Non-state-sponsored activities often involve cyberattacks, misinformation campaigns, or other actions carried out without direct government backing. These operations can significantly impact national security, economic stability, and individual privacy. Discover how understanding the mechanisms behind non-state-sponsored threats can protect your digital environment by reading the full article.
Table of Comparison
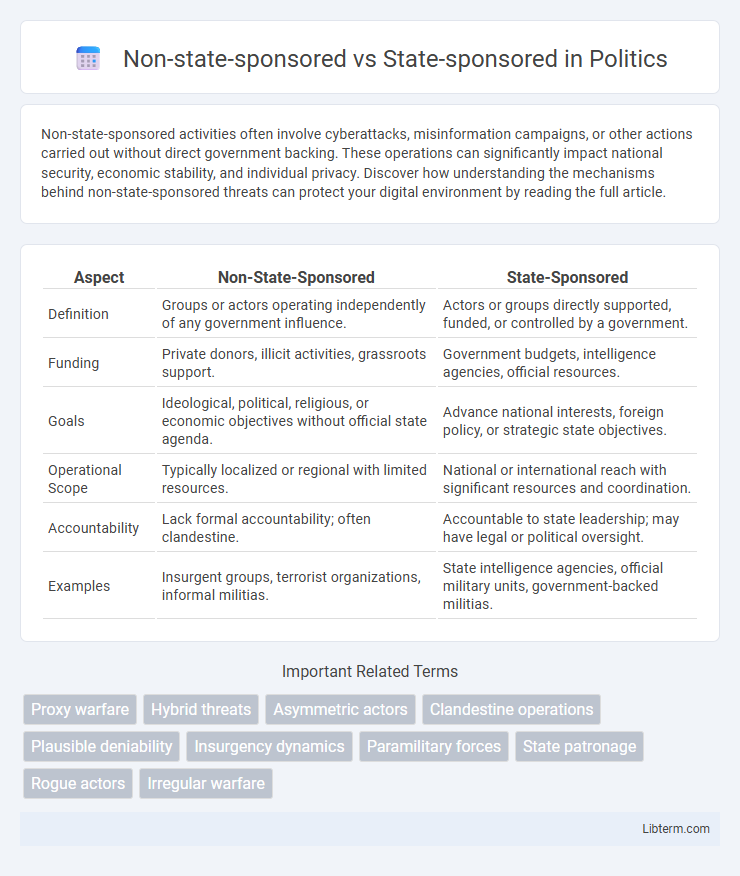
| Aspect | Non-State-Sponsored | State-Sponsored |
|---|---|---|
| Definition | Groups or actors operating independently of any government influence. | Actors or groups directly supported, funded, or controlled by a government. |
| Funding | Private donors, illicit activities, grassroots support. | Government budgets, intelligence agencies, official resources. |
| Goals | Ideological, political, religious, or economic objectives without official state agenda. | Advance national interests, foreign policy, or strategic state objectives. |
| Operational Scope | Typically localized or regional with limited resources. | National or international reach with significant resources and coordination. |
| Accountability | Lack formal accountability; often clandestine. | Accountable to state leadership; may have legal or political oversight. |
| Examples | Insurgent groups, terrorist organizations, informal militias. | State intelligence agencies, official military units, government-backed militias. |
Defining Non-State-Sponsored and State-Sponsored Entities
Non-state-sponsored entities operate independently from direct government control, often including hacktivist groups, criminal organizations, and private individuals pursuing their own agendas. State-sponsored entities receive funding, resources, and strategic direction from government agencies to conduct cyber espionage, information warfare, or infrastructure disruption aligned with national interests. Distinguishing factors include attribution complexity, resource availability, and geopolitical motivations driving the attacks or activities.
Key Differences Between State and Non-State Sponsorship
State-sponsored groups receive direct financial, logistical, and intelligence support from government entities, enabling sophisticated cyberattacks and geopolitical influence operations. Non-state-sponsored actors operate independently or as part of decentralized networks, often motivated by ideological, financial, or personal agendas without official state backing. Key differences include the scale of resources, strategic objectives aligned with national interests, and the level of operational coordination provided by state actors versus the typically opportunistic and fragmented nature of non-state groups.
