Sidecar Proxy enhances application performance and security by managing network traffic within a microservices architecture. It operates alongside application processes to offload common networking tasks such as load balancing, encryption, and service discovery. Explore the rest of the article to understand how integrating a Sidecar Proxy can optimize Your cloud-native applications.
Table of Comparison
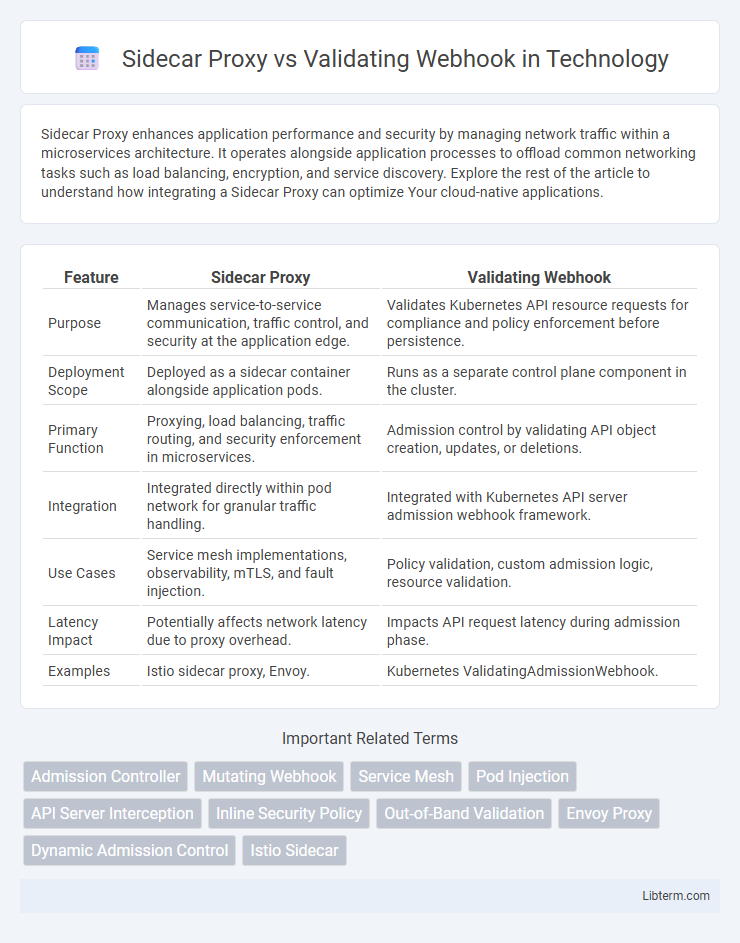
| Feature | Sidecar Proxy | Validating Webhook |
|---|---|---|
| Purpose | Manages service-to-service communication, traffic control, and security at the application edge. | Validates Kubernetes API resource requests for compliance and policy enforcement before persistence. |
| Deployment Scope | Deployed as a sidecar container alongside application pods. | Runs as a separate control plane component in the cluster. |
| Primary Function | Proxying, load balancing, traffic routing, and security enforcement in microservices. | Admission control by validating API object creation, updates, or deletions. |
| Integration | Integrated directly within pod network for granular traffic handling. | Integrated with Kubernetes API server admission webhook framework. |
| Use Cases | Service mesh implementations, observability, mTLS, and fault injection. | Policy validation, custom admission logic, resource validation. |
| Latency Impact | Potentially affects network latency due to proxy overhead. | Impacts API request latency during admission phase. |
| Examples | Istio sidecar proxy, Envoy. | Kubernetes ValidatingAdmissionWebhook. |
Introduction to Sidecar Proxies and Validating Webhooks
Sidecar proxies are deployed alongside application containers to handle network communication, enabling service mesh features like load balancing, traffic routing, and security enforcement without modifying application code. Validating webhooks in Kubernetes serve as admission controllers that intercept API requests to validate and enforce custom policies before resource creation or updates, ensuring cluster integrity. Both mechanisms enhance application reliability and security but operate at different layers: sidecar proxies focus on runtime traffic management, while validating webhooks ensure policy compliance during API request processing.
Core Functionality Comparison
Sidecar Proxy operates at the network level, managing traffic flow and enforcing security policies for microservices through interception and routing of service requests. Validating Webhook functions at the Kubernetes API layer by intercepting and validating resource configuration requests before they are persisted, enforcing policy compliance and custom admission control. Both enhance application reliability and security but target different stages in the request lifecycle--Sidecar Proxy at runtime traffic management and Validating Webhook at deployment-time validation.
