Asymmetric designs break conventional balance by favoring one side, creating visual interest and dynamic appeal that enhances modern aesthetics. This approach challenges symmetry, offering unique compositions that stand out in art, architecture, and fashion. Explore the full article to discover how asymmetric elements can transform Your creative projects.
Table of Comparison
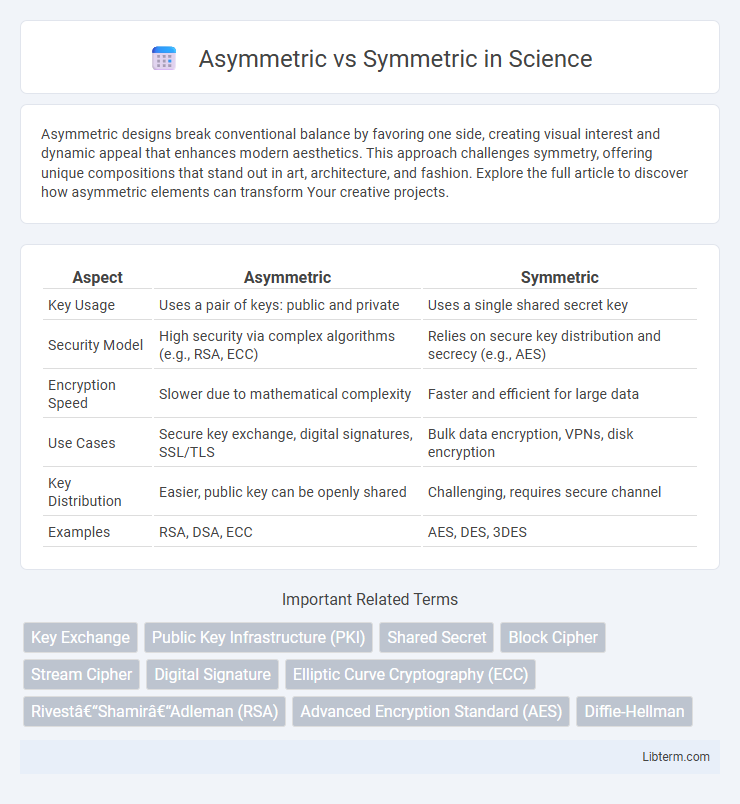
| Aspect | Asymmetric | Symmetric |
|---|---|---|
| Key Usage | Uses a pair of keys: public and private | Uses a single shared secret key |
| Security Model | High security via complex algorithms (e.g., RSA, ECC) | Relies on secure key distribution and secrecy (e.g., AES) |
| Encryption Speed | Slower due to mathematical complexity | Faster and efficient for large data |
| Use Cases | Secure key exchange, digital signatures, SSL/TLS | Bulk data encryption, VPNs, disk encryption |
| Key Distribution | Easier, public key can be openly shared | Challenging, requires secure channel |
| Examples | RSA, DSA, ECC | AES, DES, 3DES |
Understanding Asymmetric and Symmetric Encryption
Asymmetric encryption uses a pair of keys--public and private--to encrypt and decrypt data, ensuring secure communication by allowing the public key to encrypt information while only the private key can decrypt it. Symmetric encryption relies on a single shared secret key for both encryption and decryption, offering faster processing but requiring secure key distribution between parties. Understanding the differences highlights asymmetric encryption's strength in secure key exchange and digital signatures, whereas symmetric encryption excels in bulk data encryption due to its efficiency.
Key Differences Between Asymmetric and Symmetric Encryption
Asymmetric encryption uses a pair of keys--a public key for encryption and a private key for decryption--providing enhanced security for data exchange, while symmetric encryption relies on a single shared key for both encryption and decryption, resulting in faster processing speeds. Key differences include asymmetric encryption's suitability for secure key exchange and digital signatures, contrasted with symmetric encryption's efficiency in encrypting large data volumes. The complexity and computational overhead in asymmetric algorithms such as RSA differ significantly from the simpler and faster symmetric algorithms like AES.
How Asymmetric Encryption Works
Asymmetric encryption uses a pair of keys--public and private--to secure data, where the public key encrypts information and only the corresponding private key can decrypt it. This method relies on complex mathematical algorithms such as RSA or ECC to generate key pairs, ensuring that even if the public key is widely distributed, only the private key holder can access the encrypted content. Asymmetric encryption provides enhanced security for data exchange, digital signatures, and authentication processes by eliminating the need to share secret keys.
How Symmetric Encryption Works
Symmetric encryption uses a single secret key for both encryption and decryption, enhancing speed and efficiency in securing data. The sender and receiver must share the same key, which is used to transform plaintext into ciphertext through algorithms like AES or DES. This method is ideal for encrypting large amounts of data quickly but requires secure key distribution to prevent unauthorized access.
Advantages of Asymmetric Encryption
Asymmetric encryption offers enhanced security by using a pair of keys--public and private--eliminating the need to share secret keys over insecure channels. It enables secure key exchange, digital signatures, and non-repudiation, making it ideal for secure communications and authentication. Unlike symmetric encryption, asymmetric methods provide better scalability and manageability in multi-user environments.
Advantages of Symmetric Encryption
Symmetric encryption offers significant advantages such as faster encryption and decryption processes due to simpler algorithms, making it ideal for processing large volumes of data efficiently. It requires only one key for both encryption and decryption, simplifying key management in controlled environments. This method is widely used in applications like database encryption, file storage, and VPNs where performance and speed are critical.
Disadvantages of Asymmetric Encryption
Asymmetric encryption involves complex mathematical algorithms that require significantly more computational power than symmetric encryption, leading to slower performance and higher latency in data processing. The key management is also more challenging due to the necessity of maintaining both public and private keys securely, increasing the risk of key compromise. Additionally, asymmetric encryption typically produces larger ciphertext sizes, consuming more bandwidth and storage resources compared to symmetric methods.
Disadvantages of Symmetric Encryption
Symmetric encryption suffers from key distribution challenges, as both sender and receiver must securely share the same secret key, increasing the risk of interception. The use of a single key for both encryption and decryption makes it vulnerable to key compromise, which can expose all transmitted data. Scalability is limited in large networks because each pair of users requires a unique key, complicating key management and increasing overhead.
Comparing Use Cases: Asymmetric vs Symmetric
Symmetric encryption excels in environments requiring fast, efficient data transmission, such as encrypting large volumes of stored data or streaming content, due to its use of a single shared key. Asymmetric encryption is ideal for secure key exchange, digital signatures, and authentication processes, leveraging a public-private key pair to enhance security in communication channels like email or SSL/TLS protocols. Organizations often combine both by using asymmetric encryption to securely share symmetric keys, optimizing performance while maintaining robust security in hybrid cryptographic systems.
Which Encryption Method Should You Choose?
Symmetric encryption uses a single key for both encryption and decryption, making it faster and more efficient for handling large volumes of data, while asymmetric encryption employs a pair of public and private keys, enhancing security in key exchange and authentication processes. Choosing between symmetric and asymmetric encryption depends on the specific needs: symmetric is ideal for speed and performance in internal data protection, whereas asymmetric is preferred for secure communications, key distribution, and establishing trust in network environments. Combining both methods in hybrid encryption systems often provides the best balance between security and efficiency.
Asymmetric Infographic
 libterm.com
libterm.com