Tampering refers to the unauthorized alteration or interference with a product, device, or data, compromising its integrity and safety. It can lead to significant security risks, financial losses, and legal consequences, especially in industries like pharmaceuticals, electronics, and logistics. Explore the rest of the article to understand how tampering impacts your security and ways to effectively prevent it.
Table of Comparison
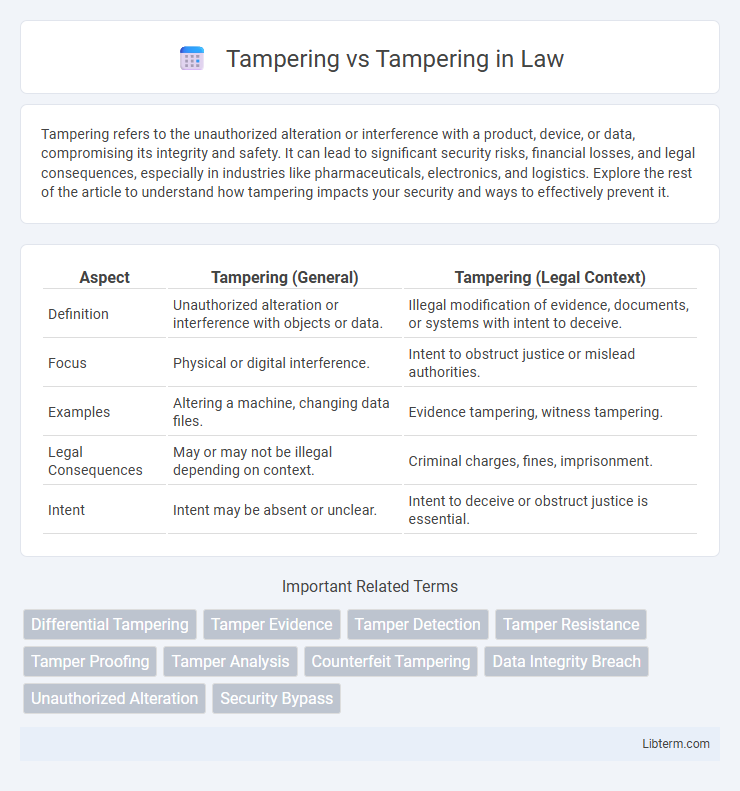
| Aspect | Tampering (General) | Tampering (Legal Context) |
|---|---|---|
| Definition | Unauthorized alteration or interference with objects or data. | Illegal modification of evidence, documents, or systems with intent to deceive. |
| Focus | Physical or digital interference. | Intent to obstruct justice or mislead authorities. |
| Examples | Altering a machine, changing data files. | Evidence tampering, witness tampering. |
| Legal Consequences | May or may not be illegal depending on context. | Criminal charges, fines, imprisonment. |
| Intent | Intent may be absent or unclear. | Intent to deceive or obstruct justice is essential. |
Introduction to Tampering: Definitions and Context
Tampering involves unauthorized alteration or manipulation of data, devices, or systems to gain illicit advantage, often compromising security and integrity. In cybersecurity, tampering refers to actions such as modifying software code or intercepting communications to evade detection or corrupt information flow. Understanding tampering's various forms and contexts is crucial for developing effective prevention and detection strategies within digital and physical environments.
Types of Tampering: Physical vs Digital
Tampering can be categorized into physical and digital types, each involving distinct methods and targets. Physical tampering involves unauthorized physical access or manipulation of devices, such as opening hardware enclosures or altering circuit boards, aiming to disrupt or steal data. Digital tampering refers to unauthorized modifications within software or data, including hacking, malware insertion, or altering digital records, impacting data integrity and system security.
Legal Implications of Tampering
Tampering, defined as the unauthorized alteration or interference with objects, documents, or systems, carries significant legal implications across various contexts, including evidence tampering in criminal cases and product tampering in consumer protection laws. Legal consequences often involve severe penalties such as fines, imprisonment, and civil liabilities, emphasizing the protection of integrity and trust in judicial and commercial systems. Courts strictly enforce tampering statutes to preserve fair trial rights, ensure public safety, and uphold regulatory compliance.
Tampering in Sports: Cheating and Integrity
Tampering in sports involves unauthorized interference with athletes, coaches, or team personnel to gain an unfair competitive advantage, often manifesting as illegal recruitment or contract negotiations without consent. Such actions undermine the integrity of competitions and violate league regulations designed to ensure fair play. Strict penalties and monitoring systems are enforced by sports governing bodies to deter tampering and uphold ethical standards within professional and amateur sports.
Tampering in Technology: Software and Hardware Risks
Tampering in technology refers to unauthorized modifications made to software or hardware components, posing significant security risks by compromising system integrity and confidentiality. Software tampering can involve code injection, malware insertion, or altering program logic, leading to vulnerabilities such as data breaches or system failures. Hardware tampering includes physical manipulation of devices, such as chip modification or interception of communication signals, which threatens device authenticity and operational reliability.
Detecting and Preventing Tampering
Detecting tampering involves monitoring data integrity through hash functions, digital signatures, and anomaly detection systems that identify unauthorized modifications in files or communication channels. Preventing tampering requires implementing robust encryption protocols, access controls, and secure hardware solutions such as Trusted Platform Modules (TPMs) to safeguard against unauthorized data alteration. Combining real-time auditing with tamper-evident technologies enhances the overall security posture by ensuring prompt identification and mitigation of tampering attempts.
Tampering vs Evidence Tampering: Key Differences
Tampering involves unauthorized interference with any object or system, while evidence tampering specifically refers to altering, destroying, or concealing evidence related to investigations or legal proceedings. Evidence tampering obstructs justice by compromising the integrity of proof, often resulting in harsher legal consequences than general tampering offenses. Understanding the distinction is critical for law enforcement and legal professionals in identifying and prosecuting crimes accurately.
Real-World Examples of Tampering Cases
Tampering involves unauthorized alteration or interference with data, products, or systems, often seen in cases such as election tampering, where hackers manipulate voting machines to alter results. Food tampering is another prevalent example, involving the deliberate contamination of consumer goods to cause harm or fear, as witnessed in several high-profile product recalls. Industrial tampering includes sabotage of machinery or infrastructure, exemplified by incidents of pipeline tampering that result in environmental damage and service disruptions.
Impact of Tampering on Trust and Security
Tampering undermines the integrity of data and systems by introducing unauthorized alterations, leading to compromised trust between users and platforms. The impact of tampering on security manifests through vulnerabilities that attackers exploit, resulting in data breaches, fraud, and loss of sensitive information. Ensuring robust tamper-detection mechanisms is critical to maintaining trust and safeguarding cybersecurity infrastructure.
Future of Tampering: Trends and Innovations
Future trends in tampering highlight advancements in sensor technology and AI-powered detection systems enhancing anti-tamper measures. Innovations in blockchain and cryptographic authentication provide robust safeguards against unauthorized alterations in digital and physical assets. Increased integration of IoT devices with real-time monitoring analytics promises proactive tampering prevention across industries such as manufacturing, supply chain, and cybersecurity.
Tampering Infographic
 libterm.com
libterm.com