Historical Context of State and Non-State Actors
State-sponsored actors have historically wielded organized resources and political power, often engaging in cyber espionage or warfare to advance national interests during geopolitical conflicts such as the Cold War. Non-state-sponsored actors, including hacktivist groups and cybercriminal organizations, emerged prominently in the late 20th century, exploiting technological advances for ideological, financial, or disruptive purposes without direct government backing. The evolving cyber threat landscape reflects this historical divide, where state actors pursue strategic dominance and non-state actors focus on opportunistic or cause-driven attacks.
Motivations Behind State and Non-State Sponsorship
State-sponsored cyberattacks are primarily motivated by geopolitical objectives, including espionage, national security, and economic advantage, leveraging government resources and intelligence agencies to achieve strategic goals. Non-state-sponsored attacks often stem from financial gain, ideological agendas, or cybercrime, exploiting vulnerabilities without direct government backing or political directives. Understanding these motivations is crucial for developing tailored cybersecurity defenses that address the distinct tactics and targets of both state and non-state actors.
Methods and Tactics Used by State vs. Non-State Actors
State-sponsored actors often employ sophisticated cyber warfare techniques, including advanced persistent threats (APTs), zero-day exploits, and extensive espionage operations backed by significant resources and intelligence infrastructure. Non-state actors typically utilize opportunistic methods such as phishing, ransomware, and hacktivism, relying on readily available tools and social engineering tactics rather than long-term infiltration. While state-sponsored groups emphasize stealth, persistence, and strategic targeting, non-state actors prioritize speed, disruption, and exploiting public vulnerabilities.
Impact on International Security and Policy
Non-state-sponsored actors such as terrorist groups and organized crime networks often exploit transnational vulnerabilities, challenging international security through asymmetric tactics and decentralized operations that complicate state responses. State-sponsored entities benefit from governmental resources, enabling sophisticated cyber-attacks, espionage, and proxy conflicts that can destabilize regions and influence global geopolitics. International policy frameworks increasingly prioritize distinguishing these threats to deploy targeted countermeasures and enhance cooperative intelligence-sharing among nations.
Case Studies of State-Sponsored Activities
State-sponsored cyber activities often involve sophisticated attacks linked to nation-states such as Russia's alleged interference in the 2016 U.S. elections and China's extensive cyber-espionage campaigns targeting intellectual property in the technology sector. Case studies reveal state-sponsored operations like North Korea's Lazarus Group executing financially motivated cyberattacks to fund government projects, contrasting with the typically less resourced non-state actors. These state-sponsored campaigns leverage advanced persistent threats (APTs) with strategic geopolitical objectives, distinguishing them from non-state-sponsored attacks driven by ideological, financial, or personal motives.
Case Studies of Non-State-Sponsored Activities
Non-state-sponsored cyber activities often involve hacktivist groups, criminal organizations, and independent hackers targeting financial institutions, critical infrastructure, and government databases without direct government backing. Case studies such as the 2017 WannaCry ransomware attack, attributed to North Korean-affiliated non-state actors, demonstrate the significant disruption non-state groups can inflict on global systems. These operations contrast with state-sponsored campaigns by lacking official government resources but can still leverage sophisticated tactics to achieve political or financial objectives.
Challenges in Attribution and Identification
Non-state-sponsored cyberattacks pose significant challenges in attribution due to the use of anonymizing technologies and decentralized operational structures, complicating efforts to trace activity back to individual actors. State-sponsored attacks leverage sophisticated tactics, including false-flag operations and advanced persistent threats (APTs), which blur attribution by mimicking other groups or nations. The overlapping methods employed by both non-state and state actors hinder clear identification, requiring enhanced forensic techniques and international collaboration for accurate cyber threat attribution.
Future Trends and Evolving Threats
State-sponsored cyber threats are projected to advance with increased resource allocation and sophisticated tactics such as AI-driven espionage and infrastructure sabotage, posing significant risks to national security and global stability. Non-state-sponsored actors, including hacktivists and cybercriminal groups, are likely to exploit emerging vulnerabilities in IoT and cloud platforms, leveraging ransomware and data exfiltration to maximize financial gain and disruption. The evolving cyber threat landscape will demand enhanced collaboration between governments and private sectors to develop adaptive defense mechanisms and real-time threat intelligence sharing.
Non-state-sponsored Infographic
 libterm.com
libterm.com