A Secure Element is a tamper-resistant hardware component designed to securely store sensitive data such as cryptographic keys, payment information, and personal identification. It plays a crucial role in enhancing security for mobile payments, digital identities, and secure communication by isolating critical operations from potential threats. Explore the article to understand how Secure Elements safeguard your digital life and applications.
Table of Comparison
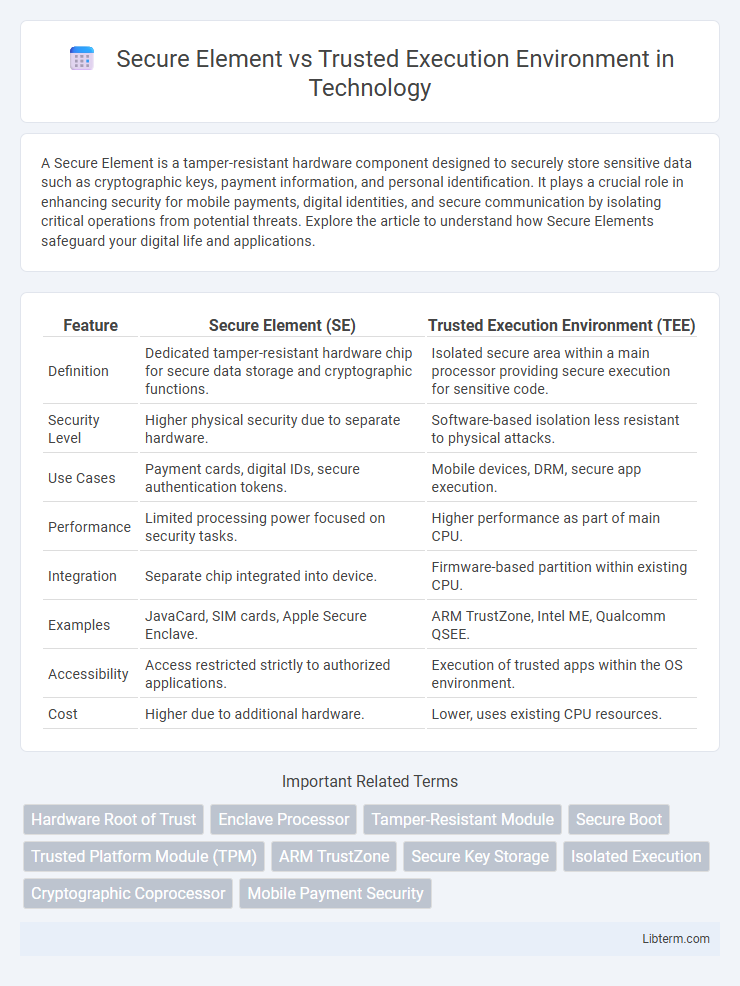
| Feature | Secure Element (SE) | Trusted Execution Environment (TEE) |
|---|---|---|
| Definition | Dedicated tamper-resistant hardware chip for secure data storage and cryptographic functions. | Isolated secure area within a main processor providing secure execution for sensitive code. |
| Security Level | Higher physical security due to separate hardware. | Software-based isolation less resistant to physical attacks. |
| Use Cases | Payment cards, digital IDs, secure authentication tokens. | Mobile devices, DRM, secure app execution. |
| Performance | Limited processing power focused on security tasks. | Higher performance as part of main CPU. |
| Integration | Separate chip integrated into device. | Firmware-based partition within existing CPU. |
| Examples | JavaCard, SIM cards, Apple Secure Enclave. | ARM TrustZone, Intel ME, Qualcomm QSEE. |
| Accessibility | Access restricted strictly to authorized applications. | Execution of trusted apps within the OS environment. |
| Cost | Higher due to additional hardware. | Lower, uses existing CPU resources. |
Introduction to Secure Element and Trusted Execution Environment
Secure Element (SE) is a dedicated, tamper-resistant hardware component designed to securely store cryptographic keys and perform sensitive operations, ensuring enhanced protection against physical and logical attacks. Trusted Execution Environment (TEE) is a secure area within a main processor that guarantees code and data integrity by isolating sensitive processes from the regular operating system. Both SE and TEE play critical roles in mobile security, digital payments, and IoT devices by safeguarding confidential information and enabling trusted computing environments.
Core Principles of Secure Element
Secure Element (SE) operates as a tamper-resistant hardware component designed to securely store cryptographic keys, execute sensitive operations, and protect confidential data independently from the device's main processor. SE's core principles include secure key storage, isolated execution environment, and strict access control mechanisms to prevent unauthorized access and ensure data integrity. Unlike the Trusted Execution Environment (TEE), which relies on a secure area within the main processor, SE provides a physically separate and highly resilient platform against hardware and software attacks.
