Pentesting and bug bounty programs are critical components of modern cybersecurity strategies, helping organizations identify vulnerabilities before attackers do. By actively seeking weaknesses through ethical hacking, these approaches enhance the security posture and protect sensitive data from potential breaches. Discover how incorporating these methods can strengthen Your defenses and why they are essential in today's digital landscape.
Table of Comparison
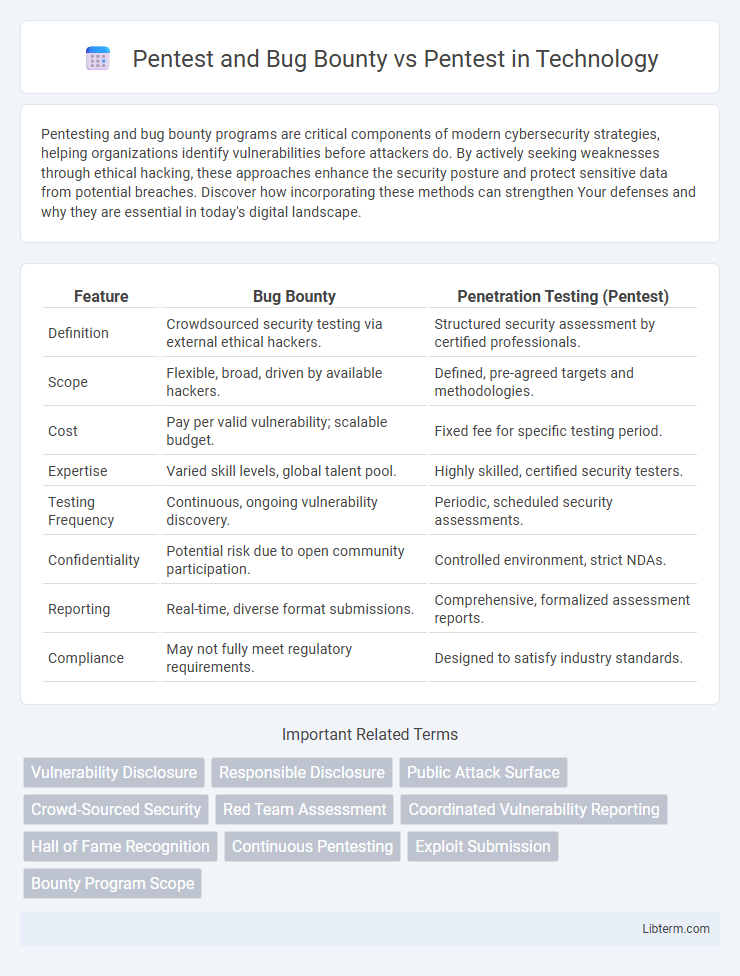
| Feature | Bug Bounty | Penetration Testing (Pentest) |
|---|---|---|
| Definition | Crowdsourced security testing via external ethical hackers. | Structured security assessment by certified professionals. |
| Scope | Flexible, broad, driven by available hackers. | Defined, pre-agreed targets and methodologies. |
| Cost | Pay per valid vulnerability; scalable budget. | Fixed fee for specific testing period. |
| Expertise | Varied skill levels, global talent pool. | Highly skilled, certified security testers. |
| Testing Frequency | Continuous, ongoing vulnerability discovery. | Periodic, scheduled security assessments. |
| Confidentiality | Potential risk due to open community participation. | Controlled environment, strict NDAs. |
| Reporting | Real-time, diverse format submissions. | Comprehensive, formalized assessment reports. |
| Compliance | May not fully meet regulatory requirements. | Designed to satisfy industry standards. |
Introduction to Penetration Testing
Penetration testing involves simulating cyberattacks to identify security vulnerabilities within an organization's systems, networks, or applications, providing a controlled environment to evaluate defenses. Bug bounty programs complement penetration tests by leveraging a diverse community of security researchers who continuously discover and report flaws, often leading to a broader scope and ongoing assessment. Both approaches are essential for proactive cybersecurity, with penetration testing delivering structured, comprehensive evaluations and bug bounties offering dynamic, crowd-sourced vulnerability discovery.
