The DMZ (Demilitarized Zone) is a secure network segment that acts as a buffer between an organization's internal network and untrusted external networks, such as the internet. It hosts public-facing services like web servers and email servers, ensuring that external users can access these resources without directly interacting with critical internal systems. Discover how implementing a DMZ can enhance Your network security and protect sensitive data by reading the rest of this article.
Table of Comparison
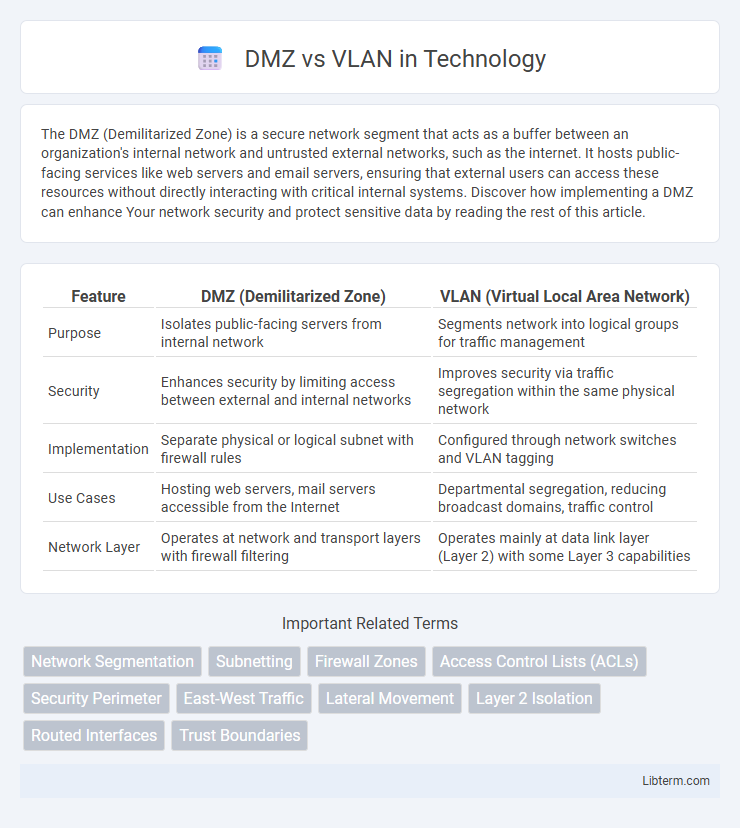
| Feature | DMZ (Demilitarized Zone) | VLAN (Virtual Local Area Network) |
|---|---|---|
| Purpose | Isolates public-facing servers from internal network | Segments network into logical groups for traffic management |
| Security | Enhances security by limiting access between external and internal networks | Improves security via traffic segregation within the same physical network |
| Implementation | Separate physical or logical subnet with firewall rules | Configured through network switches and VLAN tagging |
| Use Cases | Hosting web servers, mail servers accessible from the Internet | Departmental segregation, reducing broadcast domains, traffic control |
| Network Layer | Operates at network and transport layers with firewall filtering | Operates mainly at data link layer (Layer 2) with some Layer 3 capabilities |
Introduction to DMZ and VLAN
A Demilitarized Zone (DMZ) is a physical or logical subnetwork that separates an internal local area network (LAN) from untrusted external networks, providing an additional layer of security by isolating public-facing services. A Virtual Local Area Network (VLAN) segments network traffic logically within the same physical network, improving network management, reducing broadcast traffic, and enhancing security by isolating sensitive data flows. Both DMZs and VLANs are essential for network architecture, offering distinct methods of controlling access and protecting critical resources.
Core Concepts: What is a DMZ?
A DMZ (Demilitarized Zone) is a physical or logical subnet that separates an internal local area network (LAN) from untrusted external networks, typically the internet, to enhance security by isolating public-facing services. It allows external users to access certain resources, such as web servers or mail servers, without exposing the entire internal network. The core concept of a DMZ is to provide a controlled buffer zone that limits the risk of direct attacks on internal systems while maintaining necessary accessibility.