Core Principles of Trusted Execution Environment
Trusted Execution Environment (TEE) operates as an isolated, secure area within the main processor, enforcing integrity and confidentiality of sensitive code and data by leveraging hardware-based isolation and secure boot processes. Core principles of TEE include secure execution, which ensures code runs within a tamper-resistant environment, and remote attestation, enabling verification of the TEE's trustworthiness to external parties. Secure Element (SE) differs by functioning as a distinct, tamper-resistant chip dedicated to secure storage and cryptographic operations, whereas TEE relies on a partitioned environment within the device's main CPU to protect sensitive computations.
Architectural Differences
Secure Element (SE) is a tamper-resistant hardware chip dedicated to securely storing cryptographic keys and executing sensitive operations isolated from the main processor. Trusted Execution Environment (TEE) operates as a secure area within the main processor, providing an isolated environment that safeguards code and data integrity while sharing some hardware resources with the Rich Execution Environment (REE). SE offers stronger physical security due to its dedicated hardware nature, whereas TEE emphasizes flexibility and performance by leveraging processor extensions and virtualization techniques.
Security Features and Protections
Secure Element (SE) offers dedicated hardware-based isolation with tamper-resistant capabilities designed to securely store cryptographic keys and execute sensitive operations, providing robust protection against physical and logical attacks. Trusted Execution Environment (TEE) provides a secure area within the main processor, enabling isolated execution of trusted applications with enhanced runtime security but shares some hardware resources with the rich OS, which can introduce potential attack vectors. SE typically excels in resistance to sophisticated side-channel attacks and hardware tampering, whereas TEE delivers flexible secure application environments with efficient, hardware-assisted isolation and secure boot features.
Use Cases in Modern Devices
Secure Element (SE) provides isolated hardware-based security for sensitive data storage and cryptographic operations, commonly used in payment systems, SIM cards, and identity verification in smartphones and IoT devices. Trusted Execution Environment (TEE) offers a secure area within the main processor, enabling secure execution of trusted applications like biometric authentication, DRM content protection, and device attestation. Modern devices leverage SE for tamper-resistant storage of payment credentials and TEE for real-time secure application processing, enhancing overall security architecture.
Performance and Resource Considerations
Secure Element (SE) offers dedicated hardware with isolated processing and memory, ensuring high security but limited by constrained computational resources and slower data exchange compared to Trusted Execution Environment (TEE). TEE leverages a secure area within the main processor, providing better performance and faster execution for complex tasks while sharing some system resources with the Rich Execution Environment (REE). Resource-wise, SE is optimized for low power and minimal resource use, suited for simple, critical operations, whereas TEE supports more resource-intensive applications but with increased dependency on the device's main CPU and memory.
Integration and Compatibility
Secure Elements (SE) are tamper-resistant hardware chips designed for strong isolation and secure storage, often integrated as separate components or embedded within devices, ensuring compatibility across diverse platforms and applications through standardized interfaces like ISO 7816 or GlobalPlatform. Trusted Execution Environments (TEE) operate as isolated secure areas within the main processor, offering seamless integration with the device's operating system and enabling direct interaction with apps, but compatibility may vary depending on the SoC manufacturer and OS support, such as ARM TrustZone. While SEs require specific hardware integration, providing robust hardware-level security, TEEs leverage existing processing units for enhanced performance and flexibility, making the choice dependent on device architecture and security requirements.
Challenges and Limitations
Secure Element (SE) faces limitations such as high manufacturing costs, limited storage capacity, and reliance on dedicated hardware, which restricts its scalability and flexibility in diverse applications. Trusted Execution Environment (TEE) encounters challenges including vulnerability to software-based attacks, complexity in integration with existing operating systems, and potential performance overhead due to resource sharing with the main processor. Both SE and TEE struggle with standardization issues and often require tailored security implementations to effectively protect cryptographic keys and sensitive data in increasingly complex threat landscapes.
Choosing Between SE and TEE: Key Factors
Choosing between Secure Element (SE) and Trusted Execution Environment (TEE) depends on factors such as security level, cost, and integration complexity. SE offers hardware-isolated security, ideal for high-value assets like payment credentials, while TEE provides a secure area within the main processor, balancing security and flexibility for applications like DRM and mobile authentication. Evaluating use case requirements, deployment environment, and the need for tamper-proofing guides the optimal choice between SE and TEE.
Secure Element Infographic
 libterm.com
libterm.com