Understanding the Bug Bounty Model
Pentesting involves a controlled, time-limited security assessment conducted by hired experts to identify vulnerabilities, while the bug bounty model leverages a crowdsourced approach, inviting a global community of ethical hackers to find and report security flaws continuously. Understanding the bug bounty model highlights its scalability and diverse attacker mindset coverage, enabling organizations to receive a wider range of vulnerability reports beyond the constraints of traditional pentests. This approach incentivizes ongoing security discovery with monetary rewards, contributing to a dynamic and proactive cybersecurity posture.
Key Differences: Pentest vs Bug Bounty
Pentest involves a structured, time-bound security assessment conducted by certified professionals who follow a predefined scope to identify vulnerabilities, while bug bounty programs leverage a global community of ethical hackers operating asynchronously to find security flaws in live environments. Pentests provide comprehensive, in-depth reports with actionable remediation steps, whereas bug bounty results are often incremental and depend on community participation and the quality of submitted findings. The key difference lies in pentests' controlled, contractual approach versus bug bounty's open, incentive-driven model targeting continuous vulnerability discovery.
Methodologies and Approaches Compared
Pentest focuses on structured, manual testing methodologies using predefined scopes and attack vectors, emphasizing comprehensive vulnerability detection through expert analysis and exploitation techniques. Bug bounty programs leverage crowdsourced security researchers employing diverse, often automated and innovative approaches to identify vulnerabilities across wide-ranging environments. Both methodologies prioritize vulnerability discovery but differ in engagement models, scope flexibility, and the breadth of testing perspectives.
Depth vs Breadth: Scope of Security Assessments
Pentest engagements typically prioritize depth by conducting thorough, focused assessments on specific systems or applications, uncovering deeply embedded vulnerabilities. Bug bounty programs emphasize breadth, harnessing a diverse pool of ethical hackers to explore a wide attack surface across multiple assets, increasing the likelihood of identifying a broader range of security flaws. Balancing pentest depth with bug bounty breadth enhances overall security posture by combining detailed scrutiny with expansive coverage.
Team Composition: In-house Testers vs Crowdsource
Pentest with in-house testers relies on a dedicated team of skilled professionals deeply familiar with the company's infrastructure, enabling focused and consistent vulnerability assessments. Bug bounty programs leverage a diverse, global crowdsource of ethical hackers who bring varied expertise and creative attack methods, increasing the chances of uncovering unique security flaws. Combining both approaches can optimize security by blending structured internal knowledge with external crowdsourced ingenuity.
Budgeting and Cost Considerations
Bug bounty programs offer scalable cost flexibility by paying only for verified vulnerabilities, whereas traditional penetration tests require a fixed budget regardless of findings. Penetration testing incurs upfront expenses that cover a defined scope and timeframe, often making it more predictable but less adaptable to dynamic risk environments. Organizations with constrained budgets may prioritize bug bounty frameworks for ongoing, crowd-sourced vulnerability discovery, while those needing comprehensive, periodic assessments may allocate funds to scheduled penetration tests.
Reporting and Remediation Processes
Pentest and Bug Bounty programs both emphasize identifying vulnerabilities but differ significantly in their reporting and remediation processes. Pentest typically involves structured, formal reports delivered by security experts with detailed vulnerability explanations, risk ratings, and recommended fixes, facilitating direct collaboration with internal teams for immediate remediation. Bug Bounty relies on crowdsourced findings submitted through platforms with triage systems, often requiring validation before developers address bugs, resulting in a variable remediation timeline based on severity and program scope.
Ideal Use Cases for Each Approach
Pentest engagements are ideal for organizations requiring comprehensive security assessments with predefined scopes and timelines, ensuring systematic vulnerability identification and compliance adherence. Bug bounty programs excel when continuous, large-scale crowd-sourced testing is needed to uncover diverse, real-world vulnerabilities beyond traditional pentest limits. Combining both approaches enhances overall security by leveraging controlled in-depth analysis and diverse hacker perspectives.
Choosing the Best Fit for Your Organization
Pentest and Bug Bounty programs both enhance cybersecurity by identifying vulnerabilities but differ in scope and engagement style; pentests provide structured, time-bound assessments led by certified ethical hackers, while bug bounty programs leverage a wider pool of external researchers continuously hunting for flaws. Organizations with fixed budgets and critical compliance requirements often prefer pentests for their thorough, controlled approach, whereas companies seeking ongoing, cost-effective vulnerability discovery may benefit more from bug bounty programs. Selecting the best fit depends on factors like organizational risk tolerance, resource availability, and the desired frequency of security assessments.
Pentest and Bug Bounty Infographic
 libterm.com
libterm.com