Core Concepts: What is a VLAN?
A VLAN (Virtual Local Area Network) segments a physical network into multiple logical networks, enhancing security and traffic management by isolating devices within the same broadcast domain. It enables network administrators to group users and resources regardless of physical location, optimizing performance and reducing congestion. VLANs function at Layer 2 of the OSI model, using tags defined by the IEEE 802.1Q standard to identify and separate traffic streams.
Key Differences Between DMZ and VLAN
A DMZ (Demilitarized Zone) is a physical or logical subnet that separates an internal network from untrusted external networks, providing an additional layer of security by isolating public-facing services such as web servers. A VLAN (Virtual Local Area Network) is a network segmentation technology that creates distinct broadcast domains within a single physical network, improving performance and security by isolating traffic at the data link layer. The key difference lies in their primary purpose: DMZs focus on external threat containment and controlled access to public services, while VLANs primarily organize and segment internal network traffic.
Use Cases: When to Use a DMZ
A DMZ (Demilitarized Zone) is ideal for hosting public-facing services such as web servers, email servers, and FTP servers that require controlled external access while protecting the internal network. VLANs (Virtual Local Area Networks) segment network traffic within an organization to isolate departments or improve security but do not inherently provide a barrier to external threats. Use a DMZ when you need to expose services to the internet securely, enabling strict access controls and monitoring between untrusted and trusted zones.
Use Cases: When to Use a VLAN
VLANs (Virtual Local Area Networks) are ideal for segmenting network traffic within an organization to enhance security, improve performance, and simplify management by isolating departments or user groups. Use VLANs when you need to control broadcast domains, enforce access policies at a granular level, or separate sensitive data flows without physical network changes. They are particularly effective in office environments for separating voice, data, and guest traffic, reducing network congestion and minimizing the risk of unauthorized access.
Security Implications: DMZ vs VLAN
A DMZ (Demilitarized Zone) provides a physical or logical subnet that isolates external-facing services from the internal network, reducing the risk of external attacks reaching critical systems. VLANs (Virtual Local Area Networks) segment network traffic within a single physical infrastructure, enabling policy-based access control but are susceptible to VLAN hopping attacks if not properly configured. Implementing a DMZ enhances security by creating a distinct security boundary, whereas VLANs offer flexible traffic segregation with less isolation, making DMZs more effective for protecting sensitive data and services from external threats.
Network Segmentation: DMZ vs VLAN
Network segmentation using DMZs and VLANs serves distinct security and organizational purposes; a DMZ (Demilitarized Zone) creates a physically or logically separated buffer zone between an internal network and external networks, typically hosting public-facing servers to limit external access to sensitive internal resources. VLANs (Virtual Local Area Networks) segment a single physical network into multiple isolated broadcast domains, improving network efficiency, managing traffic, and enhancing security by restricting communication between different VLANs without additional routing. While DMZs emphasize external threat mitigation by isolating internet-facing services, VLANs focus on internal traffic management and containment within an organization's infrastructure.
Performance and Management Considerations
DMZ (Demilitarized Zone) segments external-facing services to enhance security by isolating them from the internal network, potentially introducing latency due to traffic filtering and inspection. VLANs (Virtual Local Area Networks) optimize performance by logically segmenting networks within the same physical infrastructure, reducing broadcast domains and improving traffic management. In terms of management, DMZs require strict policy enforcement and dedicated security controls, while VLANs offer flexible network segmentation but necessitate careful configuration to prevent inter-VLAN routing vulnerabilities.
Choosing the Right Solution: DMZ or VLAN
Choosing between a DMZ and VLAN depends on the specific security requirements and network architecture. A DMZ provides a secured buffer zone for exposing services to the internet, isolating public-facing servers to prevent direct access to the internal network. VLANs offer segmented network traffic within the internal environment, enhancing performance and internal security but are not designed for exposing services to untrusted external networks.
DMZ Infographic
 libterm.com
libterm.com