Architectural Differences
Sidecar Proxy operates as an independent network proxy deployed alongside application containers, intercepting and managing all incoming and outgoing traffic to enforce policies and enable observability, thus functioning at the network layer. In contrast, a Validating Webhook integrates within the Kubernetes control plane as a dynamically invoked HTTP callback to validate or reject API requests during resource admission, working at the API layer. The architectural difference centers on Sidecar Proxy's decentralized, runtime traffic interception versus the centralized, request-validation role of Validating Webhooks within Kubernetes admission control.
Performance Impact Analysis
Sidecar proxies introduce latency by intercepting and processing all network traffic between microservices, which can lead to increased CPU and memory consumption depending on the proxy's configuration and load. Validating webhooks primarily impact API server performance during resource admission by adding synchronous validation calls, potentially causing request delays when webhook servers experience high latency or downtime. Performance impact of sidecar proxies is usually continuous and scales with traffic volume, whereas validating webhooks impose intermittent overhead tied to specific API requests.
Security Considerations
Sidecar proxies enhance security by enforcing stringent access control and traffic encryption within service meshes, reducing the attack surface through mutual TLS and fine-grained policy enforcement. Validating webhooks provide an additional layer of security by intercepting and validating API requests to enforce compliance and prevent malicious resource configurations before they are persisted. Combining sidecar proxies with validating webhooks strengthens the security posture by ensuring both runtime traffic protection and admission-time policy validation.
Scalability and Resource Utilization
Sidecar proxies offload network functions to dedicated containers, enhancing scalability by distributing traffic management without impacting the main application container's performance. Validating webhooks introduce latency and resource overhead because they rely on synchronous API server calls for admission control, potentially becoming bottlenecks under high request volumes. Efficient resource utilization favors sidecar proxies in dynamic, high-scale environments, whereas validating webhooks suit policy enforcement scenarios with moderate request rates.
Use Cases and Best Fit Scenarios
Sidecar proxy excels in managing service-to-service communication, traffic routing, and observability in microservices architectures, making it ideal for use cases requiring dynamic request control and security enforcement within service meshes like Istio. Validating webhooks are best suited for Kubernetes API request validation, ensuring compliance with custom policies and configuration rules before resource creation or modification. For scenarios demanding real-time traffic management and fine-grained security policies at the application layer, sidecar proxies are the best fit, whereas validating webhooks provide optimal control for admission control and policy validation at the cluster level.
Integration with Kubernetes Workloads
Sidecar proxies integrate closely with Kubernetes workloads by running alongside application containers in the same pod, providing transparent traffic interception, load balancing, and security enforcement without modifying the application code. Validating webhooks operate as admission controllers that intercept API server requests to enforce policies during workload creation or modification, ensuring compliance before the workload is admitted to the cluster. Both mechanisms enhance Kubernetes workload security and governance, with sidecars focusing on runtime network traffic management and webhooks ensuring configuration correctness at deployment time.
Maintenance and Operational Overhead
Sidecar proxies require continuous configuration updates and monitoring to ensure network policies and traffic routing remain effective, increasing operational complexity. Validating webhooks demand regular maintenance to handle schema changes and ensure request validation accuracy, which can introduce latency and failure points. Both approaches necessitate ongoing resource management, but sidecar proxies often incur higher overhead due to their persistent presence alongside application pods.
Decision Criteria for Choosing Between Sidecar Proxy and Validating Webhook
Choosing between a Sidecar Proxy and a Validating Webhook depends on the desired level of traffic interception and policy enforcement granularity; Sidecar Proxies provide dynamic, in-path request handling ideal for fine-grained control and observability, while Validating Webhooks offer lightweight, event-driven admission control within Kubernetes API requests. Performance impact and scalability are critical factors, as Sidecar Proxies introduce runtime overhead by intercepting all network traffic, whereas Validating Webhooks affect only the API server's request validation phase. Security requirements also influence the decision, with Sidecar Proxies enabling continuous security enforcement and mutual TLS, and Validating Webhooks focusing on admission-time policy compliance without ongoing traffic interception.
Sidecar Proxy Infographic
 libterm.com
libterm.com