Replay attacks exploit the interception and retransmission of valid data to deceive systems into unauthorized actions, posing a significant threat to network security and communication integrity. Protecting against such attacks involves implementing robust cryptographic protocols, timestamping, and session tokens to ensure message freshness and authenticity. Explore this article to understand how to safeguard your systems against replay attacks effectively.
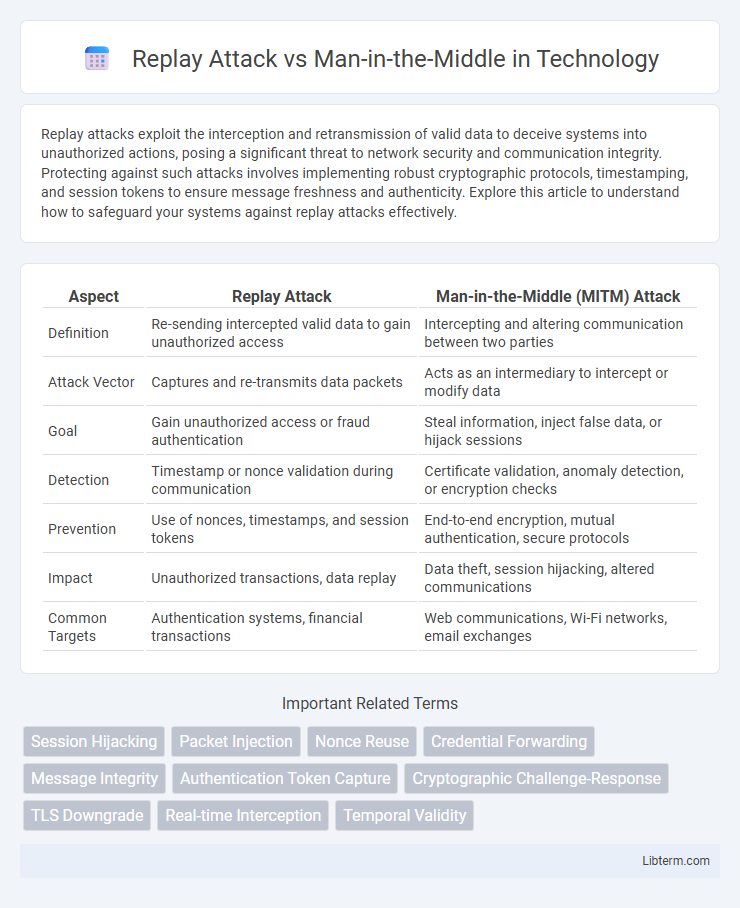
Table of Comparison
| Aspect | Replay Attack | Man-in-the-Middle (MITM) Attack |
|---|---|---|
| Definition | Re-sending intercepted valid data to gain unauthorized access | Intercepting and altering communication between two parties |
| Attack Vector | Captures and re-transmits data packets | Acts as an intermediary to intercept or modify data |
| Goal | Gain unauthorized access or fraud authentication | Steal information, inject false data, or hijack sessions |
| Detection | Timestamp or nonce validation during communication | Certificate validation, anomaly detection, or encryption checks |
| Prevention | Use of nonces, timestamps, and session tokens | End-to-end encryption, mutual authentication, secure protocols |
| Impact | Unauthorized transactions, data replay | Data theft, session hijacking, altered communications |
| Common Targets | Authentication systems, financial transactions | Web communications, Wi-Fi networks, email exchanges |
Understanding Replay Attacks
Replay attacks involve intercepting valid data transmissions and retransmitting them to deceive a system into unauthorized actions, exploiting the absence of proper session validation or timestamping. Unlike man-in-the-middle attacks, which actively intercept and alter communications between parties, replay attacks simply reuse captured data without modification to gain illicit access or privileges. Preventing replay attacks typically requires implementing cryptographic nonce values, timestamps, or challenge-response mechanisms to ensure message freshness and authenticity.
What is a Man-in-the-Middle Attack?
A Man-in-the-Middle (MitM) attack occurs when an attacker secretly intercepts and alters communication between two parties without their knowledge. This type of attack enables the attacker to eavesdrop, steal sensitive data, or inject malicious content by impersonating each party involved. MitM attacks are common in unsecured networks, particularly targeting protocols lacking strong encryption, such as HTTP or unsecured Wi-Fi connections.
