographic
 libterm.com
libterm.com