Resource Owner Password Credentials Flow allows users to obtain access tokens by directly providing their username and password to the client application, streamlining authentication in trusted environments. This flow is especially useful when other OAuth 2.0 flows are not feasible, but it requires high trust between the user and the client due to the sensitive nature of credentials. Explore the rest of the article to understand how to implement this flow securely and when it is appropriate for your application.
Table of Comparison
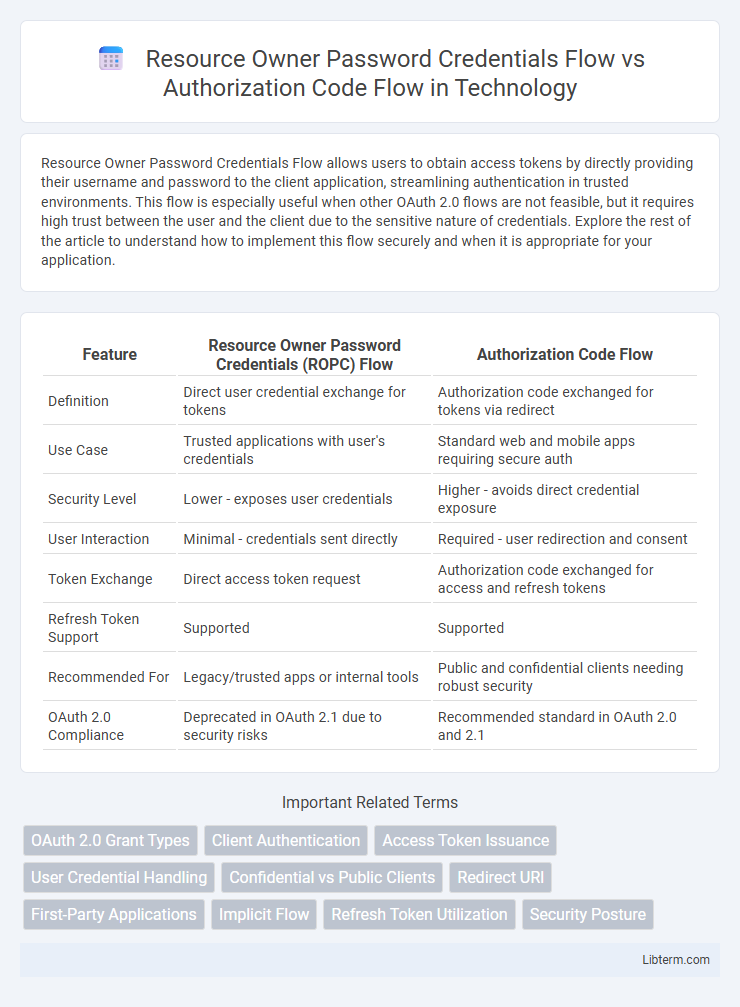
| Feature | Resource Owner Password Credentials (ROPC) Flow | Authorization Code Flow |
|---|---|---|
| Definition | Direct user credential exchange for tokens | Authorization code exchanged for tokens via redirect |
| Use Case | Trusted applications with user's credentials | Standard web and mobile apps requiring secure auth |
| Security Level | Lower - exposes user credentials | Higher - avoids direct credential exposure |
| User Interaction | Minimal - credentials sent directly | Required - user redirection and consent |
| Token Exchange | Direct access token request | Authorization code exchanged for access and refresh tokens |
| Refresh Token Support | Supported | Supported |
| Recommended For | Legacy/trusted apps or internal tools | Public and confidential clients needing robust security |
| OAuth 2.0 Compliance | Deprecated in OAuth 2.1 due to security risks | Recommended standard in OAuth 2.0 and 2.1 |
Introduction to OAuth 2.0 Grant Types
OAuth 2.0 grant types define methods for obtaining access tokens, essential for securing API access. The Resource Owner Password Credentials (ROPC) flow involves exchanging user credentials directly for tokens, suitable for highly trusted applications but less secure due to credential exposure. The Authorization Code flow offers enhanced security by using an intermediary authorization code and redirect URIs, ideal for web and mobile applications requiring user authentication through third-party providers.