Key Differences: Replay vs Man-in-the-Middle
Replay attacks involve the malicious retransmission of valid data to deceive a system, exploiting previously captured communication without altering the original message. Man-in-the-middle (MITM) attacks intercept and manipulate the communication between two parties in real time, allowing the attacker to alter messages or impersonate participants actively. Unlike replay attacks that rely on outdated data, MITM attacks enable dynamic interference, making detection and prevention more complex.
Common Techniques Used in Replay Attacks
Replay attacks commonly exploit the interception and retransmission of valid data packets to deceive authentication systems, often using techniques like packet capture and session hijacking. Attackers utilize network sniffers and tools such as Wireshark to record legitimate communication data, which is then replayed to gain unauthorized access or replicate transactions. These techniques differ from man-in-the-middle attacks, where the intruder actively intercepts and alters communication in real-time rather than merely resending static data.
Methods Employed in Man-in-the-Middle Attacks
Man-in-the-Middle (MitM) attacks utilize techniques such as packet sniffing, session hijacking, and DNS spoofing to intercept and manipulate communications between two parties unnoticed. Attackers often exploit vulnerabilities in Wi-Fi networks or leverage SSL stripping to downgrade secure connections, enabling real-time data interception. Unlike Replay Attacks that resend captured data to gain unauthorized access, MitM attacks actively alter or inject malicious data into the communication stream for control or data theft.
Real-World Examples of Replay Attacks
Replay attacks exploit intercepted data by retransmitting valid authentication messages to gain unauthorized access, as seen in the 2011 RSA SecureID breach where attackers reused stolen tokens to bypass security. In contrast, man-in-the-middle attacks involve an adversary actively intercepting and altering communication, exemplified by the 2013 Target data breach where attackers intercepted payment information between customers and the retailer. Real-world replay attacks often target RFID-enabled systems and wireless networks, such as the 2000 KELOQ car key encryption hack, demonstrating vulnerabilities in outdated cryptographic protocols.
Real-World Examples of Man-in-the-Middle Attacks
Man-in-the-Middle (MitM) attacks involve an attacker secretly intercepting and altering communication between two parties, often seen in scenarios like public Wi-Fi eavesdropping, where hackers capture sensitive data such as login credentials. Replay attacks differ by capturing data transmissions and retransmitting them later to gain unauthorized access, but lack the dynamic interaction seen in MitM attacks. Notable real-world MitM incidents include the 2011 DigiNotar breach, where attackers compromised Certificate Authority systems to issue fraudulent SSL certificates, undermining internet security for millions.
Impact of Replay and MITM Attacks on Data Security
Replay attacks compromise data security by resending captured valid data transmissions, leading to unauthorized access and potential data manipulation without detection. Man-in-the-Middle (MITM) attacks intercept and alter communications between two parties, allowing attackers to steal sensitive information, inject malicious content, or impersonate users. Both attack types undermine confidentiality, integrity, and authenticity, significantly increasing the risk of data breaches and financial loss in digital communication systems.
Prevention Strategies for Replay Attacks
Replay attacks can be prevented using time-stamps, nonces, and session tokens to ensure message uniqueness and freshness, preventing attackers from resubmitting intercepted data. Implementing strong encryption combined with mutual authentication protocols further safeguards against unauthorized message replay. Network monitoring and anomaly detection systems help identify suspicious repeated transmissions, enhancing defense against replay attacks.
Best Practices to Mitigate Man-in-the-Middle Risks
Implementing strong encryption protocols such as TLS 1.3, enforcing mutual authentication with digital certificates, and regularly updating software to patch vulnerabilities are essential best practices to mitigate Man-in-the-Middle (MITM) attack risks. Utilizing secure communication channels, employing Intrusion Detection Systems (IDS), and conducting comprehensive network monitoring further enhance protection against interception and tampering. Educating users on phishing and social engineering threats helps prevent attacker access, complementing technical defenses for robust MITM risk reduction.
Replay Attack Infographic
 libterm.com
libterm.com