UEFI Secure Boot ensures that only trusted software is allowed to run during the startup process, protecting your system from malware and unauthorized code execution. It enhances security by verifying digital signatures of firmware and operating system loaders before they are executed. Discover how UEFI Secure Boot can safeguard your device by reading the full article.
Table of Comparison
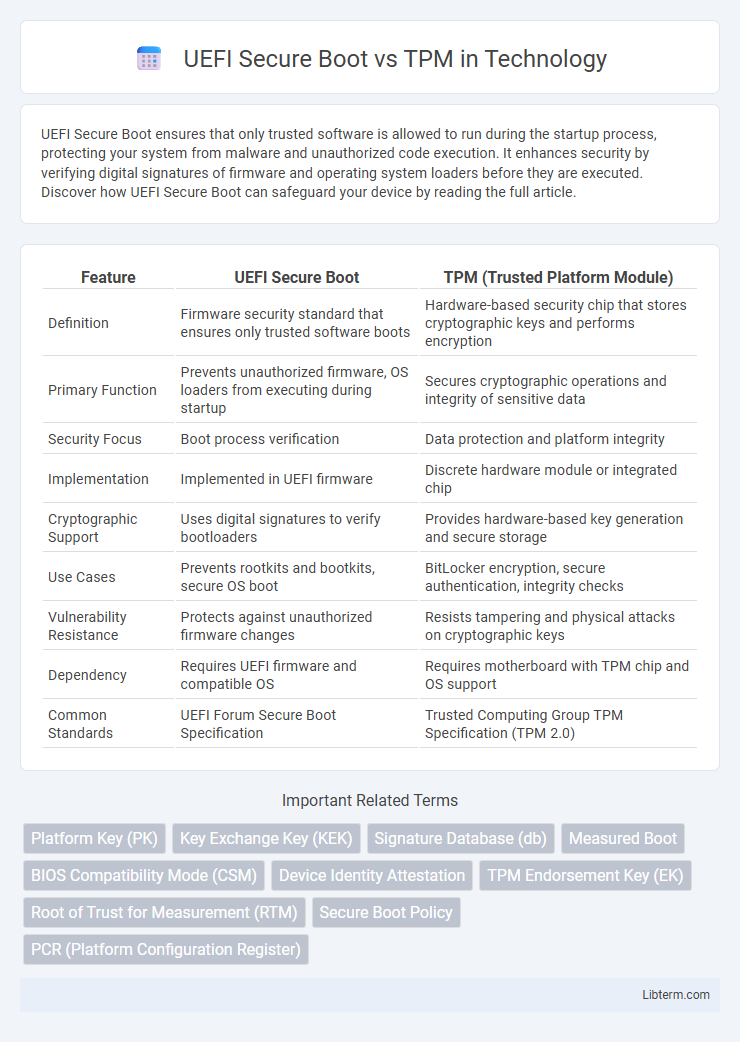
| Feature | UEFI Secure Boot | TPM (Trusted Platform Module) |
|---|---|---|
| Definition | Firmware security standard that ensures only trusted software boots | Hardware-based security chip that stores cryptographic keys and performs encryption |
| Primary Function | Prevents unauthorized firmware, OS loaders from executing during startup | Secures cryptographic operations and integrity of sensitive data |
| Security Focus | Boot process verification | Data protection and platform integrity |
| Implementation | Implemented in UEFI firmware | Discrete hardware module or integrated chip |
| Cryptographic Support | Uses digital signatures to verify bootloaders | Provides hardware-based key generation and secure storage |
| Use Cases | Prevents rootkits and bootkits, secure OS boot | BitLocker encryption, secure authentication, integrity checks |
| Vulnerability Resistance | Protects against unauthorized firmware changes | Resists tampering and physical attacks on cryptographic keys |
| Dependency | Requires UEFI firmware and compatible OS | Requires motherboard with TPM chip and OS support |
| Common Standards | UEFI Forum Secure Boot Specification | Trusted Computing Group TPM Specification (TPM 2.0) |
Introduction to UEFI Secure Boot and TPM
UEFI Secure Boot is a security standard designed to ensure that a device boots using only software trusted by the Original Equipment Manufacturer (OEM), preventing malicious code from executing during the startup process. Trusted Platform Module (TPM) is a dedicated hardware chip that securely stores cryptographic keys and enables functionalities such as hardware-based authentication and platform integrity verification. Together, UEFI Secure Boot and TPM provide robust system protection by verifying firmware authenticity and safeguarding critical security credentials against unauthorized access.
What is UEFI Secure Boot?