Overview of Resource Owner Password Credentials Flow
Resource Owner Password Credentials Flow enables users to provide their username and password directly to the client application, which exchanges these credentials for an access token from the authorization server. This flow is typically used in highly trusted applications because it involves exposing user credentials to the client, raising security risks. Unlike the Authorization Code Flow, which redirects users to an authorization server for authentication, the Resource Owner Password Credentials Flow bypasses this step, simplifying token acquisition but limiting support for multi-factor authentication and federated identity providers.
Overview of Authorization Code Flow
Authorization Code Flow is an OAuth 2.0 authorization framework designed for confidential and public clients, providing enhanced security by exchanging an authorization code for an access token. This flow involves redirection-based user authentication, where the client receives an authorization code after the user approves access, minimizing exposure of client credentials. It is widely recommended for web applications and mobile apps due to its robust protection against token interception and replay attacks.
Key Differences Between the Two Flows
Resource Owner Password Credentials Flow involves the user directly providing their username and password to the client application, which then exchanges these credentials for an access token, making it suitable only for highly trusted clients. Authorization Code Flow, by contrast, redirects the user to the authorization server to authenticate and grant consent, providing an authorization code that the client exchanges for tokens, enhancing security by not exposing user credentials to the client. Key differences include the level of user credential exposure, suitability for various client types, and the inherent security measures protecting token exchange and user authentication.
Security Implications and Best Practices
Resource Owner Password Credentials (ROPC) Flow presents significant security risks due to direct handling of user credentials by the client application, increasing exposure to phishing and credential leakage. Authorization Code Flow enhances security by delegating authentication to the authorization server, using an authorization code exchanged for tokens, thus minimizing exposure to sensitive data. Best practices recommend using Authorization Code Flow with Proof Key for Code Exchange (PKCE) for public clients and avoiding ROPC except in highly trusted applications.
Use Cases for Resource Owner Password Credentials Flow
Resource Owner Password Credentials Flow is best suited for trusted applications where users directly provide their credentials, such as legacy systems or internal corporate apps requiring seamless access without redirecting to an authorization server. It enables quick authentication by exchanging user credentials for tokens, often used in scenarios with limited UI or automation scripts. This flow is not recommended for public clients or third-party applications due to security concerns and the risk of exposing user credentials.
Use Cases for Authorization Code Flow
Authorization Code Flow is ideal for applications requiring enhanced security, such as web and mobile apps that access sensitive user data through APIs. It supports confidential clients by exchanging an authorization code for tokens via a secure back-channel, minimizing exposure of access credentials. This flow is preferred when requiring user consent, multi-factor authentication, and compliance with OAuth 2.0 best practices for secure authorization.
Advantages and Disadvantages Comparison
Resource Owner Password Credentials Flow allows users to exchange their credentials directly for tokens, offering simplicity and suitability for trusted applications but risks exposing sensitive information and lacks support for multi-factor authentication. Authorization Code Flow enhances security by using an intermediate code and redirect URIs, minimizing token exposure and supporting confidential clients, but requires more complex implementation and user-agent interaction. While Resource Owner Password Credentials Flow might suffice for legacy or highly trusted environments, Authorization Code Flow remains the recommended standard for secure, scalable OAuth 2.0 authorization.
Choosing the Right Flow for Your Application
Choosing the right OAuth 2.0 flow depends on your application's security needs and user experience. Resource Owner Password Credentials Flow is suitable for trusted applications where users directly input credentials, but it's less secure due to direct handling of passwords. Authorization Code Flow enhances security by exchanging authorization codes for tokens on a backend server, ideal for web and mobile apps requiring strong authentication and minimal exposure of sensitive data.
Conclusion and Recommendations
Resource Owner Password Credentials Flow is less secure due to direct handling of user credentials and is suitable only for highly trusted applications. Authorization Code Flow offers enhanced security by exchanging authorization codes instead of credentials, making it the recommended choice for most web and mobile applications. Implement Authorization Code Flow with PKCE to protect user data and comply with modern OAuth 2.0 security standards.
Resource Owner Password Credentials Flow Infographic
 libterm.com
libterm.com