UEFI Secure Boot is a security standard embedded in the Unified Extensible Firmware Interface (UEFI) firmware designed to ensure that only trusted software with verified digital signatures can boot on a device, preventing unauthorized or malicious code from executing during the startup process. It plays a crucial role in protecting the boot integrity by validating the operating system's loader against a database of approved signatures stored in the firmware. Unlike TPM (Trusted Platform Module), which provides hardware-based cryptographic functions and secure key storage, UEFI Secure Boot focuses specifically on verifying the authenticity and integrity of the bootloader to maintain a secure boot chain.
What is TPM (Trusted Platform Module)?
TPM (Trusted Platform Module) is a specialized hardware chip designed to enhance computer security by securely storing cryptographic keys, passwords, and certificates. It provides hardware-based encryption and ensures platform integrity by verifying that the system is running trusted software during the boot process. Unlike UEFI Secure Boot, which validates the digital signature of the firmware and bootloader, TPM offers a broader range of security functions including device authentication and secure generation of cryptographic keys.
Core Functions of UEFI Secure Boot
UEFI Secure Boot ensures system integrity by allowing only signed, trusted software to load during the boot process, preventing unauthorized firmware, bootloaders, or OS loaders from executing. It relies on a digital signature database to verify boot components, enforcing a secure chain of trust from firmware to operating system. Unlike TPM, which securely stores cryptographic keys and enables hardware-based security functions, UEFI Secure Boot primarily focuses on validating and authenticating software integrity at startup.
Core Functions of TPM
TPM (Trusted Platform Module) provides hardware-based cryptographic functions that securely store cryptographic keys, perform platform integrity measurements, and enable hardware authentication, which are core to ensuring system trustworthiness. UEFI Secure Boot verifies the digital signatures of firmware and operating system boot loaders, preventing unauthorized code from executing during startup. While Secure Boot protects the boot process's integrity, TPM enhances overall platform security through secure key storage, attestation, and encryption capabilities.
Security Benefits: UEFI Secure Boot vs TPM
UEFI Secure Boot enhances system integrity by preventing unauthorized bootloaders and malware from executing during startup through cryptographic signature verification. TPM (Trusted Platform Module) provides hardware-based security by securely storing cryptographic keys and enabling platform integrity measurements, ensuring trusted authentication and encryption. Combining UEFI Secure Boot with TPM strengthens overall security by protecting the boot process and safeguarding sensitive cryptographic operations against firmware and software attacks.
Compatibility and System Requirements
UEFI Secure Boot requires a UEFI firmware interface and support from the operating system, ensuring only trusted software loads during startup, while TPM (Trusted Platform Module) demands a dedicated hardware chip compliant with TPM 1.2 or 2.0 standards for cryptographic operations. Compatibility for Secure Boot is tied to UEFI-enabled motherboards and firmware, limiting use in legacy BIOS systems, whereas TPM can be integrated as a discrete module or embedded in modern CPUs, influencing hardware upgrade needs. System requirements for Secure Boot include enabling UEFI in the BIOS settings and configuring allowed bootloaders, whereas TPM requires compatible hardware and may necessitate BIOS/UEFI activation and corresponding driver support in the OS.
Implementation Challenges
Implementation challenges of UEFI Secure Boot primarily involve compatibility issues with older hardware and the complexity of signing all boot components to maintain a trusted chain, which can lead to boot failures if unsigned or improperly signed software is detected. TPM integration struggles with diverse firmware interfaces and variations in TPM versions, complicating seamless attestation and cryptographic key management across different systems. Both technologies require careful coordination between firmware, OS vendors, and hardware manufacturers to ensure secure, yet flexible, boot processes without compromising system usability.
Use Cases and Scenarios
UEFI Secure Boot ensures that only trusted firmware and operating system loaders signed with verified digital certificates are executed during boot, ideal for protecting systems against bootkits and unauthorized OS modifications in secure corporate environments. TPM (Trusted Platform Module) provides hardware-based cryptographic functions, enabling use cases such as secure key storage, device authentication, and measured boot attestation, critical for enforcing data encryption and integrity in enterprise endpoint security and remote attestation scenarios. Combining UEFI Secure Boot with TPM enhances overall platform trustworthiness by verifying boot components and securely storing cryptographic keys for tasks like BitLocker disk encryption and identity management.
UEFI Secure Boot vs TPM: Which Is Better for Your Needs?
UEFI Secure Boot ensures that only trusted software with valid digital signatures runs during the system startup, preventing rootkits and boot-level malware attacks, while TPM (Trusted Platform Module) provides hardware-based security functions such as key storage, device authentication, and attestation. UEFI Secure Boot is ideal for protecting the boot process and maintaining system integrity, whereas TPM enhances overall device security by supporting cryptographic operations and storing encryption keys securely. Choosing between the two depends on specific security needs: Secure Boot is best for preventing unauthorized code execution at boot time, while TPM offers broader hardware-backed security features for data protection and identity management.
UEFI Secure Boot Infographic
 libterm.com
libterm.com